How medical device companies can safeguard
... The IP Commission estimates that China is responsible for 50-80% of international IP theft, and is the No. 1 perpetrator of cyber attacks designed to steal IP. One reason is that China’s industrial policy goals encourage IP theft, and an extraordinary number of Chinese business and government entiti ...
... The IP Commission estimates that China is responsible for 50-80% of international IP theft, and is the No. 1 perpetrator of cyber attacks designed to steal IP. One reason is that China’s industrial policy goals encourage IP theft, and an extraordinary number of Chinese business and government entiti ...
D efe ns iv
... sophisticated backdoor techniques. Students will depart this course with an understanding of advanced techniques used by the most sophisticated attackers to maintain stealth and security while minimizing their footprint and identity. Locating the Cyber Ninja ...
... sophisticated backdoor techniques. Students will depart this course with an understanding of advanced techniques used by the most sophisticated attackers to maintain stealth and security while minimizing their footprint and identity. Locating the Cyber Ninja ...
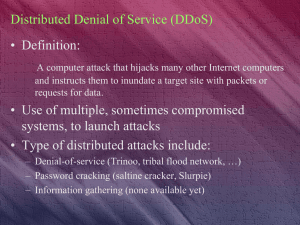
Distributed Denial of Service (DDoS)
... A computer attack that hijacks many other Internet computers and instructs them to inundate a target site with packets or requests for data. ...
... A computer attack that hijacks many other Internet computers and instructs them to inundate a target site with packets or requests for data. ...
Darktrace Case Study: Human Longevity, Medical Technology
... Thanks to the Enterprise Immune System, Human Longevity is now benefitting from real-time threat detection and increased confidence in its cyber defense strategy’s capabilities, having integrated Darktrace with the company’s existing security solutions. Without having to change the nature of its net ...
... Thanks to the Enterprise Immune System, Human Longevity is now benefitting from real-time threat detection and increased confidence in its cyber defense strategy’s capabilities, having integrated Darktrace with the company’s existing security solutions. Without having to change the nature of its net ...
Incident Response: Six Steps for Managing Cyber Breaches
... At first, hacking was merely a pastime for computer-savvy individuals seeking to challenge their skill sets and knowledge. But those days are long over. While the majority of attacks are considered opportunistic – meaning the attacker did not intentionally target the victim -- nowadays, financial, e ...
... At first, hacking was merely a pastime for computer-savvy individuals seeking to challenge their skill sets and knowledge. But those days are long over. While the majority of attacks are considered opportunistic – meaning the attacker did not intentionally target the victim -- nowadays, financial, e ...
FEARLESS - Cyber Security Research and Education Institute
... Data Privacy, Secure Web Services, Secure Cloud Computing, Hardware Security, CISSP Modules ...
... Data Privacy, Secure Web Services, Secure Cloud Computing, Hardware Security, CISSP Modules ...
45.3% of employees are aware that their workplace can be
... In this survey, we saw a disparity in the level of awareness between system admins and general employees, which suggests that companies should reexamine how they educate and share security-related information to their employees. Compared to the previous year, security measures against targeted attac ...
... In this survey, we saw a disparity in the level of awareness between system admins and general employees, which suggests that companies should reexamine how they educate and share security-related information to their employees. Compared to the previous year, security measures against targeted attac ...
Information Security - National University of Sciences and
... Communication Security • Alice sends a message to Bob • A malicious person Eve can listen • Listening: Attack on confidentiality • Modify data and again transmit to Bob: Attack on integrity • Self generate a message and send to Bob, pretending that it came from Alice: Attack on authenticity ...
... Communication Security • Alice sends a message to Bob • A malicious person Eve can listen • Listening: Attack on confidentiality • Modify data and again transmit to Bob: Attack on integrity • Self generate a message and send to Bob, pretending that it came from Alice: Attack on authenticity ...
Security - UTRGV Faculty Web
... Christopher Padilla Computer & Communications Industry Association ...
... Christopher Padilla Computer & Communications Industry Association ...
Emsisoft Internet Security
... EMSISOFT‘S VISION: A MALWARE-FREE WORLD It’s a place where home and business computer security is engineered to perfection. It’s a software that effectively detects new threats before your computer is compromised. It’s an innovative Anti-Malware that is efficient, powerful, unobtrusive and minimalistic ...
... EMSISOFT‘S VISION: A MALWARE-FREE WORLD It’s a place where home and business computer security is engineered to perfection. It’s a software that effectively detects new threats before your computer is compromised. It’s an innovative Anti-Malware that is efficient, powerful, unobtrusive and minimalistic ...
Homeland Security
... the Department and our highest priority •The Department's efforts to battle terrorism, •detecting explosives in public spaces and transportation networks • helping protect critical infrastructure and cyber networks from attack •detecting agents of biological warfare ...
... the Department and our highest priority •The Department's efforts to battle terrorism, •detecting explosives in public spaces and transportation networks • helping protect critical infrastructure and cyber networks from attack •detecting agents of biological warfare ...
attacks
... The process of using social skills to persuade people to reveal access credentials or other valuable information. ◦ Over the phone: “Hey, Joe, this is Andy from department C. Aaron (the boss) told me to ask you to give me the XYZ plans, the customers is demanding we fix the bugs by tomorrow. “ ◦ Ove ...
... The process of using social skills to persuade people to reveal access credentials or other valuable information. ◦ Over the phone: “Hey, Joe, this is Andy from department C. Aaron (the boss) told me to ask you to give me the XYZ plans, the customers is demanding we fix the bugs by tomorrow. “ ◦ Ove ...
The Need for Security
... function Enable the safe operation of applications Protect the data Safeguard technology assets ...
... function Enable the safe operation of applications Protect the data Safeguard technology assets ...
Bandura® Releases REACT™ Software to Integrate Internal
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
International Organized Crime
... • Cultural Differences • Values • Sovereignty • Can we just ignore the problem of crimes such as: ...
... • Cultural Differences • Values • Sovereignty • Can we just ignore the problem of crimes such as: ...
Huntsman Security updates trail-blazing cyber security analytics and
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
Tungsten™
... is dependent on strengthening cyber security measures and increasing collaboration with IT and physical security stakeholders. They empower US federal agencies to implement holistic security measures to protect critical infrastructure, buildings, assets, information and people. ...
... is dependent on strengthening cyber security measures and increasing collaboration with IT and physical security stakeholders. They empower US federal agencies to implement holistic security measures to protect critical infrastructure, buildings, assets, information and people. ...
Insider Threat and the Dark Web: Cyber Response Mini
... managing the technical response, responding to massive incidents requires synchronizing business, legal, communications, as well as technical activities. Most companies would benefit from a pre-defined and dedicated Crisis Management Executive that has a broad enterprise view of the organization and ...
... managing the technical response, responding to massive incidents requires synchronizing business, legal, communications, as well as technical activities. Most companies would benefit from a pre-defined and dedicated Crisis Management Executive that has a broad enterprise view of the organization and ...
Security and Ethical Challenges
... A malicious or criminal hacker who maintains knowledge of vulnerabilities found for private advantage ...
... A malicious or criminal hacker who maintains knowledge of vulnerabilities found for private advantage ...
INTRODUCTION
... computer equipped with windows were confirmed. Another usage could be the selling of the code to competitors.”9 ...
... computer equipped with windows were confirmed. Another usage could be the selling of the code to competitors.”9 ...
Why Cryptography is Harder Than It Looks
... – Motivation of attackers • Vast knowledge and free time • Few financial resources and / or vendetta ...
... – Motivation of attackers • Vast knowledge and free time • Few financial resources and / or vendetta ...
Slide 1
... Instead of requiring (certain types of) attribute value match (e.g., the destination IP address of one alert matches the source IP of another) ...
... Instead of requiring (certain types of) attribute value match (e.g., the destination IP address of one alert matches the source IP of another) ...