HUANG LAYOUT - Systems and Computer Engineering
... are disjoint from the working path corresponding to the recovery path in question. In other words, in 1:1 protection the protected traffic normally travels only on the working path, and is switched to the recovery path when the working path has a fault. The protection switching is typically initiate ...
... are disjoint from the working path corresponding to the recovery path in question. In other words, in 1:1 protection the protected traffic normally travels only on the working path, and is switched to the recovery path when the working path has a fault. The protection switching is typically initiate ...
A Protocol for a Wireless ... Xiaolan Qian
... Lan Standard, Bluetooth, and HomeRF. Although these solutions target different environments and offer varying services, they all provide wireless data communications and mobility management. They are also based on more sophisticated radios with spread-spectrum technologies increasing the cost and si ...
... Lan Standard, Bluetooth, and HomeRF. Although these solutions target different environments and offer varying services, they all provide wireless data communications and mobility management. They are also based on more sophisticated radios with spread-spectrum technologies increasing the cost and si ...
Wireless Security By Neeraj Poddar Advanced
... Personal WPA or WPA-PSK (Key Pre-Shared) that use for small office and home for domestic use authentication which does not use an authentication server and the data cryptography key can go up to 256 bits. Enterprise WPA or Commercial that the authentication is made by an authentication server 802.1x ...
... Personal WPA or WPA-PSK (Key Pre-Shared) that use for small office and home for domestic use authentication which does not use an authentication server and the data cryptography key can go up to 256 bits. Enterprise WPA or Commercial that the authentication is made by an authentication server 802.1x ...
List of Figures
... arrangements. Of particular interest are the peculiarities of the commercial relationships that exist between ISPs that may be in an up and downstream relationship to each other, but can also be in competition with each other. Third, there is a focus on economics and economic incentives. Issues here ...
... arrangements. Of particular interest are the peculiarities of the commercial relationships that exist between ISPs that may be in an up and downstream relationship to each other, but can also be in competition with each other. Third, there is a focus on economics and economic incentives. Issues here ...
2nd draft
... underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: acknowledgements (ACKs): receiver explicitly tells sender ...
... underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: acknowledgements (ACKs): receiver explicitly tells sender ...
CS244a: An Introduction to Computer Networks
... – Scalable? (broadcast, spanning tree algorithm…) – Heterogeneity (understands one type of LAN address only) ...
... – Scalable? (broadcast, spanning tree algorithm…) – Heterogeneity (understands one type of LAN address only) ...
MAPS™ ISDN-SIGTRAN Emulator
... User-friendly GUI for configuring the IUA IP layer Supports interfacing with both high-speed PRI (Primary Rate Interface or 23B +D) and lowspeed BRI (Basic Rate Interface, or 2B + D) digital lines. Generates and process all ISDN messages such as Setup, Connect, Release messages, & more User controll ...
... User-friendly GUI for configuring the IUA IP layer Supports interfacing with both high-speed PRI (Primary Rate Interface or 23B +D) and lowspeed BRI (Basic Rate Interface, or 2B + D) digital lines. Generates and process all ISDN messages such as Setup, Connect, Release messages, & more User controll ...
IP Address - ECSE - Rensselaer Polytechnic Institute
... a new protocol (IP) and map all applications/networks to IP Require only one mapping (IP -> new protocol) when a new protocol/app is added Global address space can be created for universal addressibility and scaling ...
... a new protocol (IP) and map all applications/networks to IP Require only one mapping (IP -> new protocol) when a new protocol/app is added Global address space can be created for universal addressibility and scaling ...
View
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
Stirling-Photonic ne.. - School of Electrical Engineering and
... In the context of a Canadian research network on agile all-photonic networks (AAPN), we assume that very fast photonic space switches will be available in the not-too-distant future and that the large bandwidth available over a single optical wavelength can be shared among several traffic flows, whi ...
... In the context of a Canadian research network on agile all-photonic networks (AAPN), we assume that very fast photonic space switches will be available in the not-too-distant future and that the large bandwidth available over a single optical wavelength can be shared among several traffic flows, whi ...
Chapter 1: A First Look at Windows 2000 Professional
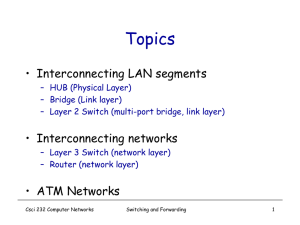
... As network usage increases, it may be necessary to support remote connections to network ISDN, DSL, cable modem, or dedicated leased-line environments may be best solution Repeater increases length of network by eliminating effect of signal attenuation Bridge installed between two network segments f ...
... As network usage increases, it may be necessary to support remote connections to network ISDN, DSL, cable modem, or dedicated leased-line environments may be best solution Repeater increases length of network by eliminating effect of signal attenuation Bridge installed between two network segments f ...
Contents - Andrew Noske
... syntax for application layer) 5. Session interhost communication (establishes, manages & terminates session between applications, + does exception reporting & class of service) 4. Transport end-to-end communication (info flow control & fault detection, + establishes, maintains & terminates v ...
... syntax for application layer) 5. Session interhost communication (establishes, manages & terminates session between applications, + does exception reporting & class of service) 4. Transport end-to-end communication (info flow control & fault detection, + establishes, maintains & terminates v ...
Virtual Service Networks
... Use shortest path first tree rooted at each node as its own private multicast tree. A B R ...
... Use shortest path first tree rooted at each node as its own private multicast tree. A B R ...
dccn-ARP - WordPress.com
... If the IP address of the destination host in the ARP query is infact one of the hosts connected to the router, then, the router itself replies the sender with the physical address of the router itself in a unicast ARP response message. When a packet arrives with the destination host’s IP address and ...
... If the IP address of the destination host in the ARP query is infact one of the hosts connected to the router, then, the router itself replies the sender with the physical address of the router itself in a unicast ARP response message. When a packet arrives with the destination host’s IP address and ...
Title: First Slide in a Presentation
... • Provides AAA services to network devices that function as AAA clients, such as routers, NASs, PIX Security Appliances, or VPN Concentrators • Helps centralize access control and accounting, in addition to router and switch access management • Allows network administrators to quickly administer acc ...
... • Provides AAA services to network devices that function as AAA clients, such as routers, NASs, PIX Security Appliances, or VPN Concentrators • Helps centralize access control and accounting, in addition to router and switch access management • Allows network administrators to quickly administer acc ...
FASP Technology Datasheet
... Complete server-side policy management: enforce all Aspera transfer properties including authorization (allowed direction, allowed IP, and secure token lifetime), bandwidth controls, encryption settings, directory creation masks and overwrite policies, and email notifications globally by server, by u ...
... Complete server-side policy management: enforce all Aspera transfer properties including authorization (allowed direction, allowed IP, and secure token lifetime), bandwidth controls, encryption settings, directory creation masks and overwrite policies, and email notifications globally by server, by u ...
ppt
... Carrier Sense Multiple Access with Collision Detection It is based on the philosophy: “Let’s just let everyone onto the media whenever they want & if two users access the media at the same time, we’ll work it out somehow.” 1. Carrier sense: the PC wishing to put data onto the shared media listens ...
... Carrier Sense Multiple Access with Collision Detection It is based on the philosophy: “Let’s just let everyone onto the media whenever they want & if two users access the media at the same time, we’ll work it out somehow.” 1. Carrier sense: the PC wishing to put data onto the shared media listens ...
Peer-to-peer networking with BitTorrent - UCLA
... network, if the participants share a part of their own (hardware) resources (processing power, storage capacity, network link capacity, printers,...). These shared resources are necessary to provide the Service and content offered by the network (e.g. file sharing or shared workspaces for collaborat ...
... network, if the participants share a part of their own (hardware) resources (processing power, storage capacity, network link capacity, printers,...). These shared resources are necessary to provide the Service and content offered by the network (e.g. file sharing or shared workspaces for collaborat ...
momina-RIP
... One of Interior gateway protocol (IGP) routing protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also some ...
... One of Interior gateway protocol (IGP) routing protocols on internal networks. Helps routers dynamically adapt to changes of network connections by communicating information about which networks each router can reach and how far away those networks are. Its made obsolete by OSPF and IS-IS. Also some ...
pptx
... • What information is exchanged in DV protocols? • What assumptions are required for the correctness of RIP • What causes RIP to converge so slowly? • How does split-horizon w/ poison-reverse work? • What CtoI situations does split-horizon w/ poison-reverse prevent • What CtoI situations does trigge ...
... • What information is exchanged in DV protocols? • What assumptions are required for the correctness of RIP • What causes RIP to converge so slowly? • How does split-horizon w/ poison-reverse work? • What CtoI situations does split-horizon w/ poison-reverse prevent • What CtoI situations does trigge ...
MPLS QoS - Lyle School of Engineering
... • An attempt to bring the ATM capabilities to IP – T-Spec: Max burst size, token rate, committed rate, etc. – R-Spec: Effective bandwidth or amount of resource required within the network. ...
... • An attempt to bring the ATM capabilities to IP – T-Spec: Max burst size, token rate, committed rate, etc. – R-Spec: Effective bandwidth or amount of resource required within the network. ...
IPv6 - DePaul University
... this (will need other protocols such as Real-Time Protocol or Resource Reservation Protocol). Sounds like MPLS, but MPLS is designed for MPLS-based edge routers, whereas flow label is end to end. TCP/IP Protocol Suite ...
... this (will need other protocols such as Real-Time Protocol or Resource Reservation Protocol). Sounds like MPLS, but MPLS is designed for MPLS-based edge routers, whereas flow label is end to end. TCP/IP Protocol Suite ...
3rd Edition: Chapter 3
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
WAP - ICMP - Extra Reading File
... Subject to the same delivery failures as any IP packet. This creates a scenario where error reports could generate more error reports, causing increased congestion on an already ailing network. For this reason, errors created by ICMP messages do not generate their own ICMP messages. It is thus possi ...
... Subject to the same delivery failures as any IP packet. This creates a scenario where error reports could generate more error reports, causing increased congestion on an already ailing network. For this reason, errors created by ICMP messages do not generate their own ICMP messages. It is thus possi ...
Link Layer
... “Taking Turns” MAC protocols channel partitioning MAC protocols: o share channel efficiently and fairly at high load o inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols o efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: o share channel efficiently and fairly at high load o inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols o efficient at low load: single node can fully uti ...