Chapter 3 OSI Model Worksheet In class lecture and handout.
... 5. This layer establishes the rules of the conversation between two applications. For example, will they take turns speaking, or can they send and receive at the same time. _________________ ...
... 5. This layer establishes the rules of the conversation between two applications. For example, will they take turns speaking, or can they send and receive at the same time. _________________ ...
No Slide Title - Ed Lazowska
... Summary Using TCP/IP and lower layers, we can get multipacket messages delivered reliably from address space A on machine B to address space C on machine D, where machines B and D are many heterogeneous network hops apart, without knowing any of the ...
... Summary Using TCP/IP and lower layers, we can get multipacket messages delivered reliably from address space A on machine B to address space C on machine D, where machines B and D are many heterogeneous network hops apart, without knowing any of the ...
View Report - PDF
... Information Technology in writing or by email. Information Technology will unblock that site or category for that associate only. Information Technology will track approved exceptions and report on them upon request. 4.0 Enforcement The IT Security Officer will periodically review Internet use monit ...
... Information Technology in writing or by email. Information Technology will unblock that site or category for that associate only. Information Technology will track approved exceptions and report on them upon request. 4.0 Enforcement The IT Security Officer will periodically review Internet use monit ...
CPSC 155a Lecture 3
... • Protocols: abstract objects that makeup a layer • Lowest level: hardware specific, implemented by a combination of network adaptors and OS device drivers • IP (Internet Protocol): focal point of the architecture, provides host-to-host connection, defines common methods of exchanging packets • TCP ...
... • Protocols: abstract objects that makeup a layer • Lowest level: hardware specific, implemented by a combination of network adaptors and OS device drivers • IP (Internet Protocol): focal point of the architecture, provides host-to-host connection, defines common methods of exchanging packets • TCP ...
Artificial Intelligence in Networking: Ant Colony Optimization
... Determines a path before packets are sent, and then sends all packets along that path ...
... Determines a path before packets are sent, and then sends all packets along that path ...
CSC 336 Data Communications and Networking Congestion
... • Receiver starts receiving data packets ...
... • Receiver starts receiving data packets ...
PSTN-Internet Convergence with QoS and Wireless Applications
... (Sometimes an incomplete version of the function provided by the communication system may be useful as a performance enhancement.) (J. H. Saltzer et al., “End-to-end Arguments in System Design”) ...
... (Sometimes an incomplete version of the function provided by the communication system may be useful as a performance enhancement.) (J. H. Saltzer et al., “End-to-end Arguments in System Design”) ...
Lecture8
... • With Third Generation (3G), emails, multimedia attachments and other data will simply be downloaded to their mobile devices. ( T ) • Circuit switched data formats are much more common than their packet switched counterparts.( F ) • One of the most important application for packet data is Web brows ...
... • With Third Generation (3G), emails, multimedia attachments and other data will simply be downloaded to their mobile devices. ( T ) • Circuit switched data formats are much more common than their packet switched counterparts.( F ) • One of the most important application for packet data is Web brows ...
The University of Oklahoma Virtual Private Network
... multiple packets in a way that did not make immediate sense to the firewall and these parts were sent in randomly, a STATELESS Firewall would allow it through, and the machine to which this content is delivered, will reassemble these packets and possibly do a lot of damage to its own data. ...
... multiple packets in a way that did not make immediate sense to the firewall and these parts were sent in randomly, a STATELESS Firewall would allow it through, and the machine to which this content is delivered, will reassemble these packets and possibly do a lot of damage to its own data. ...
Overview - La Revue MODULAD
... – No insertion of own packets, just listen! – Obtain information from the captured data ...
... – No insertion of own packets, just listen! – Obtain information from the captured data ...
Review of Underlying Network Technologies
... Want user to see only one network to which all machines are connected Network level interconnections means: ...
... Want user to see only one network to which all machines are connected Network level interconnections means: ...
A6_Oct_07_08 - Raadio- ja sidetehnika instituut
... – (pro-active) traffic demands expected between any two locations in the network and – (re-active) the actual traffic demand ...
... – (pro-active) traffic demands expected between any two locations in the network and – (re-active) the actual traffic demand ...
A method for IP multicast performance monitoring
... Motivation • Artifacts seen by IPTV users are mainly related to Packet Loss - IPTV service is sensitive to very low PL rates (10-4 and below) ...
... Motivation • Artifacts seen by IPTV users are mainly related to Packet Loss - IPTV service is sensitive to very low PL rates (10-4 and below) ...
PowerPoint format - Computer Science
... • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
... • Top three layers are not well-defined, all have to do with application level abstractions such as transformation of different data formats ...
Introduction
... LANs and WANs There are two broad categories of networks: Local Area Networks (LAN) Wide Area Networks (WAN) ...
... LANs and WANs There are two broad categories of networks: Local Area Networks (LAN) Wide Area Networks (WAN) ...
HyperText Transfer Protocol
... length data sequences from a source to a destination via one or more networks while maintaining the quality of service requested by the Transport layer. ...
... length data sequences from a source to a destination via one or more networks while maintaining the quality of service requested by the Transport layer. ...
BCS433 Data Communication & Networking
... Metropolitan Network (MAN) Wide Area Network (WAN) ...
... Metropolitan Network (MAN) Wide Area Network (WAN) ...
No Slide Title
... Every computer on the Internet has a unique address. Information sent across IP networks is broken up into bite-sized pieces, called packets. The information within a packet is usually between 1 and about 1500 characters long. ...
... Every computer on the Internet has a unique address. Information sent across IP networks is broken up into bite-sized pieces, called packets. The information within a packet is usually between 1 and about 1500 characters long. ...
Windows Vista Security and Compliance
... Enhanced Security All communications are authenticated, authorized & healthy Defense-in-depth on your terms with DHCP, VPN, IPsec, 802.1X Policy-based access that IT Pros can set and control ...
... Enhanced Security All communications are authenticated, authorized & healthy Defense-in-depth on your terms with DHCP, VPN, IPsec, 802.1X Policy-based access that IT Pros can set and control ...
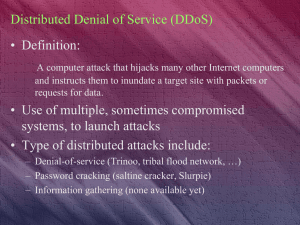
Distributed Denial of Service (DDoS)
... • Untrusted tools could be used to distribute viruses, Trojan horses and back doors ...
... • Untrusted tools could be used to distribute viruses, Trojan horses and back doors ...
Communication by Computer
... What sorts of ethical issues can you imagine cropping up on the Internet? Should nations, universities, or families have internet policies? Should the Internet be privately managed or publicly managed? What sort of Internet policy should McMaster have? ...
... What sorts of ethical issues can you imagine cropping up on the Internet? Should nations, universities, or families have internet policies? Should the Internet be privately managed or publicly managed? What sort of Internet policy should McMaster have? ...
Campus Area Networking
... Transport - Layer 4 The transport layer is responsible for overall end to end validity and integrity of the transmission. The lower data link layer (layer 2) is only responsible for delivering packets from one node to another. Thus, if a packet gets lost in a router somewhere in the enterprise inte ...
... Transport - Layer 4 The transport layer is responsible for overall end to end validity and integrity of the transmission. The lower data link layer (layer 2) is only responsible for delivering packets from one node to another. Thus, if a packet gets lost in a router somewhere in the enterprise inte ...