CCNA 1 v3.0 - chu.edu.tw
... Which OSI and TCP/IP layer appears in both models yet has different functions in each? • application ...
... Which OSI and TCP/IP layer appears in both models yet has different functions in each? • application ...
Chapter 1 - William Stallings, Data and Computer Communications
... This affects traffic volume in a number of ways: • It enables a user to be continuously consuming network capacity • Capacity can be consumed on multiple devices simultaneously • Different broadband devices enable different applications which may have greater traffic generation capability ...
... This affects traffic volume in a number of ways: • It enables a user to be continuously consuming network capacity • Capacity can be consumed on multiple devices simultaneously • Different broadband devices enable different applications which may have greater traffic generation capability ...
DCC10e
... This affects traffic volume in a number of ways: • It enables a user to be continuously consuming network capacity • Capacity can be consumed on multiple devices simultaneously • Different broadband devices enable different applications which may have greater traffic generation capability ...
... This affects traffic volume in a number of ways: • It enables a user to be continuously consuming network capacity • Capacity can be consumed on multiple devices simultaneously • Different broadband devices enable different applications which may have greater traffic generation capability ...
Defense in Depth / Firewalls Presentation
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
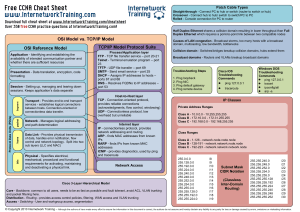
CCNA cheat sheet - Internetwork Training
... (acknowledgments, flow control, windowing) UDP - Connectionless protocol, low overhead but unreliable Internet layer IP - connectionless protocol, provides network addressing and routing ARP - finds MAC addresses from known IPs RARP - finds IPs from known MAC addresses ICMP - provides diagnostics, u ...
... (acknowledgments, flow control, windowing) UDP - Connectionless protocol, low overhead but unreliable Internet layer IP - connectionless protocol, provides network addressing and routing ARP - finds MAC addresses from known IPs RARP - finds IPs from known MAC addresses ICMP - provides diagnostics, u ...
Lec-14.-Network-Security - Degree 36
... Crashing the victim Ping-of-Death A type of Denial of Service (DoS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets. ...
... Crashing the victim Ping-of-Death A type of Denial of Service (DoS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets. ...
Some Tools for Computer Security Incident Response
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
Convergence
... • VPNs are managed by carriers that provide links between corporate sites, and between corporate sites and their customers ...
... • VPNs are managed by carriers that provide links between corporate sites, and between corporate sites and their customers ...
Language Support for Concurrency
... send packet on each hop [framing, error detection,…] send packet end to end [addressing, routing] pace transmissions [detect congestion] retransmit erroneous or missing packets [acks, timeout] find destination address from name [DNS] ...
... send packet on each hop [framing, error detection,…] send packet end to end [addressing, routing] pace transmissions [detect congestion] retransmit erroneous or missing packets [acks, timeout] find destination address from name [DNS] ...
NAME: NWOSU JENNIFER CHIMENKA COLLEGE: MEDICINE AND
... route traffic across the country from one commercial site to another without passing through the government funded NSFNet Internet backbone. Delphi was the first national commercial online service to offer Internet access to its subscribers. It opened up an email connection in July 1992 and full Int ...
... route traffic across the country from one commercial site to another without passing through the government funded NSFNet Internet backbone. Delphi was the first national commercial online service to offer Internet access to its subscribers. It opened up an email connection in July 1992 and full Int ...
Defense in Depth / Firewalls Presentation
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
Defense in Depth / Firewalls Presentation
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
Internet History - Physics, Computer Science and Engineering
... Univ of Cal at Berkley (UCB) by its Computer Systems Research (CSRG). Public funding dictated it be made available at cost. Lots of startup companies used it. Inexpensive Microprocessors Inexpensive wide-area fiber optic bandwidth NSFNET regional networks ...
... Univ of Cal at Berkley (UCB) by its Computer Systems Research (CSRG). Public funding dictated it be made available at cost. Lots of startup companies used it. Inexpensive Microprocessors Inexpensive wide-area fiber optic bandwidth NSFNET regional networks ...
Collecting Information to Visualize Network Status
... http://i-path.goto.info.waseda.ac.jp/trac/i-Path/ • Dai Mochinaga, Katsushi Kobayashi, Shigeki Goto, Akihiro Shimoda, and Ichiro Murase, Collecting Information to Visualize Network Status, 28th APAN Network Research Workshop, ...
... http://i-path.goto.info.waseda.ac.jp/trac/i-Path/ • Dai Mochinaga, Katsushi Kobayashi, Shigeki Goto, Akihiro Shimoda, and Ichiro Murase, Collecting Information to Visualize Network Status, 28th APAN Network Research Workshop, ...
Internet Traffic Patterns
... Example: In a switched packet network, a link is “broken” and a packet analyser is connected between two network nodes ...
... Example: In a switched packet network, a link is “broken” and a packet analyser is connected between two network nodes ...
Midterm Sample
... 3) Statistical multiplexing is most useful when the peak rate is close to the average rate. False 4) The changing of either the IP address or the name leads to an update of DNS. True 5) TCP uses destination IP address and port number to identify the application layer process. False ...
... 3) Statistical multiplexing is most useful when the peak rate is close to the average rate. False 4) The changing of either the IP address or the name leads to an update of DNS. True 5) TCP uses destination IP address and port number to identify the application layer process. False ...
WAN topology
... – Efficient and secure communication between the enterprise campus and remote locations, business partners, mobile users, and the Internet – Aggregates connectivity, provides traffic filtering and inspection and routing to the enterprise campus – Includes WAN, VPN, internet access, and e-commerce mo ...
... – Efficient and secure communication between the enterprise campus and remote locations, business partners, mobile users, and the Internet – Aggregates connectivity, provides traffic filtering and inspection and routing to the enterprise campus – Includes WAN, VPN, internet access, and e-commerce mo ...
A Study on Quality of Service Issues
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
NetworkingReview
... LAN, WAN, bridge, repeater, switch, router, gateway, backbone. 6. Explain the hidden terminal problem for wireless networks. What is a solution? 7. At what layer in the TCP/IP protocol hierarchy would a firewall be placed to filter messages based on a. Message content b. Source address c. Type of ap ...
... LAN, WAN, bridge, repeater, switch, router, gateway, backbone. 6. Explain the hidden terminal problem for wireless networks. What is a solution? 7. At what layer in the TCP/IP protocol hierarchy would a firewall be placed to filter messages based on a. Message content b. Source address c. Type of ap ...
tutorial 1 - UniMAP Portal
... 1b. Repeat part (a) for an e-mail message. At this point, you may have to conjecture different approaches about what goes on inside the computer network. 1c. Are the procedures in parts (a) and (b) connection-oriented or connectionless? 2a. Describe what step-by-step procedure might be involved insi ...
... 1b. Repeat part (a) for an e-mail message. At this point, you may have to conjecture different approaches about what goes on inside the computer network. 1c. Are the procedures in parts (a) and (b) connection-oriented or connectionless? 2a. Describe what step-by-step procedure might be involved insi ...