slides - TNC15
... • He finds that the requirements for data are very different than those for voice. ...
... • He finds that the requirements for data are very different than those for voice. ...
Medium Time Metric
... Each path flow φij exists only on πij (path) each edge (u, v) in the transmission graph the sum of the fractional shares used by all flows in the interference neighborhood of (u, v) must be less than or equal to 100%. this is a more complicated version of the classic edge ...
... Each path flow φij exists only on πij (path) each edge (u, v) in the transmission graph the sum of the fractional shares used by all flows in the interference neighborhood of (u, v) must be less than or equal to 100%. this is a more complicated version of the classic edge ...
Enter your project title here
... company a fair chance to claim that its existing product is actually a VPN. But no matter what definition you choose, the networking buzz- phrase doesn't make sense. The idea is to create a private network via tunneling and/or encryption over the public Internet. Sure, it's a lot cheaper than using ...
... company a fair chance to claim that its existing product is actually a VPN. But no matter what definition you choose, the networking buzz- phrase doesn't make sense. The idea is to create a private network via tunneling and/or encryption over the public Internet. Sure, it's a lot cheaper than using ...
electronic-commerce-9th-edition-gary-schneider-test-bank
... 51. A computer ____________________ is any technology that allows people to connect computers to each computer. ________________________________________ 52. A network which uses a specific set of rules and connects networks all over the world to each other, is called the ____________________. ______ ...
... 51. A computer ____________________ is any technology that allows people to connect computers to each computer. ________________________________________ 52. A network which uses a specific set of rules and connects networks all over the world to each other, is called the ____________________. ______ ...
Why Fiber Optic?
... Benefits to City Government • Develop IP based phone system for all City buildings o Cost savings o Increased efficiency & reliability ...
... Benefits to City Government • Develop IP based phone system for all City buildings o Cost savings o Increased efficiency & reliability ...
Chapter1
... 1.2 Network edge 1.3 Network core 1.4 Network access and physical media 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...
... 1.2 Network edge 1.3 Network core 1.4 Network access and physical media 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...
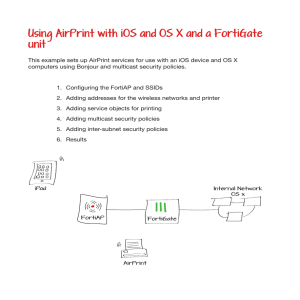
Using AirPrint with iOS and OS X and a FortiGate unit
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
The OSI Reference Model - Department of Computing
... Understand the OSI model and the tcp/ip model – Understand the function protocols and their role at each layer. ...
... Understand the OSI model and the tcp/ip model – Understand the function protocols and their role at each layer. ...
Chapter 18 - William Stallings, Data and Computer
... In that case there is no searching and next hop is found quickly. Moving packet from input to output port: Bus => simple, one at a time (slow) Switch => connects two end points, flexible connection, complex control ...
... In that case there is no searching and next hop is found quickly. Moving packet from input to output port: Bus => simple, one at a time (slow) Switch => connects two end points, flexible connection, complex control ...
lecture3 - Academic Csuohio
... Covered a “ton” of material! Internet overview What’s a protocol? Network edge, core, access network Packet-switching versus circuit-switching Internet structure Performance: loss, delay, throughput Layering, reference models Networking standards History ...
... Covered a “ton” of material! Internet overview What’s a protocol? Network edge, core, access network Packet-switching versus circuit-switching Internet structure Performance: loss, delay, throughput Layering, reference models Networking standards History ...
PowerPoint
... congestion control: • senders “slow down sending rate” when network Introduction congested ...
... congestion control: • senders “slow down sending rate” when network Introduction congested ...
notes - Academic Csuohio
... Covered a “ton” of material! Internet overview What’s a protocol? Network edge, core, access network Packet-switching versus circuit-switching Internet structure Performance: loss, delay, throughput Layering, reference models Networking standards History ...
... Covered a “ton” of material! Internet overview What’s a protocol? Network edge, core, access network Packet-switching versus circuit-switching Internet structure Performance: loss, delay, throughput Layering, reference models Networking standards History ...
Internet Access - University of St. Thomas
... • I encrypt the secret with THEIR public key • They decrypt with their own private key – I can use my PRIVATE key to “sign” things • I encrypt a hash (checksum) with my PRIVATE key • Others can check the result with my PUBLIC key March 2005 ...
... • I encrypt the secret with THEIR public key • They decrypt with their own private key – I can use my PRIVATE key to “sign” things • I encrypt a hash (checksum) with my PRIVATE key • Others can check the result with my PUBLIC key March 2005 ...
Chapter 4 : TCP/IP and OSI
... Segregation means that no other software needs to be concerned about net specifics ...
... Segregation means that no other software needs to be concerned about net specifics ...
PowerPoint
... Of the possible paths from C to I, router C will identify one as the “shortest” and will use that path for all traffic from C to I Traffic from A and B will flow over the same path to I, congesting some links while leaving others under-utilized If the chosen path fails, the new path may be dif ...
... Of the possible paths from C to I, router C will identify one as the “shortest” and will use that path for all traffic from C to I Traffic from A and B will flow over the same path to I, congesting some links while leaving others under-utilized If the chosen path fails, the new path may be dif ...
WiHawk
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
A Guide to Designing and Implementing Local and Wide Area
... to another, reducing excessive traffic Join neighboring or distant networks Connect dissimilar networks Prevent network bottlenecks by isolating portions of a network Secure portions of a network from intruders ...
... to another, reducing excessive traffic Join neighboring or distant networks Connect dissimilar networks Prevent network bottlenecks by isolating portions of a network Secure portions of a network from intruders ...
eRouter-200TM
... cost-effective T1 broadband access router that combines a CSU/DSU, IP router for data transport, DHCP server for address management, and a firewall for LAN security in a single, compact unit. It simplifies business communication, saves on capital and operational expenses, and delivers the industry’s ...
... cost-effective T1 broadband access router that combines a CSU/DSU, IP router for data transport, DHCP server for address management, and a firewall for LAN security in a single, compact unit. It simplifies business communication, saves on capital and operational expenses, and delivers the industry’s ...
HW1 Solution
... root router would have a dead 17th port, and so there would be a routing table of size 16 on the first router, and 17 on every other router. This would be of the form: • (prefix, halfbyte, unmatched) routes to the port indexed by halfbyte, where prefix is the total specified address on the parent r ...
... root router would have a dead 17th port, and so there would be a routing table of size 16 on the first router, and 17 on every other router. This would be of the form: • (prefix, halfbyte, unmatched) routes to the port indexed by halfbyte, where prefix is the total specified address on the parent r ...
PPT - Oregon Connections Telecommunications Conference
... Priority access and local control Enables more coordinated emergency response Improved situational awareness across the entire incident team Coverage based on geography, not just population Coverage solutions for rural and wilderness areas Capacity tailored to expected traffic loads and special even ...
... Priority access and local control Enables more coordinated emergency response Improved situational awareness across the entire incident team Coverage based on geography, not just population Coverage solutions for rural and wilderness areas Capacity tailored to expected traffic loads and special even ...
Security Requirements
... “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using other students email account” ...
... “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using other students email account” ...