Operating System Security Fundamentals
... Controls the flow of activities Provides a user interface Administers user actions and accounts Runs software utilities and programs Enforce security measures ...
... Controls the flow of activities Provides a user interface Administers user actions and accounts Runs software utilities and programs Enforce security measures ...
Computer Security-et..
... can implement to minimize these risks Internet security risks and safeguards Ethical issues surrounding information accuracy, intellectual property rights, codes of conduct, and information privacy Computer-related health issues, their preventions, and ways to keep the environment healthy ...
... can implement to minimize these risks Internet security risks and safeguards Ethical issues surrounding information accuracy, intellectual property rights, codes of conduct, and information privacy Computer-related health issues, their preventions, and ways to keep the environment healthy ...
Security Policies, Standards, and Planning
... planning, design, and deployment. In general, policies direct how issues should be addressed and how technologies should be used. They should not specifically explain how to properly operate hardware or software. Policy should never contradict law. ...
... planning, design, and deployment. In general, policies direct how issues should be addressed and how technologies should be used. They should not specifically explain how to properly operate hardware or software. Policy should never contradict law. ...
Network Security Policy in the Work Place
... stability and assets face minimal risks. • Defines how an organization plans to protect the company’s network. ...
... stability and assets face minimal risks. • Defines how an organization plans to protect the company’s network. ...
Authentication and Remote Access
... L2TP • Designed for use across all kinds of networks, including ATM and Frame Relay • Can be implemented by both hardware and software • Designed to work with established AAA services such as RADIUS and TACACS+ ...
... L2TP • Designed for use across all kinds of networks, including ATM and Frame Relay • Can be implemented by both hardware and software • Designed to work with established AAA services such as RADIUS and TACACS+ ...
Communication - Providence Washington
... of an individual or past, present and future payment for treatment and care of an individual. Personal Identifiable Information (PII): Information that uniquely identifies an individual (e.g., name plus one of the following: social security number, driver’s license or ID card number, date of birth, ...
... of an individual or past, present and future payment for treatment and care of an individual. Personal Identifiable Information (PII): Information that uniquely identifies an individual (e.g., name plus one of the following: social security number, driver’s license or ID card number, date of birth, ...
Word Template
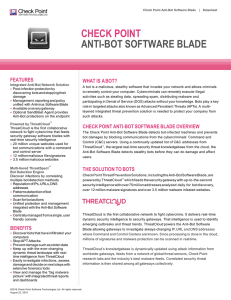
... with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the solution includes a comprehensive ThreatWiKi enabling security teams to easily understand the bot they are facing—what does it do, how it operates and any other available technical i ...
... with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the solution includes a comprehensive ThreatWiKi enabling security teams to easily understand the bot they are facing—what does it do, how it operates and any other available technical i ...
Protecting the connected barrels | Cybersecurity for
... groundbreaking research, and industry collaboration to help companies solve the most complex energy challenges. Through the Center, Deloitte’s Energy & Resources group leads the debate on critical topics on the minds of executives—from the impact of legislative and regulatory policy, to operational ...
... groundbreaking research, and industry collaboration to help companies solve the most complex energy challenges. Through the Center, Deloitte’s Energy & Resources group leads the debate on critical topics on the minds of executives—from the impact of legislative and regulatory policy, to operational ...
Best Practices for Better Security
... customer records. Anyone conducting credit card transactions must adhere to guidelines of the financial industry, including the Payment Card Industry (PCI) Data Security Standard. Healthcare providers must comply with the guidelines of the Health Insurance Portability and Accountability Act (HIPAA). ...
... customer records. Anyone conducting credit card transactions must adhere to guidelines of the financial industry, including the Payment Card Industry (PCI) Data Security Standard. Healthcare providers must comply with the guidelines of the Health Insurance Portability and Accountability Act (HIPAA). ...
Real-Time Georgia…….
... Too many single points of network & system failure Inadequate data back-up & storage procedures Often there is no real communicated security policy Networks open to Cyber Attacks and Cyber Crime Small skill base of specialist IT security personnel ...
... Too many single points of network & system failure Inadequate data back-up & storage procedures Often there is no real communicated security policy Networks open to Cyber Attacks and Cyber Crime Small skill base of specialist IT security personnel ...
Educause Task Force on Systems Security
... Trends in Academic InfoSec • E-Commerce site threaten litigation against future DDoS sites. Liability for negligence? • Insurance companies begin to rewrite liability policies, separate ‘cyber’ policies to require info security vulnerability assessments & changes. • Funding agencies to require fire ...
... Trends in Academic InfoSec • E-Commerce site threaten litigation against future DDoS sites. Liability for negligence? • Insurance companies begin to rewrite liability policies, separate ‘cyber’ policies to require info security vulnerability assessments & changes. • Funding agencies to require fire ...
Incident Response and Honeypots
... 5. Investigate until root cause discovered, then restore system from backups and patch security holes. 6. Call law enforcement before proceeding further. ...
... 5. Investigate until root cause discovered, then restore system from backups and patch security holes. 6. Call law enforcement before proceeding further. ...
PPT Version
... Recommendation X.805 • ITU-T Recommendation X.805 Security architecture for systems providing end-to-end communications had been developed by ITU-T SG 17 (ITU-T Lead Study Group on Telecommunication Security) and was published in October 2003. • The group has developed a set of the well-recognized R ...
... Recommendation X.805 • ITU-T Recommendation X.805 Security architecture for systems providing end-to-end communications had been developed by ITU-T SG 17 (ITU-T Lead Study Group on Telecommunication Security) and was published in October 2003. • The group has developed a set of the well-recognized R ...
Forcepoint™ Stonesoft Next Generation Firewall
... AETs and traffic anomalies that evade other next-generation firewalls. Only after traffic has been fully normalized can it be properly inspected across all protocols and layers for threats and malware. And only Forcepoint NGFW has been successfully tested against more than 800 million AETs. KNOWLEDG ...
... AETs and traffic anomalies that evade other next-generation firewalls. Only after traffic has been fully normalized can it be properly inspected across all protocols and layers for threats and malware. And only Forcepoint NGFW has been successfully tested against more than 800 million AETs. KNOWLEDG ...
Rapid Response to the Advanced Persistent Threat (APT)
... to highlight trends and anomalies. It protects reputation as well as critical business data, significantly reducing the cost and impact of any breach. Through the deployment of ZoneFox, activity that has previously been hidden from security teams and that breaches company policy or expected behaviou ...
... to highlight trends and anomalies. It protects reputation as well as critical business data, significantly reducing the cost and impact of any breach. Through the deployment of ZoneFox, activity that has previously been hidden from security teams and that breaches company policy or expected behaviou ...
CSCI6268L37
... Foundations of Network and Computer Security John Black Lecture #36 Dec 11th 2009 ...
... Foundations of Network and Computer Security John Black Lecture #36 Dec 11th 2009 ...
Computer Forensics
... the use of computer forensics is commonly used in the pursuit of an attacker or a criminal. There are many different professions involved with computer forensics in today’s society. A few professions include law enforcement, government agencies, military, university programs, private computer forens ...
... the use of computer forensics is commonly used in the pursuit of an attacker or a criminal. There are many different professions involved with computer forensics in today’s society. A few professions include law enforcement, government agencies, military, university programs, private computer forens ...
Intrusion Detection Technique by using K
... • Experimental results shows that our proposed new approach do better than BPNN, multiclass SVM and other well-known methods such as decision trees and Columbia model in terms of sensitivity, specificity and in particular detection accuracy. ...
... • Experimental results shows that our proposed new approach do better than BPNN, multiclass SVM and other well-known methods such as decision trees and Columbia model in terms of sensitivity, specificity and in particular detection accuracy. ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Using these tables, stateful firewalls can allow only inbound TCP packets that are in response to a connection initiated from within the internal network. Also called stateful inspection ...
... Using these tables, stateful firewalls can allow only inbound TCP packets that are in response to a connection initiated from within the internal network. Also called stateful inspection ...
XML: Part - Houston Community College System
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...
Chapter 3 - Faculty Personal Homepage
... • What are some characteristics of common computer criminals, including their objectives, available resources, willingness to accept risk, and frequency of attack? • What are the key elements of a multilayer process for managing security vulnerabilities, based on the concept of reasonable assurance? ...
... • What are some characteristics of common computer criminals, including their objectives, available resources, willingness to accept risk, and frequency of attack? • What are the key elements of a multilayer process for managing security vulnerabilities, based on the concept of reasonable assurance? ...
Security & Privacy on the WWW
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...