slides - Inria
... protocol that prefix x is reachable from AS3 and from AS2. To configure forwarding table, router 1d must determine towards which gateway it should forward packets for dest x. This is also the job on inter-AS routing protocol! 3c AS 3 3b ...
... protocol that prefix x is reachable from AS3 and from AS2. To configure forwarding table, router 1d must determine towards which gateway it should forward packets for dest x. This is also the job on inter-AS routing protocol! 3c AS 3 3b ...
Ch11
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
Document
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
Energy-Aware Adaptive Routing Solutions in IP-over-WDM Networks Filip Idzikowski
... Today’s core networks are permanently powered on and consume non-negligible amount of energy. Traffic varies over time giving an opportunity to switch off or put into standby mode a subset of network devices in order to save energy in low-demand hours. Line cards are targeted to be dynamically switc ...
... Today’s core networks are permanently powered on and consume non-negligible amount of energy. Traffic varies over time giving an opportunity to switch off or put into standby mode a subset of network devices in order to save energy in low-demand hours. Line cards are targeted to be dynamically switc ...
No Slide Title
... enabling negotiation, monitoring and enforcement of Service Level Specifications (SLS) between customer/ISP and ISP/ISP • Develop a functional model of co-operating components, algorithms and protocols offering a intra-domain traffic engineering solution for meeting the contracted SLSs • Develop a s ...
... enabling negotiation, monitoring and enforcement of Service Level Specifications (SLS) between customer/ISP and ISP/ISP • Develop a functional model of co-operating components, algorithms and protocols offering a intra-domain traffic engineering solution for meeting the contracted SLSs • Develop a s ...
5 Requirements - ISO/IEC JTC 1/SC 25/WG 1 Home Page
... This document does not specify how two home network systems share a common resource or how to ensure that two home network systems used within the same premises do not interfere with each other. However, this document requires that two home network systems may share a common resource, and that they ...
... This document does not specify how two home network systems share a common resource or how to ensure that two home network systems used within the same premises do not interfere with each other. However, this document requires that two home network systems may share a common resource, and that they ...
Chapter 4: Addressing
... If a contiguous hierarchical addressing scheme is not used, it may not be possible to summarize routes. If the network addresses do not have common bits from left to right, a summary mask cannot be applied. BEWARE! Do not advertise addresses that do not belong to you! ...
... If a contiguous hierarchical addressing scheme is not used, it may not be possible to summarize routes. If the network addresses do not have common bits from left to right, a summary mask cannot be applied. BEWARE! Do not advertise addresses that do not belong to you! ...
On-demand loop-free routing with link vectors
... find a given destination records its traversed route, and a route reply (RREP) sent by a node in response to the RREQ specifies the complete route between the node and the destination. Routers store the discovered routes in a route cache. The basic scheme in DSR is for the header of every data packet ...
... find a given destination records its traversed route, and a route reply (RREP) sent by a node in response to the RREQ specifies the complete route between the node and the destination. Routers store the discovered routes in a route cache. The basic scheme in DSR is for the header of every data packet ...
Linksys NR041 Manual
... other device on the network. Since a static IP address remains valid until you disable it, static IP addressing ensures that the device assigned it will always have that same IP address until you change it. Static IP addresses are commonly used with network devices such as server PCs or print server ...
... other device on the network. Since a static IP address remains valid until you disable it, static IP addressing ensures that the device assigned it will always have that same IP address until you change it. Static IP addresses are commonly used with network devices such as server PCs or print server ...
T R ECHNICAL ESEARCH
... number of links in the network at any given time. If node 6 fails to admit the ow, 6 sends an ACF The TORA routing table is restructured in INORA message to 3 as shown in g.9 Associated with every destination, there is a list of next hops which is created by TORA. With the feedback that TORA recei ...
... number of links in the network at any given time. If node 6 fails to admit the ow, 6 sends an ACF The TORA routing table is restructured in INORA message to 3 as shown in g.9 Associated with every destination, there is a list of next hops which is created by TORA. With the feedback that TORA recei ...
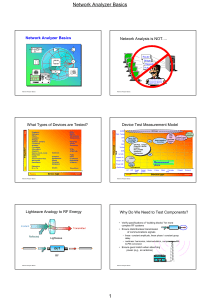
Network Analyzer Basics
... Zo determines relationship between voltage and current waves Zo is a function of physical dimensions and εr Zo is usually a real impedance (e.g. 50 or 75 ohms) ...
... Zo determines relationship between voltage and current waves Zo is a function of physical dimensions and εr Zo is usually a real impedance (e.g. 50 or 75 ohms) ...
Owner`s Manual Network Set
... Examples: Type and contents of alert mail....................................................................................................28 ...
... Examples: Type and contents of alert mail....................................................................................................28 ...
PDF - at www.arxiv.org.
... from relatively obscure research activities to a healthy research topic attracting both network designers and application developers[1], due to that the communication model of the Internet is based on some inherent networking assumptions, e.g., the existence of a continuous end-to-end path between t ...
... from relatively obscure research activities to a healthy research topic attracting both network designers and application developers[1], due to that the communication model of the Internet is based on some inherent networking assumptions, e.g., the existence of a continuous end-to-end path between t ...
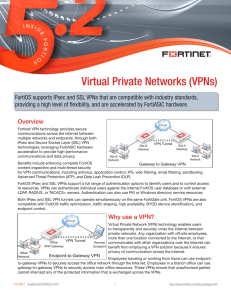
Virtual Private Networks (VPNs)
... FortiOS also supports policy-based and route-based IPsec VPNs. A route-based VPN creates a virtual IPsec network interface that applies encryption or decryption as needed to any traffic that interface carries. Route-based VPNs are also known as interface-based VPNs. A policy-based VPN is implemented ...
... FortiOS also supports policy-based and route-based IPsec VPNs. A route-based VPN creates a virtual IPsec network interface that applies encryption or decryption as needed to any traffic that interface carries. Route-based VPNs are also known as interface-based VPNs. A policy-based VPN is implemented ...
Module 2 - OoCities
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
... at MIT in 1957.(Answer: John McCarthy). Q15: ARPA’s networking project Managed by ______________ from MIT. (Answer: Lawrence Robert). Q16: Nodes with large time-sharing computers at the connected sites are called _____________. (Answer: hosts). Q17: What’s the different between Circuit-switching vs. ...
In Search of Path Diversity in ISP Networks ABSTRACT
... the Akamai content distribution network, they explore the performance benefits of multihoming where traffic uses first-hop diversity of routing to different ISPs on the first hop to the same destination. Using traceroute measurements between Akamai servers and Keynote Systems nodes in geographically ...
... the Akamai content distribution network, they explore the performance benefits of multihoming where traffic uses first-hop diversity of routing to different ISPs on the first hop to the same destination. Using traceroute measurements between Akamai servers and Keynote Systems nodes in geographically ...
6 The model to classify the requirements for Smart Grid
... The phrase "is required to" indicates a requirement which must be strictly followed and from which no deviation is permitted if conformance to this Deliverable is to be claimed. The phrase "is prohibited from" indicates a requirement which must be strictly followed and from which no deviation is per ...
... The phrase "is required to" indicates a requirement which must be strictly followed and from which no deviation is permitted if conformance to this Deliverable is to be claimed. The phrase "is prohibited from" indicates a requirement which must be strictly followed and from which no deviation is per ...
SK-NET FDDI
... • EISA Adapter for SysKonnect FDDI NICs designed for installation in EISA (Extended Industry Standard) bus computers • ISA Adapter for SysKonnect FDDI NICs designed for installation in ISA (Industry Standard) bus computers • PCI Adapter for SysKonnect FDDI NICs designed for installation in PCI (Peri ...
... • EISA Adapter for SysKonnect FDDI NICs designed for installation in EISA (Extended Industry Standard) bus computers • ISA Adapter for SysKonnect FDDI NICs designed for installation in ISA (Industry Standard) bus computers • PCI Adapter for SysKonnect FDDI NICs designed for installation in PCI (Peri ...
pptx - Department of Computer Science
... A logical network built on top of a physical network Overlay links are tunnels through the underlying network Many logical networks may coexist at once Over the same underlying network And providing its own particular service Nodes are often end hosts Acting as intermediate nodes that ...
... A logical network built on top of a physical network Overlay links are tunnels through the underlying network Many logical networks may coexist at once Over the same underlying network And providing its own particular service Nodes are often end hosts Acting as intermediate nodes that ...