Chapter 6 - YSU Computer Science & Information Systems
... there is a neighbor table for each protocol that EIGRP supports used to support reliable, sequenced delivery of packets • One field in each row of the table is populated with the last sequence number of the packet received from that neighbor • EIGRP uses this field for two purposes: – Sequence num ...
... there is a neighbor table for each protocol that EIGRP supports used to support reliable, sequenced delivery of packets • One field in each row of the table is populated with the last sequence number of the packet received from that neighbor • EIGRP uses this field for two purposes: – Sequence num ...
AirLive AP60 Manual
... with your country regulation. Please do not use more power than allowed in your country. Versatile Management The AP60 comes with a user friendly interface that can access through web browser. There is a setup wizard to help you setup quickly. The IP finder utility can help you to find your AP. Whet ...
... with your country regulation. Please do not use more power than allowed in your country. Versatile Management The AP60 comes with a user friendly interface that can access through web browser. There is a setup wizard to help you setup quickly. The IP finder utility can help you to find your AP. Whet ...
NETGEAR Wireless Router Setup Manual
... residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular ...
... residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular ...
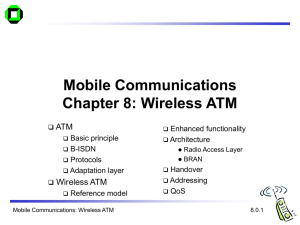
Mobile Communications
... Task: development of specifications to enable the use of ATM technology also for wireless networks with a large coverage of current network scenarios (private and public, local and global) compatibility to existing ATM Forum standards important it should be possible to easily upgrade existing ATM ne ...
... Task: development of specifications to enable the use of ATM technology also for wireless networks with a large coverage of current network scenarios (private and public, local and global) compatibility to existing ATM Forum standards important it should be possible to easily upgrade existing ATM ne ...
Multicast Routing Algos
... Reliability : Pagani et al • These guarantees hold only as long as there is : • Eventual Subsidence : For each m, eventually no more messages are generated regarding m • Liveness : Each mobile is connected for at least a given time to its clusterhead • Clusterhead Stability : A node chosen as the c ...
... Reliability : Pagani et al • These guarantees hold only as long as there is : • Eventual Subsidence : For each m, eventually no more messages are generated regarding m • Liveness : Each mobile is connected for at least a given time to its clusterhead • Clusterhead Stability : A node chosen as the c ...
EARNEST and the e-IRG
... new topics in e-Infrastructure (RN, Grid, testbeds, libraries, research...) general political importance of the field increases seamless pan-European end-to-end connectivity needed geographical coverage of the pan-European network widening digital divide to be narrowed testing, piloting and introduc ...
... new topics in e-Infrastructure (RN, Grid, testbeds, libraries, research...) general political importance of the field increases seamless pan-European end-to-end connectivity needed geographical coverage of the pan-European network widening digital divide to be narrowed testing, piloting and introduc ...
document
... Autonomous system - group of router exchanging routing info using same routing protocol Area - set of routers and networks that have the same area designation, each router in an area has same info Neighbors - two routers that share a common network, discover and exchange routing info across it Hello ...
... Autonomous system - group of router exchanging routing info using same routing protocol Area - set of routers and networks that have the same area designation, each router in an area has same info Neighbors - two routers that share a common network, discover and exchange routing info across it Hello ...
21-04-0164-04-0000-Freescale_March2005
... the right to add, amend or withdraw material contained herein. The contributor grants a free, irrevocable license to the IEEE to incorporate material contained in this contribution, and any modifications thereof, in the creation of an IEEE Standards publication; to copyright in the IEEE’s name any I ...
... the right to add, amend or withdraw material contained herein. The contributor grants a free, irrevocable license to the IEEE to incorporate material contained in this contribution, and any modifications thereof, in the creation of an IEEE Standards publication; to copyright in the IEEE’s name any I ...
Network Programming
... – Used by some network utility applications to communicate with the remote host on the network – Examples: ping and traceroute ...
... – Used by some network utility applications to communicate with the remote host on the network – Examples: ping and traceroute ...
FiOS Gateway USER GUIDE - Frontier Communications
... • Reset Button - allows you to reset your Gateway to the factory default settings. To reset the Gateway, press and hold the Reset button for at least three seconds. • Ethernet LAN - connects devices to your Gateway using Ethernet cables to join the local area network (LAN). The four Ethernet LAN ...
... • Reset Button - allows you to reset your Gateway to the factory default settings. To reset the Gateway, press and hold the Reset button for at least three seconds. • Ethernet LAN - connects devices to your Gateway using Ethernet cables to join the local area network (LAN). The four Ethernet LAN ...
Aalborg Universitet HomePort ZigBee Adapter
... looking for the start and end bytes of the messages and verifying that the length matches. If the length does not match, we assume that we are in the middle of a partially received message and skips ahead until the next start byte. C. Develco Layer (SmartAMM, Modem, Develco) SmartAMM parses the Smar ...
... looking for the start and end bytes of the messages and verifying that the length matches. If the length does not match, we assume that we are in the middle of a partially received message and skips ahead until the next start byte. C. Develco Layer (SmartAMM, Modem, Develco) SmartAMM parses the Smar ...
Chapter 4 IP Addresses: Classful Addressing
... A LAN: 220.3.6.0: Class C An LAN: 134.18.0.0: Class B An LAN: 124.0.0.0: Class A A point-to-point WAN, for example a T-1 line n n ...
... A LAN: 220.3.6.0: Class C An LAN: 134.18.0.0: Class B An LAN: 124.0.0.0: Class A A point-to-point WAN, for example a T-1 line n n ...
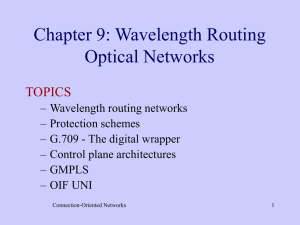
Chapter 9: Wavelength Routing Optical Networks
... • Protection can be done at both the fiber level or at the lightpath level. • Fiber protection switching is used to restore a network failure caused by a fiber cut or a failure of an optical amplifier. Lightpath protection switching is used to restore a lightpath that failed due to a transmitter or ...
... • Protection can be done at both the fiber level or at the lightpath level. • Fiber protection switching is used to restore a network failure caused by a fiber cut or a failure of an optical amplifier. Lightpath protection switching is used to restore a lightpath that failed due to a transmitter or ...
Ubee DDW36C Advanced Wireless Gateway
... On Green – An Ethernet device is connected to the device at 1000 Mbps speeds (Gigabit Ethernet). On Orange – An Ethernet device is connected to the device at 10/100 Mbps speeds. Flashes (in Green or Orange) – When data is being passed between the cable modem and the connected device. The Ethernet po ...
... On Green – An Ethernet device is connected to the device at 1000 Mbps speeds (Gigabit Ethernet). On Orange – An Ethernet device is connected to the device at 10/100 Mbps speeds. Flashes (in Green or Orange) – When data is being passed between the cable modem and the connected device. The Ethernet po ...
View
... • Other constraints we need to take into account – destination-based routing: not pair-based!
– multiple shortest paths (“equal-cost” paths, ECPs) may
exist and can be used for load-balancing
• But typical equal splitting is used to split traffic among ECPs
for a given destination prefix
...
... • Other constraints we need to take into account – destination-based routing: not
IT Management System Scalability for the Enterprise
... An information service (IS) which will provide a single point of communication and query the servers ...
... An information service (IS) which will provide a single point of communication and query the servers ...
Data Sheet UMUX NEBRA/NEBRO
... the UMUX multi-service access platform offers cost effective Fast Ethernet and Gigabit Ethernet connectivity combined with the proven reliability and manageability of SDH networks. This makes it ideal for bandwidth intensive point-to-point applications like corporate internet access, LAN interconnec ...
... the UMUX multi-service access platform offers cost effective Fast Ethernet and Gigabit Ethernet connectivity combined with the proven reliability and manageability of SDH networks. This makes it ideal for bandwidth intensive point-to-point applications like corporate internet access, LAN interconnec ...
FIREWALLS
... must pass. A firewall security policy dictates which traffic is authorized to pass in each direction. A firewall may be designed to operate as a filter at the level of IP packets, or may operate at a higher protocol layer. ...
... must pass. A firewall security policy dictates which traffic is authorized to pass in each direction. A firewall may be designed to operate as a filter at the level of IP packets, or may operate at a higher protocol layer. ...
Interconnecting Devices
... Multiple Hubs can be used to extend the network length For 10BaseT and 100BaseT the maximum length of the connection between an adapter and the hub is 100 meters the maximum length between any two nodes is 200 m = maximum network length ©The McGraw-Hill Companies, Inc., 2004 ...
... Multiple Hubs can be used to extend the network length For 10BaseT and 100BaseT the maximum length of the connection between an adapter and the hub is 100 meters the maximum length between any two nodes is 200 m = maximum network length ©The McGraw-Hill Companies, Inc., 2004 ...
TL-WN7200N 150Mbps High Power Wireless USB Adapter - TP-Link
... compliance. This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter. This equipment has been SAR-evaluated for use in hand. SAR measurements are based on a 5mm spacing from the body and that compliance is achieved at that distance. ...
... compliance. This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter. This equipment has been SAR-evaluated for use in hand. SAR measurements are based on a 5mm spacing from the body and that compliance is achieved at that distance. ...
Avaya Virtual Services Platform 8404
... enables businesses to satisfy many typical deployments scenarios with a consistent hardware platform. Mid-sized businesses are increasingly ...
... enables businesses to satisfy many typical deployments scenarios with a consistent hardware platform. Mid-sized businesses are increasingly ...
Slide 1
... network management tools were specific to that insular environment, if used at all – The advent of the PC and Macintosh made networks get much more heterogeneous, and increased the complexity of network management INFO 331 chapter 9 ...
... network management tools were specific to that insular environment, if used at all – The advent of the PC and Macintosh made networks get much more heterogeneous, and increased the complexity of network management INFO 331 chapter 9 ...
VENDOR PROFILE Tata Communications Ethernet Portfolio and
... believes that emerging markets is its competitive edge over the existing global tier 1s (i.e., AT&T, Verizon Business, Orange Business Services, BT Global Services, TSystems, and Cable & Wireless). Tapping its experiences in its home markets of India and South Africa, as well as its footprints, it h ...
... believes that emerging markets is its competitive edge over the existing global tier 1s (i.e., AT&T, Verizon Business, Orange Business Services, BT Global Services, TSystems, and Cable & Wireless). Tapping its experiences in its home markets of India and South Africa, as well as its footprints, it h ...
Hell of a Handshake: Abusing TCP for Reflective
... NetBIOS transmitted about 25 MB of traffic, while the RST amplifiers caused traffic of more than 12 GB. Similarly, even though we observed most of the FTP amplifiers sending SYN/ACK packets (causing a total of 3.2 GB of traffic), the RST amplifiers transferred 15.1 GB of traffic in the same amount o ...
... NetBIOS transmitted about 25 MB of traffic, while the RST amplifiers caused traffic of more than 12 GB. Similarly, even though we observed most of the FTP amplifiers sending SYN/ACK packets (causing a total of 3.2 GB of traffic), the RST amplifiers transferred 15.1 GB of traffic in the same amount o ...
WWW.BSSVE.IN
... 1962, J.C.R. Licklider was hired and developed a working group he called the "Intergalactic Network", a precursor to the ARPANet. In 1964, researchers at Dartmouth developed the Dartmouth Time Sharing System for distributed users of large computer systems. The same year, at MIT, a research group sup ...
... 1962, J.C.R. Licklider was hired and developed a working group he called the "Intergalactic Network", a precursor to the ARPANet. In 1964, researchers at Dartmouth developed the Dartmouth Time Sharing System for distributed users of large computer systems. The same year, at MIT, a research group sup ...