Chapter 4 Review Questions
... guaranteed maximum jitter. None of these services is provided by the Internet’s network layer. ATM’s CBR service provides both guaranteed delivery and timing. ABR does not provide any of these services. 6. Interactive live multimedia applications, such as IP telephony and video conference, could ben ...
... guaranteed maximum jitter. None of these services is provided by the Internet’s network layer. ATM’s CBR service provides both guaranteed delivery and timing. ABR does not provide any of these services. 6. Interactive live multimedia applications, such as IP telephony and video conference, could ben ...
The OSI Model - Institute of Technology Sligo
... • LCC (Logical Link Control) sublayer • Manages communication between devices over a single link of a network. • Enables multiple higher-layer protocols to share a single physical data link. • MAC sublayer • Manages protocol access to the physical network medium. • Determines hardware addresses. ...
... • LCC (Logical Link Control) sublayer • Manages communication between devices over a single link of a network. • Enables multiple higher-layer protocols to share a single physical data link. • MAC sublayer • Manages protocol access to the physical network medium. • Determines hardware addresses. ...
Proposal for 802.21 solution
... the HMH function in the handover decision making process • The HMC layer relays the formatted event indications to HMH through an event service to be defined • Higher Layer Mobility Protocols will be consumers of the HMH function provided information • HMH function messages to Higher Layer Mobility ...
... the HMH function in the handover decision making process • The HMC layer relays the formatted event indications to HMH through an event service to be defined • Higher Layer Mobility Protocols will be consumers of the HMH function provided information • HMH function messages to Higher Layer Mobility ...
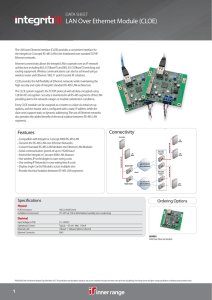
LAN Over Ethernet Module (CLOE)
... The LAN over Ethernet Interface (CLOE) provides a convenient interface for the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U ( ...
... The LAN over Ethernet Interface (CLOE) provides a convenient interface for the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U ( ...
OSI Model Review Layer 1
... • The network layer (Layer 3) deals with higherlevel addressing schemes and path determination. The network layer address is the Internet Protocol (IP) address of a computer. • Each computer on a network has an IP address to identify its location on the network. It indicates to which network and sub ...
... • The network layer (Layer 3) deals with higherlevel addressing schemes and path determination. The network layer address is the Internet Protocol (IP) address of a computer. • Each computer on a network has an IP address to identify its location on the network. It indicates to which network and sub ...
FRF.6 - Broadband Forum
... This agreement applies to Frame Relay network service providers that wish to provide their customers with a customer network management (CNM) capability, and to Frame Relay network service customers that wish to perform network management functions on the services provided to them. It shall be imple ...
... This agreement applies to Frame Relay network service providers that wish to provide their customers with a customer network management (CNM) capability, and to Frame Relay network service customers that wish to perform network management functions on the services provided to them. It shall be imple ...
HWBA54G Manual
... 802.11g wireless standard and operates at transfer speeds up to 54Mbps. It is backwards compatible current 802.11b wireless hardware. The Hi-Speed 54G Wireless AP/Bridge utilizes the highest wireless security standards (WPA) to protect your network from outside intruders. The unique multi-function ...
... 802.11g wireless standard and operates at transfer speeds up to 54Mbps. It is backwards compatible current 802.11b wireless hardware. The Hi-Speed 54G Wireless AP/Bridge utilizes the highest wireless security standards (WPA) to protect your network from outside intruders. The unique multi-function ...
The HENP Working Group
... Centers as needed, so that the ensemble of research networks is able to work efficiently and provide the high level of capability required. Contact: Jim Williams (IndianaU)/
Slide 15
...
... Centers as needed, so that the ensemble of research networks is able to work efficiently and provide the high level of capability required. Contact: Jim Williams (IndianaU)/
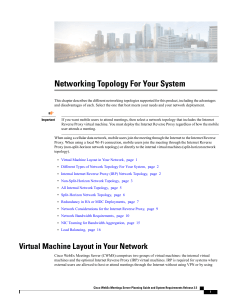
Networking Topology For Your System
... • A 50 user system consists of an Admin virtual machine and optionally an Internet Reverse Proxy (IRP) virtual machine for public access. If you add a HA (MDC is not available) system, the combined 50 user system consists of two Admin virtual machines and two IRP virtual machines. • A primary 250 or ...
... • A 50 user system consists of an Admin virtual machine and optionally an Internet Reverse Proxy (IRP) virtual machine for public access. If you add a HA (MDC is not available) system, the combined 50 user system consists of two Admin virtual machines and two IRP virtual machines. • A primary 250 or ...
for overlay networks
... size and number of groups that can be supported – IP Multicast is still plagued with concerns pertaining to scalability, network management, deployment and support for error, flow and ...
... size and number of groups that can be supported – IP Multicast is still plagued with concerns pertaining to scalability, network management, deployment and support for error, flow and ...
Ethernet, IP, PoE How do you Test?
... address for data frames. Think of it as a mailing address, they change over time. LAN Local Area Network - a group of Ethernet devices that communicate in a geographical area typically as large as a campus. MAC Address Media Access Controller Address - The permanent hardware ID of a device. Every Et ...
... address for data frames. Think of it as a mailing address, they change over time. LAN Local Area Network - a group of Ethernet devices that communicate in a geographical area typically as large as a campus. MAC Address Media Access Controller Address - The permanent hardware ID of a device. Every Et ...
3rd Edition: Chapter 4
... (“fragmented”) within net one datagram becomes several datagrams “reassembled” only at final destination (before given to transport layer) IP header bits used to identify, order related ...
... (“fragmented”) within net one datagram becomes several datagrams “reassembled” only at final destination (before given to transport layer) IP header bits used to identify, order related ...
Data Networks, Summer 2007 Homework #1
... you wish to transfer an n-byte file along a path composed of the source, destination, five point-to-point links, and four switches. Suppose each link has a propagation delay of 1 ms, bandwidth of 3 Mbps, and that the switches support both circuit and packet switching. Thus you can either break the f ...
... you wish to transfer an n-byte file along a path composed of the source, destination, five point-to-point links, and four switches. Suppose each link has a propagation delay of 1 ms, bandwidth of 3 Mbps, and that the switches support both circuit and packet switching. Thus you can either break the f ...
Brocade CNA in Virtualized Environments
... based on the L2 header—primarily MAC address and/or VLAN tags. VMOP multiplexes and demultiplexes workloads based on this distribution logic. Moreover, each VMOP queue is assigned an MSI-X interrupt vector to distribute the workload across multiple processors. VMOP requires no user configuration and ...
... based on the L2 header—primarily MAC address and/or VLAN tags. VMOP multiplexes and demultiplexes workloads based on this distribution logic. Moreover, each VMOP queue is assigned an MSI-X interrupt vector to distribute the workload across multiple processors. VMOP requires no user configuration and ...
Chapter 4 Network Layer CMPT 371 Data Communications
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination host ID) every router on source-dest path maintains “state” for ...
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination host ID) every router on source-dest path maintains “state” for ...
Network Layer
... inefficient use of address space, address space exhaustion e.g., class B net allocated enough addresses for 65K hosts, even if only 2K hosts in that network ...
... inefficient use of address space, address space exhaustion e.g., class B net allocated enough addresses for 65K hosts, even if only 2K hosts in that network ...
Chapter 18 - Personal.kent.edu
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
Manual - Maxon Australia
... Change or modification without the express consent of Maxon Australia Pty Ltd voids the user’s authority to use the equipment. These limits are designed to provide reasonable protection against harmful interference in an appropriate installation. The modem is a transmitting device with similar outpu ...
... Change or modification without the express consent of Maxon Australia Pty Ltd voids the user’s authority to use the equipment. These limits are designed to provide reasonable protection against harmful interference in an appropriate installation. The modem is a transmitting device with similar outpu ...