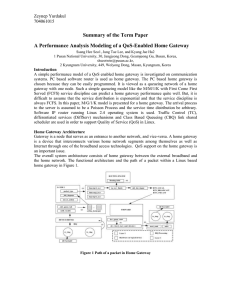
A performance analysis modeling of a QoS
... was dropped. This means that the QoS mechanism was achieved. Since the UDP1 traffic has the lowest priority although the UDP1 traffic has the lowest sending rate. Also, UDP1 and VoIP traffic were dropped at 1.7M. But, the UDP0 traffic was not, because of the drop of VoIP traffic. As greater bandwidt ...
... was dropped. This means that the QoS mechanism was achieved. Since the UDP1 traffic has the lowest priority although the UDP1 traffic has the lowest sending rate. Also, UDP1 and VoIP traffic were dropped at 1.7M. But, the UDP0 traffic was not, because of the drop of VoIP traffic. As greater bandwidt ...
performance analysis of wdm optical shuffle – exchange
... teleconferencing, e-mail, and multimedia, which require high bandwidth, and scalable data services. By allowing several channels to be routed on the same fibre on different wavelengths, the capacity of each link is increased tremendously. Thus, WDM permits use of enormous fiber bandwidth by providin ...
... teleconferencing, e-mail, and multimedia, which require high bandwidth, and scalable data services. By allowing several channels to be routed on the same fibre on different wavelengths, the capacity of each link is increased tremendously. Thus, WDM permits use of enormous fiber bandwidth by providin ...
3rd Edition: Chapter 4
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Chapter 18 - Personal.kent.edu
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
Chapter 5
... Programs that implement Layer 2 protocols use physical addresses, or MAC addresses. Programs that implement Layer 3, 4, and 5 protocols use logical addresses, or IP addresses. ...
... Programs that implement Layer 2 protocols use physical addresses, or MAC addresses. Programs that implement Layer 3, 4, and 5 protocols use logical addresses, or IP addresses. ...
Manual - Maxon Australia
... Change or modification without the express consent of Maxon Australia Pty Ltd voids the user’s authority to use the equipment. These limits are designed to provide reasonable protection against harmful interference in an appropriate installation. The modem is a transmitting device with similar outpu ...
... Change or modification without the express consent of Maxon Australia Pty Ltd voids the user’s authority to use the equipment. These limits are designed to provide reasonable protection against harmful interference in an appropriate installation. The modem is a transmitting device with similar outpu ...
Adaptive QoS Framework for Multimedia in Wireless Networks and
... movement suboptimal VCs or VCs with loops might result. These are detected by the information received in the feedback packets and VCs are updated appropriately by the new SN. ...
... movement suboptimal VCs or VCs with loops might result. These are detected by the information received in the feedback packets and VCs are updated appropriately by the new SN. ...
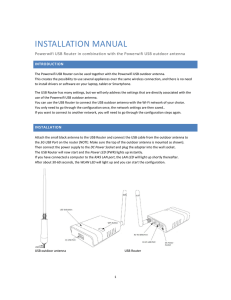
installation manual
... configuration you should not enter a password, a username and password should be provided afterwards at a special Hotspot login page where you should be automatically redirected when launching a browser. Depending on the Hotspot settings you might need an extra password for every additional device. ...
... configuration you should not enter a password, a username and password should be provided afterwards at a special Hotspot login page where you should be automatically redirected when launching a browser. Depending on the Hotspot settings you might need an extra password for every additional device. ...
COMPARATIVE STUDY OF TABLE DRIVEN ROUTING Mr. Pradip A. Chougule
... Comparative Study Of Table Driven routing protocols In Ad Hoc Wireless Networks 3.1.1. Normalized routing overhead: This is the number of routing packets transmitted per delivery of a data packet. Each hop transmission of a routing packet is counted as one transmission. This factor also tells us so ...
... Comparative Study Of Table Driven routing protocols In Ad Hoc Wireless Networks 3.1.1. Normalized routing overhead: This is the number of routing packets transmitted per delivery of a data packet. Each hop transmission of a routing packet is counted as one transmission. This factor also tells us so ...
Chapter 1 Lecture Presentation
... TCP provides connection-oriented reliable byte transfer service UDP provides best-effort datagram service ...
... TCP provides connection-oriented reliable byte transfer service UDP provides best-effort datagram service ...
Physical and Link Layers
... Collision detection and retransmission with back-off was first used in the ALOHA MAC algorithm from the University of Hawaii (1970) for access to satellite channels ...
... Collision detection and retransmission with back-off was first used in the ALOHA MAC algorithm from the University of Hawaii (1970) for access to satellite channels ...
1 Which of the following devices can we use to segment our lan
... 29 A border router Z is connected to three internal routers A, B, C. Subnets connected to router A are 200.168.98.0/24, 200.168.99.0/24. Subnets connected to router B are 200.168.100.0/24, 200.168.101.0/24, 200.168.102.0/24. The subnet connected router C is 200.168.105.0/24. After route summarizatio ...
... 29 A border router Z is connected to three internal routers A, B, C. Subnets connected to router A are 200.168.98.0/24, 200.168.99.0/24. Subnets connected to router B are 200.168.100.0/24, 200.168.101.0/24, 200.168.102.0/24. The subnet connected router C is 200.168.105.0/24. After route summarizatio ...
1 Which of the following devices can we use to segment our lan
... 19 Which command will configure a default route on a router? D (A) ip route 0.0.0.0. 10.1.1.0 10.1.1.1 (B) ip default-route 10.1.1.0 (C) ip default-gateway 10.1.1.0 (D) ip route 0.0.0.0 0.0.0.0 10.1.1.1 20 You are given a PC, a router, and a cable. Select the correct combination that will allow you ...
... 19 Which command will configure a default route on a router? D (A) ip route 0.0.0.0. 10.1.1.0 10.1.1.1 (B) ip default-route 10.1.1.0 (C) ip default-gateway 10.1.1.0 (D) ip route 0.0.0.0 0.0.0.0 10.1.1.1 20 You are given a PC, a router, and a cable. Select the correct combination that will allow you ...
PowerPoint Presentation - Defense-in
... – Host Posture Verification – The ability to make sure that the host posture (virus definitions, patches, firewalls, etc.) match the policy of the network for which it is destined. – Host Remediation – The placement of the host into the correct ...
... – Host Posture Verification – The ability to make sure that the host posture (virus definitions, patches, firewalls, etc.) match the policy of the network for which it is destined. – Host Remediation – The placement of the host into the correct ...
Data communications and enterprise networking
... factors. Firstly, there is a need to exchange information. For most of mankind’s history the speed at which information could be shared over a long distance depended on how fast a messenger could run or ride a horse. More sophisticated methods did evolve to transmit limited information such as the u ...
... factors. Firstly, there is a need to exchange information. For most of mankind’s history the speed at which information could be shared over a long distance depended on how fast a messenger could run or ride a horse. More sophisticated methods did evolve to transmit limited information such as the u ...
Lab 1.1.4 Calculating VLSM Subnets
... Use variable-length subnet mask (VLSM) to support more efficient use of the assigned IP addresses and to reduce the amount of routing information at the top level. The solution to this VLSM lab is provided in the steps themselves. Students should take the recommended subnetting in each step and buil ...
... Use variable-length subnet mask (VLSM) to support more efficient use of the assigned IP addresses and to reduce the amount of routing information at the top level. The solution to this VLSM lab is provided in the steps themselves. Students should take the recommended subnetting in each step and buil ...
UGL2454-APXR
... Point) and Bridge (Point to Multi-Point) modes The 2.4GHz 802.11g/b Wireless Access Point with Super-G function boost ...
... Point) and Bridge (Point to Multi-Point) modes The 2.4GHz 802.11g/b Wireless Access Point with Super-G function boost ...
Chapter 2 Introduction
... The 54 Mbps Wireless Router WGR614 v6 with 4-port switch connects your local area network (LAN) to the Internet through an external access device such as a cable modem or DSL modem. The WGR614 v6 router provides you with multiple Web content filtering options, plus browsing activity reporting and in ...
... The 54 Mbps Wireless Router WGR614 v6 with 4-port switch connects your local area network (LAN) to the Internet through an external access device such as a cable modem or DSL modem. The WGR614 v6 router provides you with multiple Web content filtering options, plus browsing activity reporting and in ...
Some of the forces driving WLAN (re)design
... • VLANs split up L2 subnets to control excessive broadcast & multicast traffic • We sometimes use VLANs to segregate traffic for security • VLANs can help us manage geographically distributed networks (addresses imply location) • We sometimes use VLANs to segregate services and QoS • We’ve always do ...
... • VLANs split up L2 subnets to control excessive broadcast & multicast traffic • We sometimes use VLANs to segregate traffic for security • VLANs can help us manage geographically distributed networks (addresses imply location) • We sometimes use VLANs to segregate services and QoS • We’ve always do ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... header, adding a field identifying all the nodes path information from source node to destination [21]. ...
... header, adding a field identifying all the nodes path information from source node to destination [21]. ...
802.1Qau Flow ID choices
... The Regions choose which NNI (shown by a heavy red line) is used for each service. Each Node in the Buffer Network, whether real or virtual, must exist, so that data can be reliably delivered from NNI to NNI. ...
... The Regions choose which NNI (shown by a heavy red line) is used for each service. Each Node in the Buffer Network, whether real or virtual, must exist, so that data can be reliably delivered from NNI to NNI. ...