project report
... output (since traceroute is inherently ‘hacky’, sometimes weirdness appears in the output). In the worst case, as long as an ip-like thing can be found, and at least one millisecond delay time, the line will be used, and that intermediate router’s information will be added to the netgraph. Otherwise ...
... output (since traceroute is inherently ‘hacky’, sometimes weirdness appears in the output). In the worst case, as long as an ip-like thing can be found, and at least one millisecond delay time, the line will be used, and that intermediate router’s information will be added to the netgraph. Otherwise ...
Document
... They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Note
... To find the type of the address, we need to look at the second hexadecimal digit from the left. If it is even, the address is unicast. If it is odd, the address is multicast. If all digits are F’s, the address is broadcast. Therefore, we have the following: a. This is a unicast address because A in ...
... To find the type of the address, we need to look at the second hexadecimal digit from the left. If it is even, the address is unicast. If it is odd, the address is multicast. If all digits are F’s, the address is broadcast. Therefore, we have the following: a. This is a unicast address because A in ...
ppt - Virginia Tech
... • Supply: vaccines may not be ready; antiviral stockpile; production capacity; available leave days • Compliance: not all individuals will be able or willing to comply with an intervention policy • Cost: drug cost; productivity loss • Delay: vaccine takes a few days to become effective ...
... • Supply: vaccines may not be ready; antiviral stockpile; production capacity; available leave days • Compliance: not all individuals will be able or willing to comply with an intervention policy • Cost: drug cost; productivity loss • Delay: vaccine takes a few days to become effective ...
Analyzing Cross-layer Interaction in Overlay Networks
... Knobs for better control over the cross-layer interaction Analysis and mitigation of the conflict in objective between native and overlay layers: ...
... Knobs for better control over the cross-layer interaction Analysis and mitigation of the conflict in objective between native and overlay layers: ...
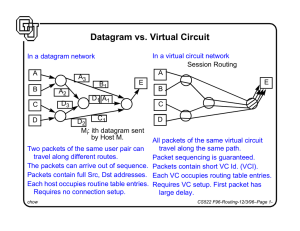
Datagram vs. Virtual Circuit
... Network Operation Center (NOC) collects information from individual nodes NOC carries out the least cost routing algorithms. NOC distributed the routing information to individual nodes. The above steps are carried out periodically. Flooding A node sends/relays a message along all its outgoing links. ...
... Network Operation Center (NOC) collects information from individual nodes NOC carries out the least cost routing algorithms. NOC distributed the routing information to individual nodes. The above steps are carried out periodically. Flooding A node sends/relays a message along all its outgoing links. ...
GPRS - MobiHealth
... GPRS Characteristics • GPRS is a new technology that optimises the use of network and radio resources: – Users share radio resources. – Only used when data are sent or received. – Uses a packet-mode technique to transfer data and signalling in an efficient manner. • GPRS data transfer is based on t ...
... GPRS Characteristics • GPRS is a new technology that optimises the use of network and radio resources: – Users share radio resources. – Only used when data are sent or received. – Uses a packet-mode technique to transfer data and signalling in an efficient manner. • GPRS data transfer is based on t ...
pptx
... preferring routes learned from Customers over those learned from Peers over those learned from Providers. – In the import filter for Customers, set LOCAL_PREF high (e.g. 90) – In the import filter for Peers, set LOCAL_PREF high (e.g. 90) – In the import filter for Providers, set LOCAL_PREF high (e.g ...
... preferring routes learned from Customers over those learned from Peers over those learned from Providers. – In the import filter for Customers, set LOCAL_PREF high (e.g. 90) – In the import filter for Peers, set LOCAL_PREF high (e.g. 90) – In the import filter for Providers, set LOCAL_PREF high (e.g ...
Technology Infrastructure: The Internet and the World Wide Web
... – Provides service speeds of 128 Kbps and upward in 128-Kbps increments ...
... – Provides service speeds of 128 Kbps and upward in 128-Kbps increments ...
Chapter 4 slides
... Router Architecture Overview Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
... Router Architecture Overview Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
Understanding Ethernet Switches and Routers
... Ethernet networks incorporate twisted-pair cabling. If the path is too long, a repeater can be used to extend distance. If fibre optic cable is preferred, media converters can be used. If multiple devices need to share the connection, a repeating hub (commonly called just a hub) is used. All three o ...
... Ethernet networks incorporate twisted-pair cabling. If the path is too long, a repeater can be used to extend distance. If fibre optic cable is preferred, media converters can be used. If multiple devices need to share the connection, a repeating hub (commonly called just a hub) is used. All three o ...
Powerpoint
... If there aren’t enough queries from local peers, left over capacity is used for remote peer’s queries (queries received from other supernodes). ...
... If there aren’t enough queries from local peers, left over capacity is used for remote peer’s queries (queries received from other supernodes). ...
Wireless Sensor Networks 巨型机说:“我认为全球大概只需要五台
... • Sensor nodes can self organize to form a sensor network • Data are collected by these scattered nodes and routed back to the sink in a multi-hop way • The user communicate with the sink via Internet ...
... • Sensor nodes can self organize to form a sensor network • Data are collected by these scattered nodes and routed back to the sink in a multi-hop way • The user communicate with the sink via Internet ...
A Rapidly Deployable Radio Network
... The main objective of the RDRN architecture is to use an adaptive point-to-point topology to gain the advantages of ATM for wireless networks. Figure 1 shows a high-level view of the RDRN system which is made up of two types of nodes: Remote Nodes (RNs) to provide wireless ATM access to end-users an ...
... The main objective of the RDRN architecture is to use an adaptive point-to-point topology to gain the advantages of ATM for wireless networks. Figure 1 shows a high-level view of the RDRN system which is made up of two types of nodes: Remote Nodes (RNs) to provide wireless ATM access to end-users an ...
Research on Performance Evaluation Model Based on Improved
... ombudsman, which may examine each employee's work effectiveness. Therefore, it is a kind of control system, according to the performance evaluation standards, enable managers to identify what kind of employees can mount guard, what kind of employees can stay and what kind of employees should be laid ...
... ombudsman, which may examine each employee's work effectiveness. Therefore, it is a kind of control system, according to the performance evaluation standards, enable managers to identify what kind of employees can mount guard, what kind of employees can stay and what kind of employees should be laid ...
3rd Edition: Chapter 4
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). ...
File
... • X.25 is a standard packet switching protocol that has been widely used in WAN. • X.25 is a standard for interface between the host system with the packet switching network in which it defines how DTE is connected and communicates with packet switching network. • It uses a virtual circuit approach ...
... • X.25 is a standard packet switching protocol that has been widely used in WAN. • X.25 is a standard for interface between the host system with the packet switching network in which it defines how DTE is connected and communicates with packet switching network. • It uses a virtual circuit approach ...
IP address
... – Largest percentage of all backbone, metropolitan, and wide area networks use TCP/IP – Most commonly used protocol on LANs ...
... – Largest percentage of all backbone, metropolitan, and wide area networks use TCP/IP – Most commonly used protocol on LANs ...
Document
... • Subnet addresses include the Class A, Class B, or Class C network portion, plus a subnet field and a host field. • To create a subnet address, a network administrator borrows bits from the original host portion and designates them as the subnet field. • Subnet addresses are assigned locally, usual ...
... • Subnet addresses include the Class A, Class B, or Class C network portion, plus a subnet field and a host field. • To create a subnet address, a network administrator borrows bits from the original host portion and designates them as the subnet field. • Subnet addresses are assigned locally, usual ...
Physical plane for Intelligent Network Capability Set 2
... The SN can control IN-based services and engage in flexible information interactions with users. The SN communicates directly with one or more SSPs, each with a point-to-point signalling and transport connection. Functionally, the SN contains an SCF, SDF, SRF, and an SSF/CCF. This SSF/CCF is closely ...
... The SN can control IN-based services and engage in flexible information interactions with users. The SN communicates directly with one or more SSPs, each with a point-to-point signalling and transport connection. Functionally, the SN contains an SCF, SDF, SRF, and an SSF/CCF. This SSF/CCF is closely ...
Pocket Guide - Industrial Networking Solutions
... Asynchronous Transfer Mode. International standard for cell relay in which multiple service types (such as voice, video, or data) are conveyed in fixed-length (53-byte) cells. Mainly used in WAN applications. ...
... Asynchronous Transfer Mode. International standard for cell relay in which multiple service types (such as voice, video, or data) are conveyed in fixed-length (53-byte) cells. Mainly used in WAN applications. ...
ch05 - The University of Texas at Dallas
... Internet Protocol (IP) • Responsible for addressing and routing of packets • Two versions in current in use – IPv4: a 192 bit (24 byte) header, uses 32 bit addresses. – IPv6: Mainly developed to increase IP address space due to the huge growth in Internet usage (128 bit ...
... Internet Protocol (IP) • Responsible for addressing and routing of packets • Two versions in current in use – IPv4: a 192 bit (24 byte) header, uses 32 bit addresses. – IPv6: Mainly developed to increase IP address space due to the huge growth in Internet usage (128 bit ...
The Nightingale-Bamford School
... must be in support of education and research and be consistent with the educational objectives of Nightingale. If Nightingale provides you with a laptop computer, the laptop computer is considered part of the Nightingale network and all of the above conditions apply. The laptop and any information o ...
... must be in support of education and research and be consistent with the educational objectives of Nightingale. If Nightingale provides you with a laptop computer, the laptop computer is considered part of the Nightingale network and all of the above conditions apply. The laptop and any information o ...