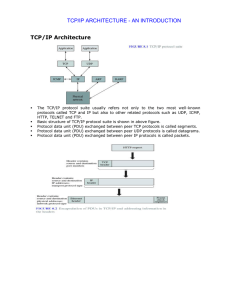
TCP/IP Architecture TCP/IP ARCHITECTURE
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
... Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are serial number o 00:90:27:96:68:07 12 hex numbers ...
Security Tools
... modifications to a specific account or group. Without the /E switch, your settings will replace the current security with only what is specified. ...
... modifications to a specific account or group. Without the /E switch, your settings will replace the current security with only what is specified. ...
VitalQIP™ DNS/DHCP and IP Management Software
... management system, extending your capabilities and increasing the return on your network investment. Choose from a full range of available management modules to augment the value and versatility of your VitalQIP™ software solution: • Network Allocator is ideal for customers needing to define and dep ...
... management system, extending your capabilities and increasing the return on your network investment. Choose from a full range of available management modules to augment the value and versatility of your VitalQIP™ software solution: • Network Allocator is ideal for customers needing to define and dep ...
Chapter 1 notes
... of paper and a pencil. Users simply “write” on the screen with a device called a stylus. ...
... of paper and a pencil. Users simply “write” on the screen with a device called a stylus. ...
What is a Network?
... A Network is a number of electronic devices which are connected so that data is able to be transferred between them. ...
... A Network is a number of electronic devices which are connected so that data is able to be transferred between them. ...
IP Addressing and DNS
... In principle, a single name server could be used to store the entire DNS database and respond to any name lookup requests. However, in practice, this server would be too overloaded to be usable, and should the server go down, then the entire Internet would be crippled. To overcome these problems, th ...
... In principle, a single name server could be used to store the entire DNS database and respond to any name lookup requests. However, in practice, this server would be too overloaded to be usable, and should the server go down, then the entire Internet would be crippled. To overcome these problems, th ...
Ethan Frome - Warrington Collegiate
... students across the Collegiate Education Trust, based at Warrington Collegiate. ...
... students across the Collegiate Education Trust, based at Warrington Collegiate. ...
What can “Economics of Information Security” offer for SMEs
... All the Windows versions and virtual machine platform are available to download using MSDN Guidance in CEHintro.pdf file ...
... All the Windows versions and virtual machine platform are available to download using MSDN Guidance in CEHintro.pdf file ...
Chap9.doc
... True or False. Type in a "T" or "F" in the blank to the left of the question. __ 1. Computer communications refers to the transfer of data, instructions, and information from one computer to another. __ 2. Communication channels include various transmission media, such as cables, telephone lines, an ...
... True or False. Type in a "T" or "F" in the blank to the left of the question. __ 1. Computer communications refers to the transfer of data, instructions, and information from one computer to another. __ 2. Communication channels include various transmission media, such as cables, telephone lines, an ...
組態管理 - Yen-Cheng Chen / 陳彥錚
... Autodiscovery 例子(一) * Suppose the IP Address of NMS is 140.131.59.20 and the network attached is a Class B network (i.e. netmask is 255.255.0.0). => Possible Addresses: 140.131.0.1 ~ 140.131.255.254 * If there exists another network, e.g. 163.25.149.0, interconnected with network 140.131.0.0, there ...
... Autodiscovery 例子(一) * Suppose the IP Address of NMS is 140.131.59.20 and the network attached is a Class B network (i.e. netmask is 255.255.0.0). => Possible Addresses: 140.131.0.1 ~ 140.131.255.254 * If there exists another network, e.g. 163.25.149.0, interconnected with network 140.131.0.0, there ...
Advanced TCP/IP Planning and Design
... Why: Say that you want a LAN network to have more than 254 hosts; a class C network is not sufficient. You can group two Class C networks using supernets. Benefits: Provide more IP addresses to the LAN segment without using secondary IP addresses on the router interface. (How would this effect the ...
... Why: Say that you want a LAN network to have more than 254 hosts; a class C network is not sufficient. You can group two Class C networks using supernets. Benefits: Provide more IP addresses to the LAN segment without using secondary IP addresses on the router interface. (How would this effect the ...
1400241431Mahesh Gur..
... DESCRIPTION: In this project a company having its two HO with multiple branch offices connected with India, using different WAN technologies such as PPP and Frame Relay Company is connected with its offices. Different routing methods are used for transmitting packets b/w different subnetted Network ...
... DESCRIPTION: In this project a company having its two HO with multiple branch offices connected with India, using different WAN technologies such as PPP and Frame Relay Company is connected with its offices. Different routing methods are used for transmitting packets b/w different subnetted Network ...
Notes as Powerpoint Presentation
... Applications/services register to listen for incoming data on the defined port IANA port numbers: http://www.iana.org/assignments/port-numbers 0 to 1023 Well Known ports managed by IANA 1024 to 49151 Registered by IANA as a convenience 49152 to 65535 Dynamic (used for source address) C:\WINDOWS\syst ...
... Applications/services register to listen for incoming data on the defined port IANA port numbers: http://www.iana.org/assignments/port-numbers 0 to 1023 Well Known ports managed by IANA 1024 to 49151 Registered by IANA as a convenience 49152 to 65535 Dynamic (used for source address) C:\WINDOWS\syst ...
EE 3760 chapter 7 - Seattle Pacific University
... • Groups to the left specify the network, others the host • Network address is assigned by InterNIC • Class A: Network.host.host.host • Network is from 1-126, allows up to 16,000,000 hosts ...
... • Groups to the left specify the network, others the host • Network address is assigned by InterNIC • Class A: Network.host.host.host • Network is from 1-126, allows up to 16,000,000 hosts ...
domain name system
... Internet Connections • There are various technologies available that you can use to connect a home computer to the Internet – A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back again into data – A ...
... Internet Connections • There are various technologies available that you can use to connect a home computer to the Internet – A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back again into data – A ...
... Plans and directs the implementation of network infrastructure systems in the Ministry and its dependent agencies; Leads the design/re-design, development and implementation of all network infrastructure projects; Implements and manages enterprise firewall solutions to support a more complex and rob ...
Networking Your Office
... become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is for any and all forms of information and commerce. Internet Web sites now provide personal, educational, political, and economic resources to anyone. ...
... become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is for any and all forms of information and commerce. Internet Web sites now provide personal, educational, political, and economic resources to anyone. ...
Internet Protocol, IP Addressing and Datagrams
... The IP Address Hierarchy • Every host is assigned a globally unique 32-bit address for identification • Each 32-bit address is divided into two distinct parts – prefix: physical network to which a host is attached, also known as network number – suffix: a host attached to a given physical network, ...
... The IP Address Hierarchy • Every host is assigned a globally unique 32-bit address for identification • Each 32-bit address is divided into two distinct parts – prefix: physical network to which a host is attached, also known as network number – suffix: a host attached to a given physical network, ...
ITGS
... heavily on a server not only to store files and applications, but run software on a client’s behalf (sometimes including even the OS) – The thin client merely acts as a terminal for accepting input and displaying output • The client only contains enough software to initialize the hardware and networ ...
... heavily on a server not only to store files and applications, but run software on a client’s behalf (sometimes including even the OS) – The thin client merely acts as a terminal for accepting input and displaying output • The client only contains enough software to initialize the hardware and networ ...
10 the internet and the new information technology infrastructure
... • Incorporates public infrastructure (telephone system, Internet, etc.) ...
... • Incorporates public infrastructure (telephone system, Internet, etc.) ...
Cisco Discovery 1 Module 03 Quiz Picture Descriptions
... packet to reach computer 10. The router checks it ARP table to determine the appropriate IP address of computer 10. The router checks its routing table to determine where to forward the packet to reach computer 10. The router checks its routing table to determine the appropriate MAC address of compu ...
... packet to reach computer 10. The router checks it ARP table to determine the appropriate IP address of computer 10. The router checks its routing table to determine where to forward the packet to reach computer 10. The router checks its routing table to determine the appropriate MAC address of compu ...
Plutarch
... Increasingly difficult to extend IP to support demands of new applications and environments. We propose Plutarch an architecture that eschews homogeneity, allowing independent networks to work together for end-to-end ...
... Increasingly difficult to extend IP to support demands of new applications and environments. We propose Plutarch an architecture that eschews homogeneity, allowing independent networks to work together for end-to-end ...
Understand Computer Network V
... Protocols at the Network Layer • TCP and UDP communicate with the Network layer, which is sometimes called the Internet layer. • Some of the other supporting protocols include ARP (Address Resolution Protocol), responsible for locating a host on a LAN; RARP (Reverse Address Resolution Protocol), re ...
... Protocols at the Network Layer • TCP and UDP communicate with the Network layer, which is sometimes called the Internet layer. • Some of the other supporting protocols include ARP (Address Resolution Protocol), responsible for locating a host on a LAN; RARP (Reverse Address Resolution Protocol), re ...
Communications and networking history and background Internet
... different physical and electrical properties different names and addresses themselves ...
... different physical and electrical properties different names and addresses themselves ...