Slide 1
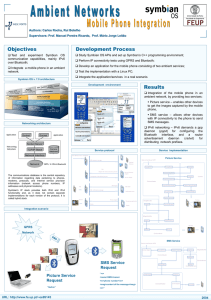
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
Chapter 2
... • Each computer attached to an Ethernet network has a 48-bit address – called Ethernet address, hardware address, physical address, MAC address (media access), or layer 2 address ...
... • Each computer attached to an Ethernet network has a 48-bit address – called Ethernet address, hardware address, physical address, MAC address (media access), or layer 2 address ...
fn-4127-nic network interface card
... the expansion of up to 64 nodes (combination of FACP’s or annuciators) on a single FireNET network wide system. Using the Loop Explorer configuration software up to 64 nodes can be programmed to respond to in a variety ways-independently or system wide. The flexibility extends the comprehensive caus ...
... the expansion of up to 64 nodes (combination of FACP’s or annuciators) on a single FireNET network wide system. Using the Loop Explorer configuration software up to 64 nodes can be programmed to respond to in a variety ways-independently or system wide. The flexibility extends the comprehensive caus ...
Document
... TCP (Transmission Control Protocol) •the primary Internet transport protocol (layer 4) • accepts messages of any length from the upperlayer protocols • provides transportation to a TCP peer • Connection oriented (more reliable than IP) • Port address is used to determine which connection a packet is ...
... TCP (Transmission Control Protocol) •the primary Internet transport protocol (layer 4) • accepts messages of any length from the upperlayer protocols • provides transportation to a TCP peer • Connection oriented (more reliable than IP) • Port address is used to determine which connection a packet is ...
File
... The Nishida Kitchens business and sales unit has 42 computer users. The plant in which the foods are produced, packaged, and shipped has 45 computer users. The company has Windows Server 2003 and Red Hat Enterprise Linux servers. The business and sales unit uses Windows XP Professional and Windows ...
... The Nishida Kitchens business and sales unit has 42 computer users. The plant in which the foods are produced, packaged, and shipped has 45 computer users. The company has Windows Server 2003 and Red Hat Enterprise Linux servers. The business and sales unit uses Windows XP Professional and Windows ...
Session5-Group4-Networking
... is a unique identifier assigned to most network adapters or network interface cards (NICs) by the manufacturer for identification. If assigned by the manufacturer, a MAC address usually encodes the manufacturer's registered identification number ...
... is a unique identifier assigned to most network adapters or network interface cards (NICs) by the manufacturer for identification. If assigned by the manufacturer, a MAC address usually encodes the manufacturer's registered identification number ...
IP_tec - iptel.org
... Special Addresses • Private addresses: Only of meaning inside an intranet ...
... Special Addresses • Private addresses: Only of meaning inside an intranet ...
Ports and IPv6
... Present IPv4 is used This is 32 bits, and has about 4,300,000,000 address spaces (2^32 – 1) IPv6 is started to be implemented. IPv6 is 128 bits giving 3.4 x 10^38 ...
... Present IPv4 is used This is 32 bits, and has about 4,300,000,000 address spaces (2^32 – 1) IPv6 is started to be implemented. IPv6 is 128 bits giving 3.4 x 10^38 ...
networking - Department of Computer Engineering
... WWW(World Wide Web) The first major Improvement to the internet came in 1989 when WWW was created by Tim ...
... WWW(World Wide Web) The first major Improvement to the internet came in 1989 when WWW was created by Tim ...
CS412 Computer Networks - Winona State University
... Simple Mail Transfer Protocol (SMTP) Internet Message Access Protocol (IMAP) Multipurpose Internet Mail Extensions (MIME) ...
... Simple Mail Transfer Protocol (SMTP) Internet Message Access Protocol (IMAP) Multipurpose Internet Mail Extensions (MIME) ...
Plutarch
... There may be a general purpose protocol that solves all these problems. However, if that is the case, we would expect that it would emerge within Plutarch and grow to make all other contexts redundant. ...
... There may be a general purpose protocol that solves all these problems. However, if that is the case, we would expect that it would emerge within Plutarch and grow to make all other contexts redundant. ...
icc_7ds - Columbia University
... What is Zeroconf? • Zero Configuration Networking (Zeroconf) • No Infrastructure – Allocate IP addresses without a DHCP server – Translate between domain names and IP addresses without a DNS Server – Find service without a directory service • A simple and reliable way to configure and browse for se ...
... What is Zeroconf? • Zero Configuration Networking (Zeroconf) • No Infrastructure – Allocate IP addresses without a DHCP server – Translate between domain names and IP addresses without a DNS Server – Find service without a directory service • A simple and reliable way to configure and browse for se ...
Prace semestralne z języka angielskiego : wzory dla studentów
... should travel through backbones. Routers are simply specialized computers that connect smaller networks into larger ones. The backbone is a physical link that connects two networks. Nowadays it is a fiber optic cable that is capable of transmitting information at very high speed ( up to 10 Gbps thro ...
... should travel through backbones. Routers are simply specialized computers that connect smaller networks into larger ones. The backbone is a physical link that connects two networks. Nowadays it is a fiber optic cable that is capable of transmitting information at very high speed ( up to 10 Gbps thro ...
Nauman Parkar
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC ...
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC ...
Eric Kha Professor Shin 4/13/15 Chapter 8 PowerPoint Answer
... TCP/IP (Transmission Control Protocol/Internet Protocol) ...
... TCP/IP (Transmission Control Protocol/Internet Protocol) ...
4_hDNS - take2theweb
... If the local DNS does not contain the IP Address for the requested Domain Name then the request is passed to another DNS server on the Internet and so on until it is ...
... If the local DNS does not contain the IP Address for the requested Domain Name then the request is passed to another DNS server on the Internet and so on until it is ...
CST125 - Suffolk County Community College
... Network transmission modes, Categories of networks, Internetworking. The OSI model. TCP/IP protocol suite. Signals, Encoding and Modulating. Transmission media, Data link control, Error control NOS installation. Hardware compatibility. MS management console and tasks scheduler. Network protocols. Ch ...
... Network transmission modes, Categories of networks, Internetworking. The OSI model. TCP/IP protocol suite. Signals, Encoding and Modulating. Transmission media, Data link control, Error control NOS installation. Hardware compatibility. MS management console and tasks scheduler. Network protocols. Ch ...
TCP_IP_Continued
... TCP Port Number Conventions • TCP Port Numbers are in the range 0 – 65535 • Ports 0 – 1023 are reserved for system services (email, web, etc.) • Ports 1024 – 49151 are registered to particular applications • Ports 49152 – 65535 can be used for custom or temporary purposes • Email servers typically ...
... TCP Port Number Conventions • TCP Port Numbers are in the range 0 – 65535 • Ports 0 – 1023 are reserved for system services (email, web, etc.) • Ports 1024 – 49151 are registered to particular applications • Ports 49152 – 65535 can be used for custom or temporary purposes • Email servers typically ...
The ID/LOC Split - UK Network Operators` Forum
... • Put this all together and your computers know roughly what they want. • They rely on the DNS to get them there most of the time • The DNS is the currently accepted way of getting from an IDENTIFIER to a LOCATOR • Or rather, put simply, we rely on the DNS to guide us through the network. • Assuming ...
... • Put this all together and your computers know roughly what they want. • They rely on the DNS to get them there most of the time • The DNS is the currently accepted way of getting from an IDENTIFIER to a LOCATOR • Or rather, put simply, we rely on the DNS to guide us through the network. • Assuming ...
What is an IP address?
... Use of different physical media Preservation of address space Security ...
... Use of different physical media Preservation of address space Security ...
Midterm Review - UTK-EECS
... application, definition of process, client, server and socket, how to address a process, client-server and P2P paradigms Transport layer services: what transport layer services are required by application layer, TCP vs. UDP services and their suitability for different applications Protocols: compara ...
... application, definition of process, client, server and socket, how to address a process, client-server and P2P paradigms Transport layer services: what transport layer services are required by application layer, TCP vs. UDP services and their suitability for different applications Protocols: compara ...