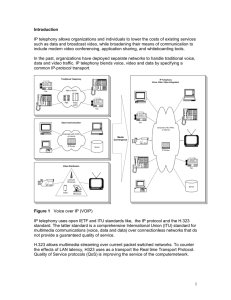
Introduction
... 1. John wishes to initiate an H.323 conference with Alice, another user on the LAN. Once Alice’s video conferencing application creates an Address object and puts it in listen mode. Alice’s IP address is added to the Internet Locator Service (ILS) ...
... 1. John wishes to initiate an H.323 conference with Alice, another user on the LAN. Once Alice’s video conferencing application creates an Address object and puts it in listen mode. Alice’s IP address is added to the Internet Locator Service (ILS) ...
Network Layer and Routing
... are divided into packets before they are sent. Each packet is then transmitted individually and can even follow different routes to its destination. Once all the packets forming a message arrive at the destination, they are recompiled into the original message. ...
... are divided into packets before they are sent. Each packet is then transmitted individually and can even follow different routes to its destination. Once all the packets forming a message arrive at the destination, they are recompiled into the original message. ...
A network operating system (NOS) is a computer
... primarily to support workstation, personal computer, and, in some instances, older terminal that are connected on a local area network (LAN). Artisoft's LANtastic, Banyan VINES, Novell's NetWare, and Microsoft's LAN Manager are examples of network operating systems. In addition, some multi-purpose o ...
... primarily to support workstation, personal computer, and, in some instances, older terminal that are connected on a local area network (LAN). Artisoft's LANtastic, Banyan VINES, Novell's NetWare, and Microsoft's LAN Manager are examples of network operating systems. In addition, some multi-purpose o ...
Networking Concepts
... Problem: Collisions of information are caused by two computers simultaneously attempting to send information in the network. Solution: Different networks have different protocol suites: • Apple Computer’s LocalTalk Protocol - Permission must be granted before information can be sent along the networ ...
... Problem: Collisions of information are caused by two computers simultaneously attempting to send information in the network. Solution: Different networks have different protocol suites: • Apple Computer’s LocalTalk Protocol - Permission must be granted before information can be sent along the networ ...
Networking Basics - Henry County Schools
... Phone or cable TV lines – connect LAN to an internet service provider (ISP) ...
... Phone or cable TV lines – connect LAN to an internet service provider (ISP) ...
Document
... Addressing in TCP/IP defined by Internet Protocol (IP) Each host assigned to a 32-bit number Called IP address or Internet address Unique to throughout Internet Each datagram contain IP address of source and destination ...
... Addressing in TCP/IP defined by Internet Protocol (IP) Each host assigned to a 32-bit number Called IP address or Internet address Unique to throughout Internet Each datagram contain IP address of source and destination ...
lecture 1 - CUNY Home
... What’s the Internet: an operational view Thus protocols define • format, order of messages sent and received among network entities, • actions taken on message transmission and receipt • address conflicts among network entities ...
... What’s the Internet: an operational view Thus protocols define • format, order of messages sent and received among network entities, • actions taken on message transmission and receipt • address conflicts among network entities ...
Network overview - Mr. Schneemann`s Web Page Edtechnology
... you study the online tutorial on networks, the PowerPoints and notes below, you should have a basic understanding of how networks work and how they can be used in the educational environment. Any time you connect at least two computers together, you have a computer network. Computer networks allow y ...
... you study the online tutorial on networks, the PowerPoints and notes below, you should have a basic understanding of how networks work and how they can be used in the educational environment. Any time you connect at least two computers together, you have a computer network. Computer networks allow y ...
Full Presentation
... user is the registrant for the ENUM domain name within the domain e164.arpa • Private Infrastructure ENUM – Creating a domain name from a telephone number (TN) and resolving it to a URI. It does not, however, use the domain e164.arpa – Private ENUM is used when there is a closed user group that want ...
... user is the registrant for the ENUM domain name within the domain e164.arpa • Private Infrastructure ENUM – Creating a domain name from a telephone number (TN) and resolving it to a URI. It does not, however, use the domain e164.arpa – Private ENUM is used when there is a closed user group that want ...
Laney Pastoria MIS 204 October 28, 2008 Chapter 9 Describe the
... A network standard defines guidelines that specify the way computers access a medium, the type(s) of medium, the speeds on different types of networks, and the type of physical cable or wireless technology used. Network communications standards include Ethernet, token ring, TCP/IP, 802.11 (Wi-Fi), B ...
... A network standard defines guidelines that specify the way computers access a medium, the type(s) of medium, the speeds on different types of networks, and the type of physical cable or wireless technology used. Network communications standards include Ethernet, token ring, TCP/IP, 802.11 (Wi-Fi), B ...
IT 141: Information Systems I
... interface card when it is made. Used for network security IP addresses: a series of numbers used to identify a network device. (e.g. 204.127.129.1) It is separated into 4 sections by periods. Each section is called an octet, because in binary it is represented by 8 bits. It can be assigned by ISPs ...
... interface card when it is made. Used for network security IP addresses: a series of numbers used to identify a network device. (e.g. 204.127.129.1) It is separated into 4 sections by periods. Each section is called an octet, because in binary it is represented by 8 bits. It can be assigned by ISPs ...
Basic Networking Hardware
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
8.9.2 Lab Configure DHCP in 7
... In this lab, you will configure an Ethernet NIC to use DHCP to obtain an IP address, test connectivity and establish a telnet connection between 2 computers. Note: The instructor will have a Telnet server configured on Host B. ...
... In this lab, you will configure an Ethernet NIC to use DHCP to obtain an IP address, test connectivity and establish a telnet connection between 2 computers. Note: The instructor will have a Telnet server configured on Host B. ...
Week 2: Routing vs. Switching
... Layering Questions • Do core devices care about layers >3 ? – Generally no, but... – What about performance? – Impact of speed mismatches on tcp vs. udp ...
... Layering Questions • Do core devices care about layers >3 ? – Generally no, but... – What about performance? – Impact of speed mismatches on tcp vs. udp ...
DRS5000 Configuration
... NOTE: Depending on the network card in your laptop it may be necessary to use a crossover Ethernet cable if connecting directly to the server. Some older computers do not automatically cross over the network data signals. If you do not have a crossover cable then you can use a hub or switch between ...
... NOTE: Depending on the network card in your laptop it may be necessary to use a crossover Ethernet cable if connecting directly to the server. Some older computers do not automatically cross over the network data signals. If you do not have a crossover cable then you can use a hub or switch between ...
Document
... by which data travels from its source to its destination. • Common network media are twisted-pair cable, coaxial cable, fiber-optic cable, and wireless links. • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of dat ...
... by which data travels from its source to its destination. • Common network media are twisted-pair cable, coaxial cable, fiber-optic cable, and wireless links. • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of dat ...
Job Class: 158814 Rev: 04/15 Exempt Page: 1
... Works with Systems Administrators to resolve system-networking issues. Works with Help Desk personnel to resolve end user networking issues. Manages, upgrades, and supports the campus network domain name services. Manages, upgrades and supports the campus network dynamic host name configuration serv ...
... Works with Systems Administrators to resolve system-networking issues. Works with Help Desk personnel to resolve end user networking issues. Manages, upgrades, and supports the campus network domain name services. Manages, upgrades and supports the campus network dynamic host name configuration serv ...
VLSM Calculation
... Since Singapore also requires 12 hosts, the next set of host addresses can be derived from the next available subnet (192.168.10.112/28). ...
... Since Singapore also requires 12 hosts, the next set of host addresses can be derived from the next available subnet (192.168.10.112/28). ...
Lab 1 – The Basics - Computer Science
... Turing has a command-line operating system called Linux, where you can directly type commands. traceroute is a command that reports the routing information for a specific URL. A URL is a Uniform Resource Locator. You can think of it as a human readable IP Address. URL are translated into numeric IP ...
... Turing has a command-line operating system called Linux, where you can directly type commands. traceroute is a command that reports the routing information for a specific URL. A URL is a Uniform Resource Locator. You can think of it as a human readable IP Address. URL are translated into numeric IP ...
Fundamentals of Computer Networks ECE 478/578
... fragmentation and re-assembly. Transport Layer: Flow (congestion) control, error control, transparent transport to upper layers Session Layer: Establishes connection among hosts, duplex, halfduplex, graceful connection termination, combination of streams Presentation Layer: Negotiation of format of ...
... fragmentation and re-assembly. Transport Layer: Flow (congestion) control, error control, transparent transport to upper layers Session Layer: Establishes connection among hosts, duplex, halfduplex, graceful connection termination, combination of streams Presentation Layer: Negotiation of format of ...
Wireless Networks
... Choice of scheme made by link manager Negotiates most appropriate scheme for application ...
... Choice of scheme made by link manager Negotiates most appropriate scheme for application ...
05. Example Networks..
... Both the Internet and ATM were designed for wide area networking The most popular LAN is Ethernet Up to 256 machines could be attached to the system via transceivers screwed onto the cable. A cable with multiple machines attached to it in parallel is called a multidrop cable A computer first listene ...
... Both the Internet and ATM were designed for wide area networking The most popular LAN is Ethernet Up to 256 machines could be attached to the system via transceivers screwed onto the cable. A cable with multiple machines attached to it in parallel is called a multidrop cable A computer first listene ...
Director III - Networks
... Significant Level Interpersonal Skills - Position engages in or requires some or all of the following: Develops, motivates, assesses, conducts performance reviews, and rewards other employees; Has significantly high interactions with student, program participants, and/or the public; Provides in dept ...
... Significant Level Interpersonal Skills - Position engages in or requires some or all of the following: Develops, motivates, assesses, conducts performance reviews, and rewards other employees; Has significantly high interactions with student, program participants, and/or the public; Provides in dept ...
Internet Layer Protocols
... • Understand network interface layer protocols • Describe different physical layer protocols • Discuss changes to IP introduced with IPv6 ...
... • Understand network interface layer protocols • Describe different physical layer protocols • Discuss changes to IP introduced with IPv6 ...























