Ping, traceroute, etc.
... • A computer that is connected to a TCP/IP network, including the Internet. • Each host has a unique IP address. – A computer may always have the same address or may have a different address each time it connects to the networks – Two computers on the same network or internet at the same time should ...
... • A computer that is connected to a TCP/IP network, including the Internet. • Each host has a unique IP address. – A computer may always have the same address or may have a different address each time it connects to the networks – Two computers on the same network or internet at the same time should ...
Windows Vista Security and Compliance
... 2.Scans the web site for characteristics common to phishing sites 3.Double checks site with online Microsoft service of reported phishing ...
... 2.Scans the web site for characteristics common to phishing sites 3.Double checks site with online Microsoft service of reported phishing ...
Q and A slides
... A: The question is, where is this extra memory required? The IP packet header didn’t change at all. Routing tables didn’t change either – because subnetting was available before CIDR. The only thing that changed is routing protocols, and they take more memory now, and the fact that ISPs can hand out ...
... A: The question is, where is this extra memory required? The IP packet header didn’t change at all. Routing tables didn’t change either – because subnetting was available before CIDR. The only thing that changed is routing protocols, and they take more memory now, and the fact that ISPs can hand out ...
Ipv6 addressing
... Describe the structure of an IPv4 address. Describe the purpose of the subnet mask. Compare the characteristics and uses of the unicast, broadcast and multicast IPv4 addresses. Compare the use of public and private addresses. Explain the need for IPv6 addressing. Describe the representat ...
... Describe the structure of an IPv4 address. Describe the purpose of the subnet mask. Compare the characteristics and uses of the unicast, broadcast and multicast IPv4 addresses. Compare the use of public and private addresses. Explain the need for IPv6 addressing. Describe the representat ...
MIDCOM-1
... Static Filtering Policy is not Enough Filtering policy in firewalls can be set up anywhere in the range between the ultimate (see previous slide) and completely open firewall (see what Microsoft suggests to enable NetMeeting in networks with firewalls) The problem: all these policies static; th ...
... Static Filtering Policy is not Enough Filtering policy in firewalls can be set up anywhere in the range between the ultimate (see previous slide) and completely open firewall (see what Microsoft suggests to enable NetMeeting in networks with firewalls) The problem: all these policies static; th ...
Part I: Introduction
... network protocols: machines rather than humans all communication activity in Internet governed by protocols protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt, other events ...
... network protocols: machines rather than humans all communication activity in Internet governed by protocols protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt, other events ...
Chervet Benjamin
... A new protocols has been created by combining different technologies from different background. ...
... A new protocols has been created by combining different technologies from different background. ...
IP address - DePaul University
... • Web browsers access HTML and other files from servers using HTTP • Web Servers store files and make them available to browsers ...
... • Web browsers access HTML and other files from servers using HTTP • Web Servers store files and make them available to browsers ...
Brad`s Lecture on networks
... PCs or just to individual PCs Better reliability- if one cable fails, rest of network not affected ...
... PCs or just to individual PCs Better reliability- if one cable fails, rest of network not affected ...
William Stallings Data and Computer Communications
... Level in architecture at which entity is named Unique address for each end system (computer) and router Network level address IP or internet address (TCP/IP) Network service access point or NSAP (OSI) ...
... Level in architecture at which entity is named Unique address for each end system (computer) and router Network level address IP or internet address (TCP/IP) Network service access point or NSAP (OSI) ...
Ch. 9 Networking Fundamentals
... • When a telephone call is placed in this type of network, only one physical path is used between the telephones for the duration of that call. • This pathway is maintained for the exclusive use of the call, until the connection is ended and the telephone is hung up. ...
... • When a telephone call is placed in this type of network, only one physical path is used between the telephones for the duration of that call. • This pathway is maintained for the exclusive use of the call, until the connection is ended and the telephone is hung up. ...
Streaming infrastructure
... rtsp - real time streaming protocol (RFC 2326) works over TCP or UDP (and could use RTP) uses URL rtsp://host.domain/dir/file as in http rtsp and request channel separate ...
... rtsp - real time streaming protocol (RFC 2326) works over TCP or UDP (and could use RTP) uses URL rtsp://host.domain/dir/file as in http rtsp and request channel separate ...
Slide 1
... • Core gateways make up the Internet backbone • Network nodes – Allowed one default gateway • Assigned manually, automatically (DHCP) ...
... • Core gateways make up the Internet backbone • Network nodes – Allowed one default gateway • Assigned manually, automatically (DHCP) ...
The network convergence: A Reality?
... UMA phone set up a WIFI connection with the Home Zone Box. It switches into UMA mode (icon appears on the phone). 1. Outside the Home Zone, the end user makes phone calls through the GSM ...
... UMA phone set up a WIFI connection with the Home Zone Box. It switches into UMA mode (icon appears on the phone). 1. Outside the Home Zone, the end user makes phone calls through the GSM ...
sheriff_1
... research computer at one university to "talk to" research computers at other universities. A side benefit of ARPANET design was that, because messages could be routed or rerouted in more than one direction, the network could continue to function even if parts of it were destroyed in the event of a m ...
... research computer at one university to "talk to" research computers at other universities. A side benefit of ARPANET design was that, because messages could be routed or rerouted in more than one direction, the network could continue to function even if parts of it were destroyed in the event of a m ...
Crowd Management System
... People count will be decided at server, by subtracting the 2 counts Suitable contraption will be designed to ensure no other light gets to sensor Advantage over single entry/exit Single entry/exit system may not be able to handle concurrent user crossings ...
... People count will be decided at server, by subtracting the 2 counts Suitable contraption will be designed to ensure no other light gets to sensor Advantage over single entry/exit Single entry/exit system may not be able to handle concurrent user crossings ...
Dealing with multiple clients
... number that acts like a name for a particular network adapter, so, for example, the network cards (or built-in network adapters) in two different computers will have different names, or MAC addresses, as would an Ethernet adapter and a wireless adapter in the same computer, and as would multiple net ...
... number that acts like a name for a particular network adapter, so, for example, the network cards (or built-in network adapters) in two different computers will have different names, or MAC addresses, as would an Ethernet adapter and a wireless adapter in the same computer, and as would multiple net ...
ppt
... • Connection setup (take on faith) -- TCP requires one roundtrip time to setup the connection state before it can chat... • How long does it take, using TCP, to fix a lost packet? • At minimum, one “round-trip time” (2x the latency of the network) • That could be 100+ milliseconds! ...
... • Connection setup (take on faith) -- TCP requires one roundtrip time to setup the connection state before it can chat... • How long does it take, using TCP, to fix a lost packet? • At minimum, one “round-trip time” (2x the latency of the network) • That could be 100+ milliseconds! ...
Question 1
... 2. If the number and load of computers in a shared Ethernet and a switched Ethernet are the same, then the average speed of the two networks will be the same. 3. Cut-through switches provide better filtering of erroneous packets than hubs. 4. A bridge can carry out traffic filtering based on Layer-2 ...
... 2. If the number and load of computers in a shared Ethernet and a switched Ethernet are the same, then the average speed of the two networks will be the same. 3. Cut-through switches provide better filtering of erroneous packets than hubs. 4. A bridge can carry out traffic filtering based on Layer-2 ...
Troubleshooting Slow Browsing
... It is recommended to use 127.0.0.1 as the Primary DNS Server if Cyberoam is used as a Direct Proxy Server (Cyberoam LAN IP configured as Proxy Server in browsers) OR if Cyberoam LAN IP is configured as DNS in all user systems. 127.0.0.1 is Cyberoam loop back local DNS Server which directly resolves ...
... It is recommended to use 127.0.0.1 as the Primary DNS Server if Cyberoam is used as a Direct Proxy Server (Cyberoam LAN IP configured as Proxy Server in browsers) OR if Cyberoam LAN IP is configured as DNS in all user systems. 127.0.0.1 is Cyberoam loop back local DNS Server which directly resolves ...
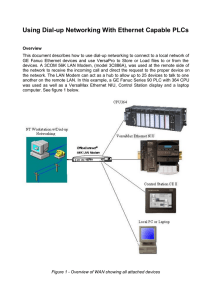
Using Dial-up Networking With Ethernet Capable PLCs
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...