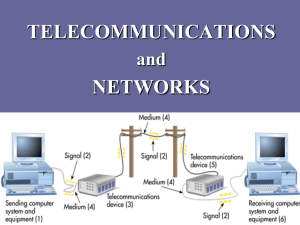
Reference Models - UT School of Information
... 1. Physical layer – not really part of this model, since TCP and IP deal with software; usually thought to refer to all hardware beneath the network layer. 2. Network or data link layer – defined by whatever the Internet Protocol will run over, e.g., a token-ring network. 3. Internet or network laye ...
... 1. Physical layer – not really part of this model, since TCP and IP deal with software; usually thought to refer to all hardware beneath the network layer. 2. Network or data link layer – defined by whatever the Internet Protocol will run over, e.g., a token-ring network. 3. Internet or network laye ...
Local Area Networks
... Because peripheral (external) devices like printers can be expensive, it is cost-effective to connect a device to a network so users can share it. ...
... Because peripheral (external) devices like printers can be expensive, it is cost-effective to connect a device to a network so users can share it. ...
N4Less17.pps - GEOCITIES.ws
... Because peripheral (external) devices like printers can be expensive, it is cost-effective to connect a device to a network so users can share it. ...
... Because peripheral (external) devices like printers can be expensive, it is cost-effective to connect a device to a network so users can share it. ...
IP addressing
... NATed client establishes connection to relay External client connects to relay relay bridges packets between connections ...
... NATed client establishes connection to relay External client connects to relay relay bridges packets between connections ...
network - CCIT131
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
Brian Kovar - Kansas State University
... How bits are physically transmitted using those media Access control rules Data transmission speeds ...
... How bits are physically transmitted using those media Access control rules Data transmission speeds ...
NETWORK FUNDAMENTALS
... Client/Server Protocol that provides file and print sharing between computers • Used directly over TCP or over NETBIOS ...
... Client/Server Protocol that provides file and print sharing between computers • Used directly over TCP or over NETBIOS ...
compnetwrk-print - SNGCE DIGITAL LIBRARY
... layer communication protocol for Metropolitan Area Networks (MANs), specified in the IEEE 802.6 standard, designed for use in MANs. DQDB is designed for data as well as voice and video transmission based on cell switching technology (similar to ATM). DQDB, which permits multiple systems to interconn ...
... layer communication protocol for Metropolitan Area Networks (MANs), specified in the IEEE 802.6 standard, designed for use in MANs. DQDB is designed for data as well as voice and video transmission based on cell switching technology (similar to ATM). DQDB, which permits multiple systems to interconn ...
2512 - Networking
... d. explain the importance of standards for communicating between devices e. explain how protocols are used to enable communication f. discuss the use of networks of computers at work and at home g. discuss the role of network hardware devices ...
... d. explain the importance of standards for communicating between devices e. explain how protocols are used to enable communication f. discuss the use of networks of computers at work and at home g. discuss the role of network hardware devices ...
Part I: Introduction - University of Pittsburgh
... CD – detect collision while sending and cancel it CA – avoid collision by getting permission first Ethernet and Wi-Fi? ...
... CD – detect collision while sending and cancel it CA – avoid collision by getting permission first Ethernet and Wi-Fi? ...
Introduction
... • Appreciate the complex trade-offs that are inherent in the design of networks • Provide a guided tour of network technologies from the lowest levels of data transmission up to network applications • Learn about the current and de facto networking standards, i.e. internet protocols ...
... • Appreciate the complex trade-offs that are inherent in the design of networks • Provide a guided tour of network technologies from the lowest levels of data transmission up to network applications • Learn about the current and de facto networking standards, i.e. internet protocols ...
Dark Matter and Dark Energy - Hitoshi Murayama Home Page
... • Fiber-optic backbone, machines attached through switches • Switches are smarter network device • Party where everybody talks over cell phone with head set • No “packet collisions,” a “sniffer” cannot steal passwords • Users allowed to install hubs, switches, routers for in-room network ...
... • Fiber-optic backbone, machines attached through switches • Switches are smarter network device • Party where everybody talks over cell phone with head set • No “packet collisions,” a “sniffer” cannot steal passwords • Users allowed to install hubs, switches, routers for in-room network ...
Exam Viewer - ENetwork Final Exam
... Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A? IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2 IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; ...
... Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A? IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2 IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; ...
A crash course in networking
... where N is the number of participants. This grows much more rapidly than either • the number of participants, N, • or the number of possible pair connections, N(N-1)/2 ...
... where N is the number of participants. This grows much more rapidly than either • the number of participants, N, • or the number of possible pair connections, N(N-1)/2 ...
Ten top problems network techs encounter
... client and server can cause connectivity problems for the client. The best way to do this is by using an SNMP tool that will monitor utilization over time on these links. Additionally, look for Ethernet Errors on all switches and routers that cause packet loss between client and server. ...
... client and server can cause connectivity problems for the client. The best way to do this is by using an SNMP tool that will monitor utilization over time on these links. Additionally, look for Ethernet Errors on all switches and routers that cause packet loss between client and server. ...
Acadia - IT, Sligo
... There is no redundancy of router link at POP. If the WAN link fails there will be no access to other resources in the district or access to the Internet The use of switches increase the network latency as well as initial cost of the network Expensive to implement Password security is based on user c ...
... There is no redundancy of router link at POP. If the WAN link fails there will be no access to other resources in the district or access to the Internet The use of switches increase the network latency as well as initial cost of the network Expensive to implement Password security is based on user c ...
Rapidly and Reliably Deploy an Enterprise Network
... Guaranteeing performance from individual Ethernet drops through the network requires performing several tests. First, test the wide area network (WAN) links to the data centers at full GE speeds using various frame sizes to ensure the links have no issues. Technicians should use different frame size ...
... Guaranteeing performance from individual Ethernet drops through the network requires performing several tests. First, test the wide area network (WAN) links to the data centers at full GE speeds using various frame sizes to ensure the links have no issues. Technicians should use different frame size ...
Chapter 9
... – NFS is a distributed file system protocol suite developed by Sun Microsystems that allows file access to a remote storage device ...
... – NFS is a distributed file system protocol suite developed by Sun Microsystems that allows file access to a remote storage device ...
research and evaluate ubnt wifi antenna for a 5 km
... Increase the wireless access point for high redundancy levels in the area Always have working spare parts ready and remember to follow-up on ...
... Increase the wireless access point for high redundancy levels in the area Always have working spare parts ready and remember to follow-up on ...
CHAP10 - Lyle School of Engineering
... • SECURITY: Exposure to Thieves & Vandals; Hackers Steal, Use Passwords; Not Yet Safe for Large Business Transactions • TECHNOLOGY: Lack of Uniform Standards; Transfer of Graphics, Video can be Costly • LEGAL ISSUES: Need More Laws Governing Electronic Commerce; Are email Contracts, Electronic Signa ...
... • SECURITY: Exposure to Thieves & Vandals; Hackers Steal, Use Passwords; Not Yet Safe for Large Business Transactions • TECHNOLOGY: Lack of Uniform Standards; Transfer of Graphics, Video can be Costly • LEGAL ISSUES: Need More Laws Governing Electronic Commerce; Are email Contracts, Electronic Signa ...
MEDICAL LABORATORY TECHNICIAN/CLINICAL LABORATORY
... The Computer Networking AAS program is designed to lead directly to employment in the field of information technology in roles such as network technician, network administrator, systems administrator and customer support. Students are trained to design, install, configure, troubleshoot, and maintain ...
... The Computer Networking AAS program is designed to lead directly to employment in the field of information technology in roles such as network technician, network administrator, systems administrator and customer support. Students are trained to design, install, configure, troubleshoot, and maintain ...
alisonc.net
... Developed C# and embedded C applications with communication over CAN/J1939/J1587. Deployed projects using dotNetInstaller and InstallShield. Prepared marketing materials and evaluated candidate products for distribution. Assisted inventory department with incoming and outgoing shipments. ...
... Developed C# and embedded C applications with communication over CAN/J1939/J1587. Deployed projects using dotNetInstaller and InstallShield. Prepared marketing materials and evaluated candidate products for distribution. Assisted inventory department with incoming and outgoing shipments. ...