TCP/IP Concepts (Part 1)
... Destination port (16 bits) – a number that identifies the Application layer program the message is destined to. Sequence number (32 bits) – Tracks packets received. Helps reassemble packets. Hackers may guest SN to hijack conversations. Has a dual role If the SYN flag is set, then this is the ini ...
... Destination port (16 bits) – a number that identifies the Application layer program the message is destined to. Sequence number (32 bits) – Tracks packets received. Helps reassemble packets. Hackers may guest SN to hijack conversations. Has a dual role If the SYN flag is set, then this is the ini ...
ns-3 solution
... Create the ns-3 Node objects that will represent the computers in the simulation. ...
... Create the ns-3 Node objects that will represent the computers in the simulation. ...
Slide 1
... Virtual Wireless Routers Microsoft Windows 7/2008 Virtual Wireless Routers o A function added to Microsoft Windows 7 is wireless Hosted Network o Virtualization of the physical wireless NIC into multiple virtual wireless NICs (Virtual WiFi) and a software-based wireless access point (SoftAP) that ...
... Virtual Wireless Routers Microsoft Windows 7/2008 Virtual Wireless Routers o A function added to Microsoft Windows 7 is wireless Hosted Network o Virtualization of the physical wireless NIC into multiple virtual wireless NICs (Virtual WiFi) and a software-based wireless access point (SoftAP) that ...
On IPv6 support in OpenFlow via Flexible Match Structures
... different protocols. NetPDL supports a myriad of protocols and cyclic encapsulations (e.g., an IPv4 packet tunnelled within another IPv6 packet). As many other technologies (e.g., XDR, ASN.1, IDL), NetPDL can be used to generate C code implementing packet processing [8], thus being able to run this ...
... different protocols. NetPDL supports a myriad of protocols and cyclic encapsulations (e.g., an IPv4 packet tunnelled within another IPv6 packet). As many other technologies (e.g., XDR, ASN.1, IDL), NetPDL can be used to generate C code implementing packet processing [8], thus being able to run this ...
Understand the Concepts of the Internet, Intranet, and
... VPNs operate as if the nodes were connected by private lines. An example would be teachers at home needing limited access to the school district’s intranet would be given VPN software for their personal laptop ...
... VPNs operate as if the nodes were connected by private lines. An example would be teachers at home needing limited access to the school district’s intranet would be given VPN software for their personal laptop ...
CS61C / CS150 in the News Review: I/O Working with real devices
... – Memory address to place data – # of bytes – I/O port #, direc]on of transfer – unit of transfer, amount to transfer per burst ...
... – Memory address to place data – # of bytes – I/O port #, direc]on of transfer – unit of transfer, amount to transfer per burst ...
Chapter 4. Network Layer
... Consider a datagram network using 32-bit host addresses. Suppose a router has four links, numbered 0 through 3, and packets are to be forwarded to the link interface as follows: ...
... Consider a datagram network using 32-bit host addresses. Suppose a router has four links, numbered 0 through 3, and packets are to be forwarded to the link interface as follows: ...
QH16-03010
... With the move to higher data rates available on The Internet there comes the ability to have simultaneous text and voice in both directions and it would also allow control functions that could provide handshaking between the terminals. Two possible scenarios for this come to mind: 1. If a user is mo ...
... With the move to higher data rates available on The Internet there comes the ability to have simultaneous text and voice in both directions and it would also allow control functions that could provide handshaking between the terminals. Two possible scenarios for this come to mind: 1. If a user is mo ...
Slide 1
... • Every host on a network is identified by a unique number, called IP address. • IP address is a 32 bit number and this number is written in dotted decimal notation, i.e. four decimal numbers one for each byte. E.g. 140.35.13.45 • Applications in the application layer are identified by unique number ...
... • Every host on a network is identified by a unique number, called IP address. • IP address is a 32 bit number and this number is written in dotted decimal notation, i.e. four decimal numbers one for each byte. E.g. 140.35.13.45 • Applications in the application layer are identified by unique number ...
Portfolio
... the Internet, but that does so on behalf of some set of endpoint nodes. The overlay is implemented by a software layer that itself uses standard Internet functionality (TCP/IP, UDP, etc). However, applications running “over” the overlay have access to special advantages that normal Internet communic ...
... the Internet, but that does so on behalf of some set of endpoint nodes. The overlay is implemented by a software layer that itself uses standard Internet functionality (TCP/IP, UDP, etc). However, applications running “over” the overlay have access to special advantages that normal Internet communic ...
Document
... • L2/L3 Technology to permit software-defined control of network forwarding and routing • What it’s not: ...
... • L2/L3 Technology to permit software-defined control of network forwarding and routing • What it’s not: ...
transparencies
... Mainly we work with the prospect of having a single user-support in EGEE (GGUS by FZK) and a single interface with GN2 Nevertheless we are aware that not all the NRENs will be handled by this single entry-point. ...
... Mainly we work with the prospect of having a single user-support in EGEE (GGUS by FZK) and a single interface with GN2 Nevertheless we are aware that not all the NRENs will be handled by this single entry-point. ...
Final_Presentation1-2
... Received frames are queued in a double buffer Frames must be de-queued in order to be removed from the buffer Incoming frames are dropped if buffer is full ...
... Received frames are queued in a double buffer Frames must be de-queued in order to be removed from the buffer Incoming frames are dropped if buffer is full ...
Transmission Control Protocol/Internet Protocol for the PC: an Ethernet implementation
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
... for the implementation of the communications package Transmission Control Protocol/Internet Protocol for the PC. A User's Manual is included as an appendix. The manual is specifically written for use in the Administrative Sciences Department Informations Systems laboratory at the Naval Postgraduate ...
Network_Layer
... The main design goals for Network Layer services: (see the book “Computer Networks by Tanenbaum” P345). ...
... The main design goals for Network Layer services: (see the book “Computer Networks by Tanenbaum” P345). ...
4th Edition: Chapter 1 - University of Wisconsin
... RIP: Link Failure and Recovery If no advertisement heard after 180 sec --> neighbor/link declared dead routes via neighbor invalidated new advertisements sent to neighbors neighbors in turn send out new advertisements (if ...
... RIP: Link Failure and Recovery If no advertisement heard after 180 sec --> neighbor/link declared dead routes via neighbor invalidated new advertisements sent to neighbors neighbors in turn send out new advertisements (if ...
Managed Bandwidth Vipersat Management System (VMS)
... clients. Thus, updates and changes can be made in a single location and distributed globally to all clients. Through its client/server architecture, VMS supports centralized management, control, and distribution of data, alarms, and events. It also supports multiple clients and network management us ...
... clients. Thus, updates and changes can be made in a single location and distributed globally to all clients. Through its client/server architecture, VMS supports centralized management, control, and distribution of data, alarms, and events. It also supports multiple clients and network management us ...
Steps for Configuring the IPv6 Test Lab - TechNet Gallery
... nondefault delivery services more efficient at intermediate routers. ...
... nondefault delivery services more efficient at intermediate routers. ...
Data Communications began in 1940 when Dr George Stibbitz sent
... The greatest concern facing specialists in data communications is the speed by which the data is transferred. As technology increases, researchers are discovering new techniques which can be used to transmit data faster than ever before. However, our expectations continue to rise, requiring an ever ...
... The greatest concern facing specialists in data communications is the speed by which the data is transferred. As technology increases, researchers are discovering new techniques which can be used to transmit data faster than ever before. However, our expectations continue to rise, requiring an ever ...
LAN Applications
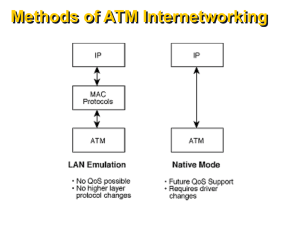
... All existing LAN applications can run on an Emulated LAN LAN Emulation allows ATM to be used as a backbone to interconnect “legacy” LANs and ATM-attached hosts To exploit the power of ATM, new applications need to use ATM-specific API’s, rather than LAN-Emulation ...
... All existing LAN applications can run on an Emulated LAN LAN Emulation allows ATM to be used as a backbone to interconnect “legacy” LANs and ATM-attached hosts To exploit the power of ATM, new applications need to use ATM-specific API’s, rather than LAN-Emulation ...
Standards for multimedia communications
... application and within the bandwidth limits provided by the network. • If the user data is shared between the various members of a conference, the application uses the services provided by a protocol known as a multipoint communications service (MCS). • A system -level standard embraces a number of ...
... application and within the bandwidth limits provided by the network. • If the user data is shared between the various members of a conference, the application uses the services provided by a protocol known as a multipoint communications service (MCS). • A system -level standard embraces a number of ...
$doc.title
... – Tradi5onal services provided by the connected network – E.g., address assignment, rou5ng, and DNS resolu5on ...
... – Tradi5onal services provided by the connected network – E.g., address assignment, rou5ng, and DNS resolu5on ...
Detecting service violation in Internet and Mobile ad hoc networks
... “unknown”. If all unknown links are treated as congested, 10 good link will be falsely labeled as congested. When the false positive is too high, the available paths that can be chosen by the routers are restricted, thus network performance is impacted. ...
... “unknown”. If all unknown links are treated as congested, 10 good link will be falsely labeled as congested. When the false positive is too high, the available paths that can be chosen by the routers are restricted, thus network performance is impacted. ...
Networks and Telecommunications
... Stress connectivity - the goal today is not a single, coherent network, but rather finding a means to interface many dissimilar networks Use standards - Most complications in networking are caused by incompatibilities which can be reduced by using standards. In fact, standards should be the foundati ...
... Stress connectivity - the goal today is not a single, coherent network, but rather finding a means to interface many dissimilar networks Use standards - Most complications in networking are caused by incompatibilities which can be reduced by using standards. In fact, standards should be the foundati ...