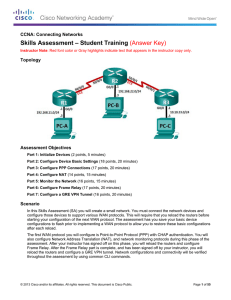
Skills Assessment – Student Training (Answer Key)
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
Chapter 14 PowerPoint Slides
... For server performance, remember that DHCP is diskintensive and purchase appropriate hardware Keep audit logging enabled for troubleshooting use Integrate DHCP with other services, such as Windows Internet Name Service (WINS) and DNS Use the appropriate number of DHCP servers for the number of DHCP- ...
... For server performance, remember that DHCP is diskintensive and purchase appropriate hardware Keep audit logging enabled for troubleshooting use Integrate DHCP with other services, such as Windows Internet Name Service (WINS) and DNS Use the appropriate number of DHCP servers for the number of DHCP- ...
Slides
... multicast tree for multicast routing table to forward the multicast datagrams. In IPv6/IPv4 multicast, routers use multicast group management protocol, such as IGMPv3 for IPv4 and MLDv2 for IPv6, to manage multicast members, and set up and maintain member relationships between hosts and the multicas ...
... multicast tree for multicast routing table to forward the multicast datagrams. In IPv6/IPv4 multicast, routers use multicast group management protocol, such as IGMPv3 for IPv4 and MLDv2 for IPv6, to manage multicast members, and set up and maintain member relationships between hosts and the multicas ...
OSPF
... - Cisco menghitung Cost dgn rumus = 108 / bandwidth interface. - Nilai cost dapat dimanipulasi dalam range 1 s/d 65.535, perintahnya: ip ospf cost ...
... - Cisco menghitung Cost dgn rumus = 108 / bandwidth interface. - Nilai cost dapat dimanipulasi dalam range 1 s/d 65.535, perintahnya: ip ospf cost ...
ipv6 technology and dns setup
... running out of IPv4 addresses; support streaming sources (flows), such as audio, video etc.; improve router efficiency and so on. IPv4 has not been substantially changed since RFC 791 was published in 1981. IPv4 is robust, easily implemented and interoperable, and has stood the test of scaling an In ...
... running out of IPv4 addresses; support streaming sources (flows), such as audio, video etc.; improve router efficiency and so on. IPv4 has not been substantially changed since RFC 791 was published in 1981. IPv4 is robust, easily implemented and interoperable, and has stood the test of scaling an In ...
Comparative firewall study - Torsten Hoefler - Qucosa
... proxy is not transparent for the user. The sender must adjust explicitly the proxy. Direct access of the client to the server has to be suppressed by blocking ports in the packet filter or disabling routing completely. In the second case the proxy is also called dual-homed gateway. You can achieve a ...
... proxy is not transparent for the user. The sender must adjust explicitly the proxy. Direct access of the client to the server has to be suppressed by blocking ports in the packet filter or disabling routing completely. In the second case the proxy is also called dual-homed gateway. You can achieve a ...
Dimension ES-4024 Ethernet Switch: User`s Guide
... commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmfu ...
... commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmfu ...
CGL Requirements Definition V5.0
... become accepted parts of the Linux mainstream. While the usage models and goals described above evolve, this is accompanied by a simultaneous shift away from proprietary platform architectures to commercial off-the-shelf (COTS) platforms and open software environments. This continues to pick up pace ...
... become accepted parts of the Linux mainstream. While the usage models and goals described above evolve, this is accompanied by a simultaneous shift away from proprietary platform architectures to commercial off-the-shelf (COTS) platforms and open software environments. This continues to pick up pace ...
Cloud and Network Services
... QoS policies can easily be applied to any WAN or VPN tunnel interface using Cisco SDM. The QoS policy wizard automates the Cisco architecture guidelines for QoS policies to effectively prioritize the traffic between real-time applications (voice or video), business-critical applications (Structured ...
... QoS policies can easily be applied to any WAN or VPN tunnel interface using Cisco SDM. The QoS policy wizard automates the Cisco architecture guidelines for QoS policies to effectively prioritize the traffic between real-time applications (voice or video), business-critical applications (Structured ...
HP Jetdirect Print Servers (300X/510X) Administrators Guide ENWW
... Internet Printer Connection Software HP Jetdirect print servers (firmware version x.07.16 or later) support the Internet Printing Protocol (IPP). Using the appropriate software on your system, you can create an IPP print path from your system to any HP Jetdirect-connected printer over the Internet. ...
... Internet Printer Connection Software HP Jetdirect print servers (firmware version x.07.16 or later) support the Internet Printing Protocol (IPP). Using the appropriate software on your system, you can create an IPP print path from your system to any HP Jetdirect-connected printer over the Internet. ...
Guide DynaStar 1500 (DS1500-XFR) X.25 Frame Router
... As to equipment proposed and furnished by Dymec, Inc., Dymec, Inc. shall defend any suit or proceeding brought against purchaser so far as based on a claim that said equipment constitutes an infringement of any patent of the United States, if notified promptly in writing and given authority, informa ...
... As to equipment proposed and furnished by Dymec, Inc., Dymec, Inc. shall defend any suit or proceeding brought against purchaser so far as based on a claim that said equipment constitutes an infringement of any patent of the United States, if notified promptly in writing and given authority, informa ...
Ip Addressing and Subnetting Workbook
... (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each independent of the other. This can only be accomplished by using a custom subnet mask. A cus ...
... (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each independent of the other. This can only be accomplished by using a custom subnet mask. A cus ...
Ip Addressing and Subnetting Workbook
... (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each independent of the other. This can only be accomplished by using a custom subnet mask. A cus ...
... (192.100.10.16, 192.100.10.32, 192.100.10.48, 192.100.10.64, 192.100.10.80) the outside world still sees the network as 192.100.10.0, but the internal computers and routers see five smaller subnetworks. Each independent of the other. This can only be accomplished by using a custom subnet mask. A cus ...
BGP-Part 1
... A better design would be to use both paths, with each one providing backup for the other in the event of link or router failure. One example would be to run a dynamic routing protocol like OSPF within your network, with static default routes advertised at both campus entrance routers into your netwo ...
... A better design would be to use both paths, with each one providing backup for the other in the event of link or router failure. One example would be to run a dynamic routing protocol like OSPF within your network, with static default routes advertised at both campus entrance routers into your netwo ...
ROUTE Chapter 8 - Strona startowa
... The first 64 bits are the network portion of the address and are statically specified or learned via SLAAC. The interface ID (second 64-bits) is the host portion of the address and is automatically generated by the router or host device. The interface ID on an Ethernet link is based on the 48- ...
... The first 64 bits are the network portion of the address and are statically specified or learned via SLAAC. The interface ID (second 64-bits) is the host portion of the address and is automatically generated by the router or host device. The interface ID on an Ethernet link is based on the 48- ...
ATIS IPTV Standards Development via ATIS IPTV
... IPTV Identity Management Packet Technologies and Systems Committee (PTSC) ...
... IPTV Identity Management Packet Technologies and Systems Committee (PTSC) ...
WiMAX Networking implications for IETF 16ng
... infrastructure to one or more Network Service Providers. • Network Service Provider (NSP) – A business entity that provides IP connectivity and network services to subscribers compliant with the Service Level Agreement it establishes with subscribers. To provide these services, an NSP establishes co ...
... infrastructure to one or more Network Service Providers. • Network Service Provider (NSP) – A business entity that provides IP connectivity and network services to subscribers compliant with the Service Level Agreement it establishes with subscribers. To provide these services, an NSP establishes co ...
broadband business - Andatelecomindia.com
... Routing is based on static routing entries in the routing table. Alternate routing is possible through the use of different preferences for different routes to the same destination. Policy based static routing: Normal routing is based on the destination IP address. Policy based routing offers the po ...
... Routing is based on static routing entries in the routing table. Alternate routing is possible through the use of different preferences for different routes to the same destination. Policy based static routing: Normal routing is based on the destination IP address. Policy based routing offers the po ...
Chapter 12 PowerPoint
... computers in a workgroup or project Ensures that mutual authentication takes place between the computers so that only authenticated computers can participate in communications Allows mutual authentication capabilities to protocols that do not support mutual authentication ...
... computers in a workgroup or project Ensures that mutual authentication takes place between the computers so that only authenticated computers can participate in communications Allows mutual authentication capabilities to protocols that do not support mutual authentication ...
ATM LAN Emulation
... or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without prior written permission of Professor Nen-Fu Huang (E-mail: [email protected]). ...
... or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without prior written permission of Professor Nen-Fu Huang (E-mail: [email protected]). ...
Internet usage
... The FTP protocol is used for reliable data transfer between a client and a server. This protocol is used to transport data in data connection of FTP communication. Secure version of the FTP protocol. GMAIL Drive is a Shell Namespace Extension that creates a virtual file system around your Google Mai ...
... The FTP protocol is used for reliable data transfer between a client and a server. This protocol is used to transport data in data connection of FTP communication. Secure version of the FTP protocol. GMAIL Drive is a Shell Namespace Extension that creates a virtual file system around your Google Mai ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.