Palo Alto Networks Administrator’s Guide Release 5.0
... VLAN Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Virtual Routers and Routing Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Routing Information Protocol. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... VLAN Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Virtual Routers and Routing Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Routing Information Protocol. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
TS 102 470-1
... Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable D ...
... Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable D ...
6rd - Enabling IPv6 Customers on an IPv4
... Native dual-stack IPv4/IPv6 in the home or office Simple, stateless, automatic IPv6-in-IPv4 encap and decap functions IPv6 traffic automatically follows IPv4 Routing between CPE and BR BRs placed at IPv6 edge, addressed via anycast for load-balancing and resiliency Standardized in RFC ...
... Native dual-stack IPv4/IPv6 in the home or office Simple, stateless, automatic IPv6-in-IPv4 encap and decap functions IPv6 traffic automatically follows IPv4 Routing between CPE and BR BRs placed at IPv6 edge, addressed via anycast for load-balancing and resiliency Standardized in RFC ...
User Guide
... Copyright © 2002 Nomadix, Inc. All Rights Reserved. This product also includes software developed by: The University of California, Berkeley and its contributors; Carnegie Mellon University, Copyright © 1998 by Carnegie Mellon University All Rights Reserved; Go Ahead Software, Inc., Copyright © 1999 ...
... Copyright © 2002 Nomadix, Inc. All Rights Reserved. This product also includes software developed by: The University of California, Berkeley and its contributors; Carnegie Mellon University, Copyright © 1998 by Carnegie Mellon University All Rights Reserved; Go Ahead Software, Inc., Copyright © 1999 ...
IPv6 Technical Challenges
... • In most countries, well under 10% of all networks are announcing IPv6 (and that includes Canada, my friends). • The web sites that people care about the most are, for the most part, still IPv4 only. • Literally 99% of all domain names are still IPv4 only, and the Internet’s authoritative name serv ...
... • In most countries, well under 10% of all networks are announcing IPv6 (and that includes Canada, my friends). • The web sites that people care about the most are, for the most part, still IPv4 only. • Literally 99% of all domain names are still IPv4 only, and the Internet’s authoritative name serv ...
JNCIA Study Guide - Open Shortest Path First (OSPF)
... new OSPF feature, we have to assign it a bit in the Options field. We already have bits assigned for multicast LSA, opaque LSA, TOS routing, and so forth. The problem is simple; we’ve used up all the bits in the Options field. As a result, the network community is having a difficult time scaling the ...
... new OSPF feature, we have to assign it a bit in the Options field. We already have bits assigned for multicast LSA, opaque LSA, TOS routing, and so forth. The problem is simple; we’ve used up all the bits in the Options field. As a result, the network community is having a difficult time scaling the ...
Cisco Prime Network Supported Technologies and Topologies, 4.2.2
... each technology. Note the fact that if a specific technology is listed in Table 11-1, it does not imply that every aspect of the relevant standard is represented and supported. In addition, the specific level of support provided for a particular technology on individual network elements can vary. Fo ...
... each technology. Note the fact that if a specific technology is listed in Table 11-1, it does not imply that every aspect of the relevant standard is represented and supported. In addition, the specific level of support provided for a particular technology on individual network elements can vary. Fo ...
PDF - Complete Book (1.66 MB)
... The Cisco BTS 10200 Softswitch is a software-based, class-independent network switch. It provides call-control intelligence for establishing, maintaining, routing, and terminating voice calls on media gateways (MGWs) in the packet network, while seamlessly operating with legacy circuit-switched netw ...
... The Cisco BTS 10200 Softswitch is a software-based, class-independent network switch. It provides call-control intelligence for establishing, maintaining, routing, and terminating voice calls on media gateways (MGWs) in the packet network, while seamlessly operating with legacy circuit-switched netw ...
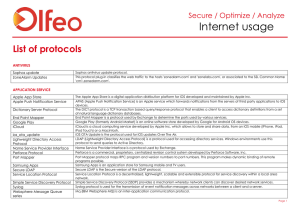
Protocols List
... The RQuota protocol enables the implementation of quotas on remote machines. It is used in conjunction with the NFS protocol. The RStat protocol is used in the Sun NFS family to exchange statistics on network activity. The RUser's protocol provides a service that lists users currently logged on a re ...
... The RQuota protocol enables the implementation of quotas on remote machines. It is used in conjunction with the NFS protocol. The RStat protocol is used in the Sun NFS family to exchange statistics on network activity. The RUser's protocol provides a service that lists users currently logged on a re ...
... artifacts in a timed, scored environment. Each thread is built around a specific security skills set, such as web, SQL, and password security. Recovering artifacts gets harder as the player progresses along the thread, providing an active, adaptable challenge. This type of game is currently availabl ...
Analysis of Reliable Multicast Protocols
... The un-numbered line after the command shows that the destination is 153.18.8.1. The TTL value is 30 hops. The packet contains 38 bytes: 20 bytes of IP header, 8 bytes of UDP header, and 10 bytes of application data. The application data is used by traceroute to keep track of the packets. The first ...
... The un-numbered line after the command shows that the destination is 153.18.8.1. The TTL value is 30 hops. The packet contains 38 bytes: 20 bytes of IP header, 8 bytes of UDP header, and 10 bytes of application data. The application data is used by traceroute to keep track of the packets. The first ...
ecs251 Spring 2007 - UC Davis Computer Science
... upload speed, resulting in a high download failure rate. If only a few individuals contribute to the public good, these few peers effectively act as centralized servers. ...
... upload speed, resulting in a high download failure rate. If only a few individuals contribute to the public good, these few peers effectively act as centralized servers. ...
Command Line Interface Guide
... This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes t ...
... This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes t ...
iSCSI SAN Topologies Version 3.2 Jonghoon (Jason) Jeong
... Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC2, EMC, and the EMC logo are registered trademarks or trademarks of EMC Corporation in the United State and other countries. All other trademarks used herein are the property ...
... Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC2, EMC, and the EMC logo are registered trademarks or trademarks of EMC Corporation in the United State and other countries. All other trademarks used herein are the property ...
PDF - Complete Book (3.07 MB)
... Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of act ...
... Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of act ...
SpeedStream™ Router Family
... Controlling Remote Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97 Disabling Remote Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97 Re-enabling Remote Management . ...
... Controlling Remote Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97 Disabling Remote Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97 Re-enabling Remote Management . ...
SnapGear Administration Guide Firmware Version 3.1.5
... measures shall not be less than those measures employed by you in protecting your own proprietary information. You may disclose the Software Product to your employees as necessary for the use permitted under this Agreement. You shall not remove any trademark, trade name, copyright notice or other pr ...
... measures shall not be less than those measures employed by you in protecting your own proprietary information. You may disclose the Software Product to your employees as necessary for the use permitted under this Agreement. You shall not remove any trademark, trade name, copyright notice or other pr ...
IBM Networking OS Application Guide for the IBM Flex System
... Configuring SSH/SCP Features on the Switch . . . . Configuring the SCP Administrator Password. . . . . Using SSH and SCP Client Commands . . . . . . . SSH and SCP Encryption of Management Messages . Generating RSA Host and Server Keys for SSH Access SSH/SCP Integration with RADIUS Authentication . . ...
... Configuring SSH/SCP Features on the Switch . . . . Configuring the SCP Administrator Password. . . . . Using SSH and SCP Client Commands . . . . . . . SSH and SCP Encryption of Management Messages . Generating RSA Host and Server Keys for SSH Access SSH/SCP Integration with RADIUS Authentication . . ...
INR11%20-%20OSPF
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
... Manipulating the election process If you want to influence the election of DR and BDR with further configurations then do one of the following: Boot up the DR first, followed by the BDR, and then boot all other routers, OR Shut down the interface on all routers, followed by a no shutdown on th ...
LAN Connection and IP Networks
... otherwise authorize in writing. Memotec Inc. reserves the right to make changes without notice in product or component design as warranted by evolution in user needs or progress in engineering or manufacturing technology. Changes which affect the operation of the unit will be documented in the next ...
... otherwise authorize in writing. Memotec Inc. reserves the right to make changes without notice in product or component design as warranted by evolution in user needs or progress in engineering or manufacturing technology. Changes which affect the operation of the unit will be documented in the next ...
NETGEAR Wireless-N Router WNR2000 User Manual , Inc.
... Radio Frequency Notice: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generat ...
... Radio Frequency Notice: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generat ...
ST Micro Connect 2 host-target interface
... When connected to an Ethernet, ST Micro Connect 2 is a network device that provides a fast, flexible interface between the host system and a target development system. Using the ST Micro Connect 2 in this mode enables the target system to be remote and to be easily shared among users. This datasheet ...
... When connected to an Ethernet, ST Micro Connect 2 is a network device that provides a fast, flexible interface between the host system and a target development system. Using the ST Micro Connect 2 in this mode enables the target system to be remote and to be easily shared among users. This datasheet ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.