Document
... • May operate in aggregate fashion • In-network processing • Sensor nodes are limited in power, computational capacities, and memory • May not have global ID like IP address ...
... • May operate in aggregate fashion • In-network processing • Sensor nodes are limited in power, computational capacities, and memory • May not have global ID like IP address ...
Telescience Update
... Osaka University and NTT have developed an uncompressed HDTV streaming system for a tiled display wall. The system can receive HDTV streams from the NTT i-Visto system. NTT has also developed a protocol converter, which enables interoperation between i-Visto and iHD1500 developed by the University o ...
... Osaka University and NTT have developed an uncompressed HDTV streaming system for a tiled display wall. The system can receive HDTV streams from the NTT i-Visto system. NTT has also developed a protocol converter, which enables interoperation between i-Visto and iHD1500 developed by the University o ...
00362r0P802-15_LRSG-Precision-Agriculture-Smart-Farm
... low date rate • Sensor information data < 50 bps/zone ...
... low date rate • Sensor information data < 50 bps/zone ...
Solution
... 2. Why is an ARP query sent with a broadcast frame? Why is an ARP response sent within a frame with a specific destination MAC address? (1 point) An ARP query is sent in a broadcast frame because the querying host does not which adapter address corresponds to the IP address in question. For the resp ...
... 2. Why is an ARP query sent with a broadcast frame? Why is an ARP response sent within a frame with a specific destination MAC address? (1 point) An ARP query is sent in a broadcast frame because the querying host does not which adapter address corresponds to the IP address in question. For the resp ...
r03-arpa - Computer Engineering
... • Different link-layers have different MTUs • Split IP packet into multiple fragments • IP header on each fragment • Various fields in header to help process • Intermediate router may fragment as needed ...
... • Different link-layers have different MTUs • Split IP packet into multiple fragments • IP header on each fragment • Various fields in header to help process • Intermediate router may fragment as needed ...
The Open Network Laboratory
... that make up their topology for the duration of their experiment. Real-time charts are available to monitor network statistics such as bandwidth, packet rates, and queue lengths. The ONL software infrastructure automatically manages all of the details of setting up the experiment, including mapping ...
... that make up their topology for the duration of their experiment. Real-time charts are available to monitor network statistics such as bandwidth, packet rates, and queue lengths. The ONL software infrastructure automatically manages all of the details of setting up the experiment, including mapping ...
WSON Impairment
... network life, e.g., the optical interfaces might be upgraded to higher bit-rates. Such changes could result in paths being unsuitable for the optical signal. Moreover, the optical physical interfaces are typically provisioned at various stages of the network's life span as needed by traffic demands. ...
... network life, e.g., the optical interfaces might be upgraded to higher bit-rates. Such changes could result in paths being unsuitable for the optical signal. Moreover, the optical physical interfaces are typically provisioned at various stages of the network's life span as needed by traffic demands. ...
i2 dcn dragon
... Some Experiments didn’t have right scaling/deployment characteristics • Implemented separate circuit based network for reserved capacity • Required separate interface(s) for downstream networks • Didn’t integrate into financial or operational model, not financially viable given current funding mode ...
... Some Experiments didn’t have right scaling/deployment characteristics • Implemented separate circuit based network for reserved capacity • Required separate interface(s) for downstream networks • Didn’t integrate into financial or operational model, not financially viable given current funding mode ...
3B-3 - McGraw Hill Higher Education
... • Server based network – Node is any network device – Servers control what the node accesses – Users gain access by logging in – Server is the most important computer – File server stores files • Forwards files to requesting nodes ...
... • Server based network – Node is any network device – Servers control what the node accesses – Users gain access by logging in – Server is the most important computer – File server stores files • Forwards files to requesting nodes ...
COS 217, Spring 2005 - Cs.princeton.edu
... – Security, economic incentives, management, mobility, layer-2 technologies (e.g., wireless, sensors, optics) – NSF FIND initiative for clean-slate network research – The importance of building and evaluating prototypes ...
... – Security, economic incentives, management, mobility, layer-2 technologies (e.g., wireless, sensors, optics) – NSF FIND initiative for clean-slate network research – The importance of building and evaluating prototypes ...
hi! i`m firoz cherapulikkal
... Profound leadership in planning and implementation of projects for computer operations and enterprise systems administration Adept in improving network functioning and ensuring delivery of high standard of customer service Skilled in establishing environment by managing system configuration, directi ...
... Profound leadership in planning and implementation of projects for computer operations and enterprise systems administration Adept in improving network functioning and ensuring delivery of high standard of customer service Skilled in establishing environment by managing system configuration, directi ...
University of Ottawa - School of Electrical Engineering and
... This communication pattern requires us to send 3 (64 – 8) or 168 total packets— that is, 56 packets in each of the three communication phases: northward, eastward, westwards. The number of hops suffered by packets depends on the topology. Here are the various cases: _ Bus—The mapping of the 8 ...
... This communication pattern requires us to send 3 (64 – 8) or 168 total packets— that is, 56 packets in each of the three communication phases: northward, eastward, westwards. The number of hops suffered by packets depends on the topology. Here are the various cases: _ Bus—The mapping of the 8 ...
1.7M PowerPoint Presentation
... Each node maintains a location table including location related information for itself and a list of its neighbouring nodes. Position information, including speed and direction, exchanged in ...
... Each node maintains a location table including location related information for itself and a list of its neighbouring nodes. Position information, including speed and direction, exchanged in ...
Should SIP be modified for per call billing?
... SIP is not just for voice, we don’t need to mimic the POTS behavior. Billing network resource is better handled by network protocols, RSVP. ...
... SIP is not just for voice, we don’t need to mimic the POTS behavior. Billing network resource is better handled by network protocols, RSVP. ...
Home Network Basics
... – Media Access Control address – Unique address for each item on a network • Can be found in System Information under Network Adapter ...
... – Media Access Control address – Unique address for each item on a network • Can be found in System Information under Network Adapter ...
426Introduction
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
Proposal Student Competition Enhancement
... Linux CIFS • The Linux samba service can offer native windows CIFS network file-system to both Linux and Windows nodes. • Requires package samba.x86_64 • /etc/samba/smb.conf is the main configuration file • /etc/init.d/smb is the samba server service ...
... Linux CIFS • The Linux samba service can offer native windows CIFS network file-system to both Linux and Windows nodes. • Requires package samba.x86_64 • /etc/samba/smb.conf is the main configuration file • /etc/init.d/smb is the samba server service ...
IT Support Engineer
... Provision of a network which gives AHDB the ability to collect, process and disseminate data on agricultural markets in order to promote efficient production and marketing of each sector of AHDB’s activities. To ensure a tested Disaster Recovery process is in place. To ensure that system secur ...
... Provision of a network which gives AHDB the ability to collect, process and disseminate data on agricultural markets in order to promote efficient production and marketing of each sector of AHDB’s activities. To ensure a tested Disaster Recovery process is in place. To ensure that system secur ...
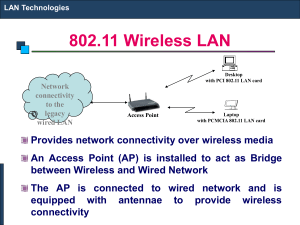
802.11 Wireless LAN
... Bridges are used to logically separate network segments within the same network. They operate at the OSI data link layer (Layer 2) and are independent of higherlayer protocols. The function of the bridge is to make intelligent decisions about whether or not to pass signals on to the next segment of ...
... Bridges are used to logically separate network segments within the same network. They operate at the OSI data link layer (Layer 2) and are independent of higherlayer protocols. The function of the bridge is to make intelligent decisions about whether or not to pass signals on to the next segment of ...
Brain Damage: Algorithms for Network Pruning
... • Hassibi, Babak, Stork, David. “Optimal Brain Surgeon and General Network Pruning”. Ricoh ...
... • Hassibi, Babak, Stork, David. “Optimal Brain Surgeon and General Network Pruning”. Ricoh ...
Peer-to-Peer Network
... wants to transmit data, it adds the data as well as the destination address to the frame. ...
... wants to transmit data, it adds the data as well as the destination address to the frame. ...
Adam Arvay IGVA 1 Opening the black box of connectionist nets
... useful starting point. Neural networking technology had advanced the point that off-the-shelf software had been developed which could be used to build and train neural networks. This allowed groups to focus more on the functionality of the network rather than understanding the operation of the netwo ...
... useful starting point. Neural networking technology had advanced the point that off-the-shelf software had been developed which could be used to build and train neural networks. This allowed groups to focus more on the functionality of the network rather than understanding the operation of the netwo ...
Chapter 1/Tutorial
... Layering ( the TCP/IP Model) : Data Link Layer : is responsible for delivery of information across a single link that transfers data between adjacent network nodes. PPP : commonly used in establishing a direct connection between two networking nodes . It can provide connection authentication , ...
... Layering ( the TCP/IP Model) : Data Link Layer : is responsible for delivery of information across a single link that transfers data between adjacent network nodes. PPP : commonly used in establishing a direct connection between two networking nodes . It can provide connection authentication , ...
INTERNET CONNECTIONS How does data get from point A to point
... The telephone switching system creates an electrical circuit between two telephones The switching system maintains this circuit until you hang up. ...
... The telephone switching system creates an electrical circuit between two telephones The switching system maintains this circuit until you hang up. ...
Securing VoIP and PSTN from Integrated Signaling
... has opened up market SS7 design and development carried out in different environment from the presently existing one. Convergence of voice and data networks ...
... has opened up market SS7 design and development carried out in different environment from the presently existing one. Convergence of voice and data networks ...