Networking and Communication: Bus, switch, and network structures
... Switches are a fundamental part of most networks. They make it possible for several users to send information over a network at the same time without slowing each other down. Switches allow different nodes (a network connection point, typically a computer) of a network to communicate directly with o ...
... Switches are a fundamental part of most networks. They make it possible for several users to send information over a network at the same time without slowing each other down. Switches allow different nodes (a network connection point, typically a computer) of a network to communicate directly with o ...
Embedded Networked Sensing Systems: motivations and challenges
... Core requirement is multi-hop time synchronization to eliminate dependence on GPS access at every node ...
... Core requirement is multi-hop time synchronization to eliminate dependence on GPS access at every node ...
Applying COSITU in the Region The Swazi MTN Experience
... ØHowever, for purposes of our business we found the model to be useful in giving us indicators on where focus must be directed for either cost reduction or tariff adjustments. ØThe only part that was not done was benchmarking with other countries. ...
... ØHowever, for purposes of our business we found the model to be useful in giving us indicators on where focus must be directed for either cost reduction or tariff adjustments. ØThe only part that was not done was benchmarking with other countries. ...
Peakflow SP
... Traffic of specific types exceeding what should be normal for a network. Misuse anomalies cover the following types of traffic: ...
... Traffic of specific types exceeding what should be normal for a network. Misuse anomalies cover the following types of traffic: ...
Understanding Networking
... • WANs require the crossing of public right of ways (under control and regulations of the interstate commerce and institute of telephone and data communications established by the gov’t and international treaties). • WANs around the world relies on the infrastructure established by the telephone com ...
... • WANs require the crossing of public right of ways (under control and regulations of the interstate commerce and institute of telephone and data communications established by the gov’t and international treaties). • WANs around the world relies on the infrastructure established by the telephone com ...
09-Planning
... ‣ To know what kind of information is valuable to collect when performing a site survey and how to do it ‣ To learn about some free tools that can simplify link planning and “what if” simulations ...
... ‣ To know what kind of information is valuable to collect when performing a site survey and how to do it ‣ To learn about some free tools that can simplify link planning and “what if” simulations ...
Screened-host firewall
... between the internet and corporate network Packet headers have information in them such as the IP of sender and receiver and port numbers. Based on this, the router knows what kind of internet service e.g. Web based or ftp is being used to send the data. And using this information can prevent ...
... between the internet and corporate network Packet headers have information in them such as the IP of sender and receiver and port numbers. Based on this, the router knows what kind of internet service e.g. Web based or ftp is being used to send the data. And using this information can prevent ...
Job Title: Human Resource Secretary Wage/Hour
... stakeholder satisfaction of services provided. Responsible for ensuring that an excellent level of customer service is being provided by the department and serves as an escalation point for principals or other district leadership that have unresolved problems. 10. Continually seek and implement new ...
... stakeholder satisfaction of services provided. Responsible for ensuring that an excellent level of customer service is being provided by the department and serves as an escalation point for principals or other district leadership that have unresolved problems. 10. Continually seek and implement new ...
No Slide Title
... • Can limit or secure network traffic based on identifiable attributes within each packet. • Switch packets to the appropriate interface based on the destination IP address. • Can perform bridging and routing. ...
... • Can limit or secure network traffic based on identifiable attributes within each packet. • Switch packets to the appropriate interface based on the destination IP address. • Can perform bridging and routing. ...
chapter 3
... Prolexic: ‘itsoknoproblembro’ DDoS attacks are highly sophisticated. Experts from Prolexic Technologies claim a new type of distributed denial-of-service (DDoS) attack has not only increased in size, but also reached a new level of sophistication. DDoS attacks have recently caused a lot of problems ...
... Prolexic: ‘itsoknoproblembro’ DDoS attacks are highly sophisticated. Experts from Prolexic Technologies claim a new type of distributed denial-of-service (DDoS) attack has not only increased in size, but also reached a new level of sophistication. DDoS attacks have recently caused a lot of problems ...
New Bulgarian University
... computer network, in which all nodes can reach each other by broadcast at the data link layer. A broadcast domain can be within the same LAN or it can be routed towards other LAN segments. ...
... computer network, in which all nodes can reach each other by broadcast at the data link layer. A broadcast domain can be within the same LAN or it can be routed towards other LAN segments. ...
Heather Ames Chuan-Heng Chsiao Chaitanya Sai Gaddam 13
... Host-based IDS look at system data and reside on each computer in a network. Networkbased systems are usually installed on one computer on the network, that gates internet connections, and mainly look at the data from packets. Intrusion detection can be cast as a machine learning problem where the t ...
... Host-based IDS look at system data and reside on each computer in a network. Networkbased systems are usually installed on one computer on the network, that gates internet connections, and mainly look at the data from packets. Intrusion detection can be cast as a machine learning problem where the t ...
Part I: Introduction
... m change of implementation of layer’s service transparent to rest of system m e.g., change in gate procedure doesn’t affect rest of system r layering considered harmful? r ...
... m change of implementation of layer’s service transparent to rest of system m e.g., change in gate procedure doesn’t affect rest of system r layering considered harmful? r ...
Chapter 2
... (OSI) reference model was created by the International Organization for Standardization (ISO) to break through this barrier. • The OSI model was meant to help vendors create interoperable network devices and software in the form of protocols so that different vendor networks could work with each oth ...
... (OSI) reference model was created by the International Organization for Standardization (ISO) to break through this barrier. • The OSI model was meant to help vendors create interoperable network devices and software in the form of protocols so that different vendor networks could work with each oth ...
ppt
... (Reading: Kurose-Ross Chap 1) goal: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
... (Reading: Kurose-Ross Chap 1) goal: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
SAC Conference Tutorial
... PBX VoIP line or trunk cards » Call path between IP phones via LAN » Nortel, Siemens, others have systems » Most PBX manufacturers working towards this type of functionality ...
... PBX VoIP line or trunk cards » Call path between IP phones via LAN » Nortel, Siemens, others have systems » Most PBX manufacturers working towards this type of functionality ...
3 - Terena
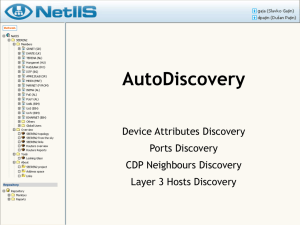
... CDP offers the information about models of these devices, as well as connected ports ...
... CDP offers the information about models of these devices, as well as connected ports ...
Advanced Networks Course Topics
... – Examples include file transfer, electronic mail, remote logon, network management, Web access etc. – This is the traditional type of traffic for which internets were designed – But even amongst these applications there can be differences in requirements ...
... – Examples include file transfer, electronic mail, remote logon, network management, Web access etc. – This is the traditional type of traffic for which internets were designed – But even amongst these applications there can be differences in requirements ...
network terminology
... applcaitons running on the network. It is used to prioritize and assure bandwidth for video and voice streams, specific applications while also ensuring lower priority traffic flows are suc cessfully received and sent. COS, or Class of Service is a way of managing traffic in a network by grouping si ...
... applcaitons running on the network. It is used to prioritize and assure bandwidth for video and voice streams, specific applications while also ensuring lower priority traffic flows are suc cessfully received and sent. COS, or Class of Service is a way of managing traffic in a network by grouping si ...
module 2 network security unit 1
... Data encryption and identity authentication are especially important to securing a VPN. Any open network connection is a vulnerability hackers can exploit to sneak onto your network. Moreover, data is particularly vulnerable while it is traveling over the Internet. Review the documentation for your ...
... Data encryption and identity authentication are especially important to securing a VPN. Any open network connection is a vulnerability hackers can exploit to sneak onto your network. Moreover, data is particularly vulnerable while it is traveling over the Internet. Review the documentation for your ...
ppt - UCF Computer Science
... We’re unable to make secure computer systems or even measure their security. New vulnerabilities kept being exploited Exploit automation and massive global scanning for vulnerabilities to compromise computer systems We use “Honeypot” as one way to get early warnings of new vulnerabilities. ...
... We’re unable to make secure computer systems or even measure their security. New vulnerabilities kept being exploited Exploit automation and massive global scanning for vulnerabilities to compromise computer systems We use “Honeypot” as one way to get early warnings of new vulnerabilities. ...