網路基本觀念 - Yen-Cheng Chen / 陳彥錚
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
Increasing Plant-Level Awareness of the Industrial Network
... With their previous systems, there were only a few nodes to hook up, control, and monitor. This allowed automation and controls engineers and technicians to manage and troubleshoot their networks using programming software tied to the automation system. Now, Industrial Ethernet, which uses standard ...
... With their previous systems, there were only a few nodes to hook up, control, and monitor. This allowed automation and controls engineers and technicians to manage and troubleshoot their networks using programming software tied to the automation system. Now, Industrial Ethernet, which uses standard ...
Working Group on Social Inclusion
... improve social inclusion and employment of Roma community, issued from ESF and other Structural Funds (mainly ERDF) activities and projects. • Learning from EXPERIENCES AND KNOW-HOW among a wide range of actors, such as public authorities, social actors and NGO’s. • DISSEMINATION AND MAINSTREAMING o ...
... improve social inclusion and employment of Roma community, issued from ESF and other Structural Funds (mainly ERDF) activities and projects. • Learning from EXPERIENCES AND KNOW-HOW among a wide range of actors, such as public authorities, social actors and NGO’s. • DISSEMINATION AND MAINSTREAMING o ...
Unit 8 - WordPress.com
... 3. There is no master computer on controller. Every computer has equal chance to place the data and access the token. 4. There are no collisions. 5. Data packets travel at greater speeds. 6. It is easier to locate the problems with device and cable i.e. fault isolation is simplified. If one device d ...
... 3. There is no master computer on controller. Every computer has equal chance to place the data and access the token. 4. There are no collisions. 5. Data packets travel at greater speeds. 6. It is easier to locate the problems with device and cable i.e. fault isolation is simplified. If one device d ...
Slide 1
... The owner of each computer on a P2P network would set aside a portion of its resources—such as processing power, disk storage, or network bandwidth—to be made directly available to other network participant, without the need for central coordination by servers or stable hosts. With this model, peers ...
... The owner of each computer on a P2P network would set aside a portion of its resources—such as processing power, disk storage, or network bandwidth—to be made directly available to other network participant, without the need for central coordination by servers or stable hosts. With this model, peers ...
IP address
... ■ The location (subnet) of the interface (host) in the network ● The IP address is the only “name” carried in an IP ...
... ■ The location (subnet) of the interface (host) in the network ● The IP address is the only “name” carried in an IP ...
Data Safety Monitoring Plan - Kennesaw State University | Office of
... Because the monitoring plan will depend on potential risks, complexity, and the nature of the trial, a number of options for monitoring are possible. These include, but are not limited to, monitoring by a: o PD/PI: While the PD/PI must ensure that the trial is conducted according to the protocol, in ...
... Because the monitoring plan will depend on potential risks, complexity, and the nature of the trial, a number of options for monitoring are possible. These include, but are not limited to, monitoring by a: o PD/PI: While the PD/PI must ensure that the trial is conducted according to the protocol, in ...
Session 13
... • In traditional voice networks, circuits are established that provide for a continuous stream of data; packet switching takes outgoing data and aggregates it into segments called packets • Packets carry up to 1500 bytes at a time • Packets have a header prepended onto the front of the packet that c ...
... • In traditional voice networks, circuits are established that provide for a continuous stream of data; packet switching takes outgoing data and aggregates it into segments called packets • Packets carry up to 1500 bytes at a time • Packets have a header prepended onto the front of the packet that c ...
05. Example Networks..
... at thousands of universities, research labs, libraries, and museums to access any of the supercomputers and to communicate with one another - the complete network was called NSFNET ...
... at thousands of universities, research labs, libraries, and museums to access any of the supercomputers and to communicate with one another - the complete network was called NSFNET ...
Nimbra 688 - Net Insight
... Flexible interfaces Available service interfaces include Gigabit Ethernet, 3G/HD/SD-SDI with optional built in JPEG2000 compression, ASI, AES/EBU and MADI. These services can be aggregated and switched with sub-Mbps granularity onto IP (1 or 10 GbE) or SDH/Sonet network interfaces. ...
... Flexible interfaces Available service interfaces include Gigabit Ethernet, 3G/HD/SD-SDI with optional built in JPEG2000 compression, ASI, AES/EBU and MADI. These services can be aggregated and switched with sub-Mbps granularity onto IP (1 or 10 GbE) or SDH/Sonet network interfaces. ...
Big Data Analytics: Online Condition Health Monitoring Nuclear Automation Background
... Plant-wide application to fleet-wide application This same technology can be applied to monitor multiple components within a plant and provide reliable data to a central data server for additional processing and analysis. Wireless technology eliminates the costs of new cable runs for added measureme ...
... Plant-wide application to fleet-wide application This same technology can be applied to monitor multiple components within a plant and provide reliable data to a central data server for additional processing and analysis. Wireless technology eliminates the costs of new cable runs for added measureme ...
pptx - NOISE
... should be passing through them, when of course it should not. Those portions of the net that are "closer" (in network topology terms) to Con Ed will send them our traffic, which makes us unreachable. ...
... should be passing through them, when of course it should not. Those portions of the net that are "closer" (in network topology terms) to Con Ed will send them our traffic, which makes us unreachable. ...
2007z
... Specific social cohesiveness among social actors regarding to silaturahmi relation depends upon the domain of social interaction, e.g.: the working place, hobbies, interests, of each. Some of the clustered was made by the alumni of same faculties while they were students, while the o ...
... Specific social cohesiveness among social actors regarding to silaturahmi relation depends upon the domain of social interaction, e.g.: the working place, hobbies, interests, of each. Some of the clustered was made by the alumni of same faculties while they were students, while the o ...
3rd Edition: Chapter 2 - Northwestern Networks Group
... links of various media applications protocols hardware, software ...
... links of various media applications protocols hardware, software ...
Enterprise Servers
... This has caused an increase in needed bandwidth. Therefore, design must address... Type of data to be accessed ...
... This has caused an increase in needed bandwidth. Therefore, design must address... Type of data to be accessed ...
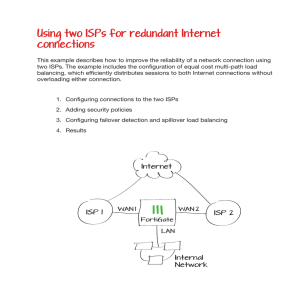
Using two ISPs for redundant Internet connections
... Using two ISPs for redundant Internet connections This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without ...
... Using two ISPs for redundant Internet connections This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without ...
Preventative controls
... • Once the threats are identified they are then ranked according to their occurrence. • Figure 5 summarizes the most common threats to security. • For example, the average cost to clean up a virus that slips through a security system and infects an average number of computers is £70,000/virus. ...
... • Once the threats are identified they are then ranked according to their occurrence. • Figure 5 summarizes the most common threats to security. • For example, the average cost to clean up a virus that slips through a security system and infects an average number of computers is £70,000/virus. ...
Computer-Aided Engineering for Inference of Genetic Regulatory
... Abstract. Biological research topics gradually shift from structural genomics into functional genomics. DNA microarrays have been used to generate abundant data for exploring functions and interactions among genes. We propose a reverse-engineering strategy to predict the interactions between genes w ...
... Abstract. Biological research topics gradually shift from structural genomics into functional genomics. DNA microarrays have been used to generate abundant data for exploring functions and interactions among genes. We propose a reverse-engineering strategy to predict the interactions between genes w ...
Advantages of networking - Cambridge GCSE Computing Online
... (b) Explain what is meant by a ‘local area network’. This is a computer network that connects computers in a limited area or on a single site such as a house, school or office building. (c) Describe two ways in which the computers can communicate with each other. They can be physically connected by ...
... (b) Explain what is meant by a ‘local area network’. This is a computer network that connects computers in a limited area or on a single site such as a house, school or office building. (c) Describe two ways in which the computers can communicate with each other. They can be physically connected by ...
Chapter 1. Introduction to Data Communications
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
SK05_JepsenISIinAction
... – Based on Three Country Pilot experiences • End-user functionality – Based on Three Country Pilot scenarios • Security aspects • Phasing of implementation – Based on Three Country pilot scenarios ...
... – Based on Three Country Pilot experiences • End-user functionality – Based on Three Country Pilot scenarios • Security aspects • Phasing of implementation – Based on Three Country pilot scenarios ...
Proposal Presentation
... Product will be open source and will integrate several available technologies ...
... Product will be open source and will integrate several available technologies ...
QoS Support in 802.11 Wireless LANs
... • Come up with engineering solutions for problems identified from scientific discovery through analysis of operational data and experimentally collected data • Implement software ...
... • Come up with engineering solutions for problems identified from scientific discovery through analysis of operational data and experimentally collected data • Implement software ...