Circuit Services
... • IP networks switch packets of information across shared networks to multiple locations and operate at Layer 3 • Shared packet networks are well suited to applications where data transfers are intermittent, multi-point, or have smaller file size transfer requirements • A “best-effort” service • Rep ...
... • IP networks switch packets of information across shared networks to multiple locations and operate at Layer 3 • Shared packet networks are well suited to applications where data transfers are intermittent, multi-point, or have smaller file size transfer requirements • A “best-effort” service • Rep ...
Linux+ Guide to Linux Certification
... Devices share responsibility for getting data from one point to another Terminators stop signals after reaching end of wire ...
... Devices share responsibility for getting data from one point to another Terminators stop signals after reaching end of wire ...
Network Technology and the 5000 Series
... • DNS servers provide a means of finding the name for an address, or the address for a name. • A server knows about its domain and servers in parent and child domains. • There are often more than one DNS servers for a domain - both have the same information - it is so the network will still operate ...
... • DNS servers provide a means of finding the name for an address, or the address for a name. • A server knows about its domain and servers in parent and child domains. • There are often more than one DNS servers for a domain - both have the same information - it is so the network will still operate ...
Chapter 17 Network Management
... SNPM v2 (2) • Support central or distributed management • In distributes system, some elements operate as manager and agent • Exchanges use SNMP v2 protocol —Simple request/response protocol —Typically uses UDP • Ongoing reliable connection not required • Reduces management overhead ...
... SNPM v2 (2) • Support central or distributed management • In distributes system, some elements operate as manager and agent • Exchanges use SNMP v2 protocol —Simple request/response protocol —Typically uses UDP • Ongoing reliable connection not required • Reduces management overhead ...
Wireless-G - Computer Direct NZ
... and supports both Wired Equivalent Privacy (WEP) and the industrialstrength wireless security of Wi-Fi Protected Access™ (WPA). The Router can serve as a DHCP Server, has a powerful SPI firewall to protect your PCs against intruders and most known Internet attacks, supports VPN pass-through, and can ...
... and supports both Wired Equivalent Privacy (WEP) and the industrialstrength wireless security of Wi-Fi Protected Access™ (WPA). The Router can serve as a DHCP Server, has a powerful SPI firewall to protect your PCs against intruders and most known Internet attacks, supports VPN pass-through, and can ...
CIS222
... Graphics Interchange Fomat (GIF) is a proprietary lossy data compression standard best suited for line drawings with limited colours. The RSVP protocol is used by receivers to reserve resources on all the routers on the path from the transmitter. All point-to-point circuits should be treated as indi ...
... Graphics Interchange Fomat (GIF) is a proprietary lossy data compression standard best suited for line drawings with limited colours. The RSVP protocol is used by receivers to reserve resources on all the routers on the path from the transmitter. All point-to-point circuits should be treated as indi ...
Computer Networks
... • All of the pieces of equipment connected together must be able to understand one another. • A network is organized into workstations, each with its own name and address. • A workstation is a computer connected to a computer network. • It is often set up with the same operating system, applications ...
... • All of the pieces of equipment connected together must be able to understand one another. • A network is organized into workstations, each with its own name and address. • A workstation is a computer connected to a computer network. • It is often set up with the same operating system, applications ...
Datacenter Network Topologies
... • Say we come up with a proper L2 solution that offers multiple paths – What about L2 broadcasts? (e.g. ARP) ...
... • Say we come up with a proper L2 solution that offers multiple paths – What about L2 broadcasts? (e.g. ARP) ...
Secure and Efficient Routing in Heterogeneous Mobile Ad hoc
... technologies that have applications like security and tactical surveillance in military or hostile environments, weather monitoring, distributed computing, fault detection and diagnosis in machinery, large bridges and tall structures, detecting ambient conditions such as temperature, movement, sound ...
... technologies that have applications like security and tactical surveillance in military or hostile environments, weather monitoring, distributed computing, fault detection and diagnosis in machinery, large bridges and tall structures, detecting ambient conditions such as temperature, movement, sound ...
7.6.1: Skills Integration Challenge-Data Link Layer Issues (Instructor
... You will need to configure the server, both routers, and the two PCs. You will not need to configure the switch nor do you need the IOS CLI to configure the routers. Part of the router configuration has already been done for you: all you must do is configure the static routes and the interfaces via ...
... You will need to configure the server, both routers, and the two PCs. You will not need to configure the switch nor do you need the IOS CLI to configure the routers. Part of the router configuration has already been done for you: all you must do is configure the static routes and the interfaces via ...
The Transport Layer
... • Best effort data delivery between processes – No frills, bare bones transport protocol – Packet may be lost, out of order ...
... • Best effort data delivery between processes – No frills, bare bones transport protocol – Packet may be lost, out of order ...
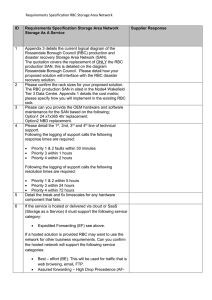
Appendix 2. Requirements Specification RBC Storage Area Network
... onsite engineer support. Covering activities such as manual reboots to any devices or typing in specific commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, ...
... onsite engineer support. Covering activities such as manual reboots to any devices or typing in specific commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, ...
20070716-wenji-demar-bowden
... systems, and identify their configuration problems Identify local network infrastructure problems such as faulted Ethernet connections, malfunctioning NICs, and Ethernet duplex mismatch. ...
... systems, and identify their configuration problems Identify local network infrastructure problems such as faulted Ethernet connections, malfunctioning NICs, and Ethernet duplex mismatch. ...
Penetration Testing Presentation
... White Box Footprinting • Consult the existing network diagram • Scan the network • Compare results – Find running services – Find live hosts • fping, ICMPenum, Ethereal ...
... White Box Footprinting • Consult the existing network diagram • Scan the network • Compare results – Find running services – Find live hosts • fping, ICMPenum, Ethereal ...
Networking
... Metropolitan Area Networks (MAN): A metropolitan area network, or MAN (plural: MANs, not MEN) is basically a bigger version of a LAN and normally uses similar technology. It might cover a group of nearby corporate offices or a city and might be either private or public. A MAN can support both data a ...
... Metropolitan Area Networks (MAN): A metropolitan area network, or MAN (plural: MANs, not MEN) is basically a bigger version of a LAN and normally uses similar technology. It might cover a group of nearby corporate offices or a city and might be either private or public. A MAN can support both data a ...
Airaya CUSTOMER PROFILE
... busiest and most reliable power plants, the Stanton Energy Center’s security plan must account for the large site and the need to monitor the remote locations and multiple entries into the plant. In some cases, the network cameras are located more than three miles away from the security station – a ...
... busiest and most reliable power plants, the Stanton Energy Center’s security plan must account for the large site and the need to monitor the remote locations and multiple entries into the plant. In some cases, the network cameras are located more than three miles away from the security station – a ...
Introduction
... Multiplexers receive multiple lower bit-rate streams of data and according to some rule transmit the higher bit-rate stream of data. Demultiplexers do the opposite. ...
... Multiplexers receive multiple lower bit-rate streams of data and according to some rule transmit the higher bit-rate stream of data. Demultiplexers do the opposite. ...
S3C2 – LAN Switching
... • Both bridges and switches connect LAN segments, use a table of MAC addresses to determine the segment on which a datagram needs to be transmitted, and reduce traffic. • Switches are more functional in today’s networks than bridges because they operate at much higher speeds than bridges and can sup ...
... • Both bridges and switches connect LAN segments, use a table of MAC addresses to determine the segment on which a datagram needs to be transmitted, and reduce traffic. • Switches are more functional in today’s networks than bridges because they operate at much higher speeds than bridges and can sup ...
pptx
... Push packet classification to end hosts Sidecars have better isolation than hypervisor Attack surface limited to network protocols Can spot-check end hosts to remove trust dependencies ...
... Push packet classification to end hosts Sidecars have better isolation than hypervisor Attack surface limited to network protocols Can spot-check end hosts to remove trust dependencies ...
Lecture4_Networking_..
... It is the Network Plumber Its job is to transmit command and control information between networks and systems ...
... It is the Network Plumber Its job is to transmit command and control information between networks and systems ...