Chapter Two_v05
... brain or not. Partially because a mechanism for reverse signaling was not obvious at the time, but most importantly because there was no plausible source for the 'teaching' or 'target' signal. However, since 2006, several unsupervised learning procedures have been proposed for neural networks with o ...
... brain or not. Partially because a mechanism for reverse signaling was not obvious at the time, but most importantly because there was no plausible source for the 'teaching' or 'target' signal. However, since 2006, several unsupervised learning procedures have been proposed for neural networks with o ...
Document
... These protocols were obsoleted by: RFC 1155 — Structure and identification of management information for TCP/IP-based internets RFC 1156 — Management information base for network management of TCP/IP-based internets RFC 1157 — A simple network management protocol ...
... These protocols were obsoleted by: RFC 1155 — Structure and identification of management information for TCP/IP-based internets RFC 1156 — Management information base for network management of TCP/IP-based internets RFC 1157 — A simple network management protocol ...
Security+ 11-Lessons
... secret to X, encrypt the secret with X's public key, then send the encrypted text When X receives the encrypted text, X will decrypt it with a private key Anyone who intercepts the encrypted text cannot decrypt it without X's private key—this is true even if he or she has X’s public key ...
... secret to X, encrypt the secret with X's public key, then send the encrypted text When X receives the encrypted text, X will decrypt it with a private key Anyone who intercepts the encrypted text cannot decrypt it without X's private key—this is true even if he or she has X’s public key ...
GPRS - MobiHealth
... • HLR (Home Location Register): The subscriber file must contain GPRS subscription data: – Address of the SGSN currently serving the subscriber – Addresses of GGSNs that will be contacted when activity from MS is detected – Access Point Name (APN) describing the access point to the external computer ...
... • HLR (Home Location Register): The subscriber file must contain GPRS subscription data: – Address of the SGSN currently serving the subscriber – Addresses of GGSNs that will be contacted when activity from MS is detected – Access Point Name (APN) describing the access point to the external computer ...
Active Switch Systems for Harsh Environments
... of the switch systems available in the network. By simply selecting a switch system, you can set several parameters such as port configuration, SNMP trap receiver, 802.1x, Radius, and many more. The user does not need to have knowledge of complex management software systems in order to perform this ...
... of the switch systems available in the network. By simply selecting a switch system, you can set several parameters such as port configuration, SNMP trap receiver, 802.1x, Radius, and many more. The user does not need to have knowledge of complex management software systems in order to perform this ...
Addresses, Protocols, and Ports Reference
... Example 1—If you have the Class B address 129.10.0.0 and you want to use the entire third octet as part of the extended network prefix instead of the host number, you must specify a subnet mask of 11111111.11111111.11111111.00000000. This subnet mask converts the Class B address into the equivalent ...
... Example 1—If you have the Class B address 129.10.0.0 and you want to use the entire third octet as part of the extended network prefix instead of the host number, you must specify a subnet mask of 11111111.11111111.11111111.00000000. This subnet mask converts the Class B address into the equivalent ...
MediaPlayer™ versus RealPlayer - Computer Science
... Large application frames sent over UDP can result in IP fragmentation. Figure 1 shows the network layer packet arrival pattern for one high encoding rate pair (a 250 Kbps MediaPlayer clip and a 217 Kbps RealPlayer clip). The MediaPlayer packets have a very regular pattern, with groups of packets and ...
... Large application frames sent over UDP can result in IP fragmentation. Figure 1 shows the network layer packet arrival pattern for one high encoding rate pair (a 250 Kbps MediaPlayer clip and a 217 Kbps RealPlayer clip). The MediaPlayer packets have a very regular pattern, with groups of packets and ...
detailed concept of integrated services digital network
... functionality to NT1, and it is usually interface rate of 2.048 Mbps. used with connecting private branch exchange (PBX) devices. CPE can be 4. CONCLUSION considered as an NT2 device. Local Exchange (LE) — it includes Local Termination (LT) and The basic advantage of ISDN is to facilitate Exchange ...
... functionality to NT1, and it is usually interface rate of 2.048 Mbps. used with connecting private branch exchange (PBX) devices. CPE can be 4. CONCLUSION considered as an NT2 device. Local Exchange (LE) — it includes Local Termination (LT) and The basic advantage of ISDN is to facilitate Exchange ...
IP Optical Networks
... Cost Reduction - integrating optics and eliminating mux stages Operation Efficiency - elimination of redundant protocol layers Transport Efficiency - elimination of transport protocol overhead Emergent technology is evolving WDM from optical transport (point-topoint line systems) to true optical net ...
... Cost Reduction - integrating optics and eliminating mux stages Operation Efficiency - elimination of redundant protocol layers Transport Efficiency - elimination of transport protocol overhead Emergent technology is evolving WDM from optical transport (point-topoint line systems) to true optical net ...
ECE537-Class 9_2009 - Electrical & Computer Engineering
... G1, G2 send RSVP request with filter excluding S2 G1, G2 only members of group reached through R4 – R4 doesn’t need to forward packets from this session – R4 merges filter spec requests and sends to R3 ...
... G1, G2 send RSVP request with filter excluding S2 G1, G2 only members of group reached through R4 – R4 doesn’t need to forward packets from this session – R4 merges filter spec requests and sends to R3 ...
3rd Edition, Chapter 5
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address ...
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address ...
Open issues in routing techniques in ad hoc wireless sensor networks
... in practice any better than other methods which have lower theoretical efficiency but provide other practical advantages. Because of these limitations, we consider a variety of protocols, not only those which claim to use “minimal” energy. The SensIT program at DARPA notes that many MANET protocols ...
... in practice any better than other methods which have lower theoretical efficiency but provide other practical advantages. Because of these limitations, we consider a variety of protocols, not only those which claim to use “minimal” energy. The SensIT program at DARPA notes that many MANET protocols ...
BROADBAND SWITCHING AND ACCESS SYSTEM
... Reduced Costs: Due to its architecture, IVI System reduces drastically the communication costs especially for companies with multiple branches (the more branches the lesser Cost/Line ratio). With IVI System there is no need for “n” high capacity lines between the headquarters and the brances. Just a ...
... Reduced Costs: Due to its architecture, IVI System reduces drastically the communication costs especially for companies with multiple branches (the more branches the lesser Cost/Line ratio). With IVI System there is no need for “n” high capacity lines between the headquarters and the brances. Just a ...
ERouting Final Exam
... Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols. Which path will be used to transmit the data packets between PC1 and PC2? The packets ...
... Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols. Which path will be used to transmit the data packets between PC1 and PC2? The packets ...
computer networks sample question bank
... wiring concentrator. This allows not only to detect fault, but also to isolate the faulty link/station with the help of a bypass relay. Q-4. What role the active token monitor performs? Ans. Token ring is maintained with the help of active token monitor. Any one of the stations has the capability to ...
... wiring concentrator. This allows not only to detect fault, but also to isolate the faulty link/station with the help of a bypass relay. Q-4. What role the active token monitor performs? Ans. Token ring is maintained with the help of active token monitor. Any one of the stations has the capability to ...
Module 2: Assigning IP Addresses in a Multiple Subnet
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
View File - University of Engineering and Technology, Taxila
... to a 64-bit value. To do this, we break the MAC address into its two 24-bit halves: the Organizationally Unique Identifier (OUI) and the NIC specific part. The 16-bit hex value 0xFFFE is then inserted between these two halves to form a 64-bit address. ...
... to a 64-bit value. To do this, we break the MAC address into its two 24-bit halves: the Organizationally Unique Identifier (OUI) and the NIC specific part. The 16-bit hex value 0xFFFE is then inserted between these two halves to form a 64-bit address. ...
Introduction to Community-based SNMPv2
... - IETF RFC 1902, "Structure of Management Information for Version 2 of the Simple Network Management Protocol (SNMPv2)", 1996 - IETF RFC 1903, "Textual Conventions for Version 2 of the Simple Network Management Protocol (SNMPv2)", 1996 - IETF RFC 1904, "Conformance Statements for Version 2 of the Si ...
... - IETF RFC 1902, "Structure of Management Information for Version 2 of the Simple Network Management Protocol (SNMPv2)", 1996 - IETF RFC 1903, "Textual Conventions for Version 2 of the Simple Network Management Protocol (SNMPv2)", 1996 - IETF RFC 1904, "Conformance Statements for Version 2 of the Si ...
Link‐State Rou.ng
... • Each router runs Dijkstra’s algorithm – To compute the shortest paths – … and construct the forwarding table ...
... • Each router runs Dijkstra’s algorithm – To compute the shortest paths – … and construct the forwarding table ...
routing101
... CIDR was developed to allow the “subnetting” (flexible address space division between network address and host address) idea to be extended to the network part of the IP address too (called “supernetting”). Recall that subnetting was a method to make address allocation more efficient. - This effecti ...
... CIDR was developed to allow the “subnetting” (flexible address space division between network address and host address) idea to be extended to the network part of the IP address too (called “supernetting”). Recall that subnetting was a method to make address allocation more efficient. - This effecti ...
outdoor environment sensing using wireless sensor networks with
... make multi-functional tiny sensor devices, which can be used to observe and to react according to physical phenomena of their surrounding environment [1]. Wireless sensor nodes are low-power devices equipped with processor, storage, a power supply, a transceiver, one or more sensors and, in some cas ...
... make multi-functional tiny sensor devices, which can be used to observe and to react according to physical phenomena of their surrounding environment [1]. Wireless sensor nodes are low-power devices equipped with processor, storage, a power supply, a transceiver, one or more sensors and, in some cas ...
PDF
... The communication on network on chip is carried out by means of router, so for implementing better NOC, the router should be efficiently design. This router supports three parallel connections at the same time. It uses store and forward type of flow control and FSM Controller deterministic routing w ...
... The communication on network on chip is carried out by means of router, so for implementing better NOC, the router should be efficiently design. This router supports three parallel connections at the same time. It uses store and forward type of flow control and FSM Controller deterministic routing w ...
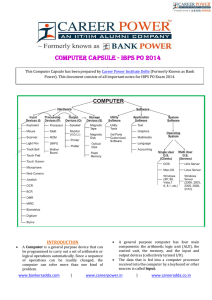
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... data from the user (input), processes the data by performing calculations and operations on it and generates the desired Output. The device which is used with a computer to display or store data is called Peripherals. The mechanical, magnetic, electronic and electrical components that comprises a co ...
... data from the user (input), processes the data by performing calculations and operations on it and generates the desired Output. The device which is used with a computer to display or store data is called Peripherals. The mechanical, magnetic, electronic and electrical components that comprises a co ...