LOCATING THE WISECRACKERS USING SPOOFER
... services of a host connected to the Internet. The most common kind of DoS attack is simply to send more traffic to a network address than the programmers who planned its data buffers [3] anticipated by someone. Although a DoS attack does not usually result in the theft of information or other securi ...
... services of a host connected to the Internet. The most common kind of DoS attack is simply to send more traffic to a network address than the programmers who planned its data buffers [3] anticipated by someone. Although a DoS attack does not usually result in the theft of information or other securi ...
Service-Oriented Software Architecture for Sensor
... void setBaudrate(int handle, int baudrate) ...
... void setBaudrate(int handle, int baudrate) ...
Service-Oriented Software Architecture for Sensor
... void setBaudrate(int handle, int baudrate) ...
... void setBaudrate(int handle, int baudrate) ...
Linksys Gateway SPA2100-SU Manual
... Q. I had to unplug one of my computers to connect the Linksys Gateway to my router. Can I plug that computer into the PC port on the Linksys unit? A. Yes, however you will not be able to share files or printers with the other computers on your network. You may need to purchase a network hub or switc ...
... Q. I had to unplug one of my computers to connect the Linksys Gateway to my router. Can I plug that computer into the PC port on the Linksys unit? A. Yes, however you will not be able to share files or printers with the other computers on your network. You may need to purchase a network hub or switc ...
A random linear network coding approach to multicast
... framework for network coding that extended previous results to arbitrary networks and robust networking, and proved the achievability with time-invariant solutions of the mincut max-flow bound for networks with delay and cycles. Reference [17] also gave an algebraic characterization of the feasibili ...
... framework for network coding that extended previous results to arbitrary networks and robust networking, and proved the achievability with time-invariant solutions of the mincut max-flow bound for networks with delay and cycles. Reference [17] also gave an algebraic characterization of the feasibili ...
the arsenal of sms scammers, spammers and fraudsters
... SMS based exploitation providers actively explore every opportunity to increase their impact while minimising costs and opportunity for detection. This often blurs the line between legitimate business behaviours and others that are shady or simply unacceptable. Mobile Network Operators have to conti ...
... SMS based exploitation providers actively explore every opportunity to increase their impact while minimising costs and opportunity for detection. This often blurs the line between legitimate business behaviours and others that are shady or simply unacceptable. Mobile Network Operators have to conti ...
Intrusion Defense Firewall
... chances of a false negative increase. This again illustrates the importance of, and flexibility in, tuning. Using the right mix of filters is the secret to finding the optimal balance point. The Intrusion Defense Firewall is bi-directional; it allows different rules to be applied to data entering or ...
... chances of a false negative increase. This again illustrates the importance of, and flexibility in, tuning. Using the right mix of filters is the secret to finding the optimal balance point. The Intrusion Defense Firewall is bi-directional; it allows different rules to be applied to data entering or ...
PPT - Suraj @ LUMS
... subscriber stations (SS) with radio base stations (BS) Offers an alternative to cabled access networks – fiber optic links, coaxial cables using cable modems, DSL links Supports nomadic and mobile clients on the go (IEEE 802.16 e, 2004) ...
... subscriber stations (SS) with radio base stations (BS) Offers an alternative to cabled access networks – fiber optic links, coaxial cables using cable modems, DSL links Supports nomadic and mobile clients on the go (IEEE 802.16 e, 2004) ...
Chapter 11
... Tests also should be conducted thoroughly: Test the routing configuration, packet filtering rules (including service-specific testing), and logging and alert options separately and ...
... Tests also should be conducted thoroughly: Test the routing configuration, packet filtering rules (including service-specific testing), and logging and alert options separately and ...
ISIS Introduction - Workshops
... SRM bits: set per interface when a router has to flood an LSP through that interface SSN bits: set per interface when router has to send a PSNP for this LSP ...
... SRM bits: set per interface when a router has to flood an LSP through that interface SSN bits: set per interface when router has to send a PSNP for this LSP ...
Wireless at KU
... all the other system requirements; a new adapter in an old Windows 98 machine won’t work because Windows 98 can’t support WPA2. If the adapter is WPA2-Enterprise certified, update the driver (XP and Vista). Go to the website of the laptop’s manufacturer and install the most current driver for the ne ...
... all the other system requirements; a new adapter in an old Windows 98 machine won’t work because Windows 98 can’t support WPA2. If the adapter is WPA2-Enterprise certified, update the driver (XP and Vista). Go to the website of the laptop’s manufacturer and install the most current driver for the ne ...
Lecture 05
... link-layer device: takes an active role store, forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment transparent hosts are unaware of presence of switches pl ...
... link-layer device: takes an active role store, forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment transparent hosts are unaware of presence of switches pl ...
Next-Generation Optical Transport Networks Demonstrations
... between various vendors equipment. A number of standards that include the Generic Framing Procedure (GFP), Virtual Concatenation (VCAT), and the Link Capacity Adjustment Scheme (LCAS) have been developed to facilitate the mapping of client signals into SONET. Standardized mapping will be required to ...
... between various vendors equipment. A number of standards that include the Generic Framing Procedure (GFP), Virtual Concatenation (VCAT), and the Link Capacity Adjustment Scheme (LCAS) have been developed to facilitate the mapping of client signals into SONET. Standardized mapping will be required to ...
Smoke Alarm - SMSZB-120
... circuit described herein; neither does it convey any license under patent rights or the rights of third parties. ...
... circuit described herein; neither does it convey any license under patent rights or the rights of third parties. ...
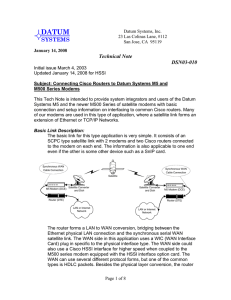
Tech Note - Datum Systems
... link was not correct, then the actual indication would be that the "Link" was down, while if the protocol was not correct then the indication would be that the Link is “Up” and the protocol is “Down”. The M500 series SnIP interface card running Linux can also be used on the other end of a link from ...
... link was not correct, then the actual indication would be that the "Link" was down, while if the protocol was not correct then the indication would be that the Link is “Up” and the protocol is “Down”. The M500 series SnIP interface card running Linux can also be used on the other end of a link from ...
cambium networks solution paper: intercepting
... difficult it is to distinguish the desired incoming signals from the interference. Cambium PMP networks are known for their exceptional ability to decode incoming signals and maximize performance in low C/I environments. Because of their unique design, Cambium radios need a minimum amount of signal ...
... difficult it is to distinguish the desired incoming signals from the interference. Cambium PMP networks are known for their exceptional ability to decode incoming signals and maximize performance in low C/I environments. Because of their unique design, Cambium radios need a minimum amount of signal ...
Chapter_1_V6.1 - Rose
... 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
... 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure 1.4 delay, loss, throughput in networks 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
Network Policy and Access Services in Windows Server 2008
... • Routing and Remote Access Services (RRAS) – Role service used to configure and manage network routing in Windows Server 2008 – Recommended for use in small networks that require ...
... • Routing and Remote Access Services (RRAS) – Role service used to configure and manage network routing in Windows Server 2008 – Recommended for use in small networks that require ...
sensors
... LDAP, and can subscribe to either current or archived sensor event streams directly from sensor managers ...
... LDAP, and can subscribe to either current or archived sensor event streams directly from sensor managers ...
Subnetting & CIDR
... will get one new client with probability 60%, will lose one client with probability 20%, or will maintain the same number with probability 20% ...
... will get one new client with probability 60%, will lose one client with probability 20%, or will maintain the same number with probability 20% ...
chapter 10 - University of Windsor
... To minimize the number of network addresses, the same IP netid must be shared by multiple physical networks, wherever all the host addresses in the allocated IP address have not been used. Three Methods Transparent routers Proxy ARP Standard IP subnets Transparent Routers A WAN with a class A ...
... To minimize the number of network addresses, the same IP netid must be shared by multiple physical networks, wherever all the host addresses in the allocated IP address have not been used. Three Methods Transparent routers Proxy ARP Standard IP subnets Transparent Routers A WAN with a class A ...
Chapter 5
... The first 5 steps used in computing the shortest path from A to D. The arrows indicate the working node. ...
... The first 5 steps used in computing the shortest path from A to D. The arrows indicate the working node. ...