Implementing a Secure Internal Network
... In this step, a DMZ9 is created and devices such as web servers, FTP servers, email servers and DNS servers are moved into this zone. These servers will reside in a secure area that is access controlled for only authorized personnel. This design is called a tri-homed DMZ and we will take one subnet ...
... In this step, a DMZ9 is created and devices such as web servers, FTP servers, email servers and DNS servers are moved into this zone. These servers will reside in a secure area that is access controlled for only authorized personnel. This design is called a tri-homed DMZ and we will take one subnet ...
How to Encrypt with the LPN Problem
... and non-malleability (NM). Indistinguishability deals with the secrecy afforded by the scheme: an adversary must be unable to distinguish the encryption of two (adversarially chosen) plaintexts. This definition was introduced in the context of public-key encryption as a more practical equivalent to ...
... and non-malleability (NM). Indistinguishability deals with the secrecy afforded by the scheme: an adversary must be unable to distinguish the encryption of two (adversarially chosen) plaintexts. This definition was introduced in the context of public-key encryption as a more practical equivalent to ...
Detecting and Mitigating Persistent Javascript eCommerce Malware
... Summary: In February 2017, analysts identified a new technique used with JavaScript-based eCommerce malware that enables the malware to re-infect the website automatically upon incomplete removal. The malware obtains this persistence by modifying the database to force the injection of a malicious Ja ...
... Summary: In February 2017, analysts identified a new technique used with JavaScript-based eCommerce malware that enables the malware to re-infect the website automatically upon incomplete removal. The malware obtains this persistence by modifying the database to force the injection of a malicious Ja ...
Title Size 30PT
... Snort is the most widely deployed IDS/IPS technology worldwide. With millions of downloads and nearly 400,000 registered users, Snort has become the de facto standard for IPS. See more at http://www.snort.org. Never designed to be application aware Presentation_ID ...
... Snort is the most widely deployed IDS/IPS technology worldwide. With millions of downloads and nearly 400,000 registered users, Snort has become the de facto standard for IPS. See more at http://www.snort.org. Never designed to be application aware Presentation_ID ...
Network Security
... (confidentiality, integrity). Authentication protocols verify the source of data. We may also control which traffic is allowed to enter our system (ingress filtering) or to leave our system (egress filtering). Access control decisions based on information like addresses, port numbers, ... ...
... (confidentiality, integrity). Authentication protocols verify the source of data. We may also control which traffic is allowed to enter our system (ingress filtering) or to leave our system (egress filtering). Access control decisions based on information like addresses, port numbers, ... ...
Advanced Threat Protection For Dummies®, Blue Coat Systems
... except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201 ...
... except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201 ...
IBM® Security Network Protection XGS Initial Setup and Deployment
... Applications or IP Reputation data ...
... Applications or IP Reputation data ...
Paper Title (use style: paper title)
... Albandari Alsumayt and John Haggerty [20] discuss various methods to handle the Denial of service attack. Due to the characteristic like dynamically changing network makes the MANETs vulnerable to various kinds of security attacks and one of the serious attacks is Denial of service attack. Denial of ...
... Albandari Alsumayt and John Haggerty [20] discuss various methods to handle the Denial of service attack. Due to the characteristic like dynamically changing network makes the MANETs vulnerable to various kinds of security attacks and one of the serious attacks is Denial of service attack. Denial of ...
Objectives - Sam Bowne
... Define the process of setting up secure remote access for individual users via a VPN Discuss best practices for effective configuration and maintenance of VPNs Introduction Private leased lines Give the user dedicated use of a predefined bandwidth or data rate Often used to connect remote users or b ...
... Define the process of setting up secure remote access for individual users via a VPN Discuss best practices for effective configuration and maintenance of VPNs Introduction Private leased lines Give the user dedicated use of a predefined bandwidth or data rate Often used to connect remote users or b ...
MT311-14
... stability of the computing environment. The safety and stability can be breached in a number of ways. When a malicious application (such as a virus) executes itself, it can cause damage to the system — for example, by deleting some critical files and rendering the computer inoperable. ...
... stability of the computing environment. The safety and stability can be breached in a number of ways. When a malicious application (such as a virus) executes itself, it can cause damage to the system — for example, by deleting some critical files and rendering the computer inoperable. ...
Power Point
... (confidentiality, integrity). Authentication protocols verify the source of data. We may also control which traffic is allowed to enter our system (ingress filtering) or to leave our system (egress filtering). Access control decisions based on information like addresses, port numbers, ... www. ...
... (confidentiality, integrity). Authentication protocols verify the source of data. We may also control which traffic is allowed to enter our system (ingress filtering) or to leave our system (egress filtering). Access control decisions based on information like addresses, port numbers, ... www. ...
Aalborg Universitet Prasad, Neeli R.
... resources among gateways. This approach allows for the application to transparently access thing services irrespective of the gateway that provides the physical thing connection. On top of the TaaS layer, the Service layer is designed to define the platform interface to the external applications. In ...
... resources among gateways. This approach allows for the application to transparently access thing services irrespective of the gateway that provides the physical thing connection. On top of the TaaS layer, the Service layer is designed to define the platform interface to the external applications. In ...
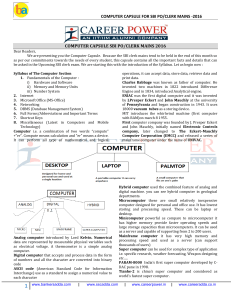
computer capsule for sbi po/clerk mains -2016
... area in a computer in which data is stored for quick access by the computer's processor. The terms random access memory (RAM) and memory are often as synonyms for primary or main storage. Primary storage is volatile and can be contrasted with non-volatile secondary storage, also known as auxiliary s ...
... area in a computer in which data is stored for quick access by the computer's processor. The terms random access memory (RAM) and memory are often as synonyms for primary or main storage. Primary storage is volatile and can be contrasted with non-volatile secondary storage, also known as auxiliary s ...
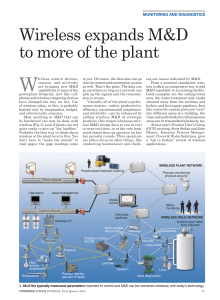
Wireless Expands M D to More of the Plant
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
Windows Firewall
... readdressed, information about protected network is hidden Cons No application Level Security ...
... readdressed, information about protected network is hidden Cons No application Level Security ...
here - HOET
... This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and knowledge required to become competent in their chosen job role and is design ...
... This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and knowledge required to become competent in their chosen job role and is design ...
On Reliable and Fast Resource Sharing in Peer
... Special ones by custom-designed HEC (ES, Blue-gene). Global supercomputing is not cost- and performanceeffective: storing data is much cheaper than transferring. ...
... Special ones by custom-designed HEC (ES, Blue-gene). Global supercomputing is not cost- and performanceeffective: storing data is much cheaper than transferring. ...
Wireless Security
... Primary goals of the attacker are to understand who uses the network,what is accessible, what capabilities of the equipment on the network are, and what the coverage area is. Denial of service Jamming- The entire area including both base station and the clients, is flooded with interference so that ...
... Primary goals of the attacker are to understand who uses the network,what is accessible, what capabilities of the equipment on the network are, and what the coverage area is. Denial of service Jamming- The entire area including both base station and the clients, is flooded with interference so that ...
Computer - CIT Computer Information Technology
... Internet: largest and most well-known computer network in the world Individuals connect to the Internet using an Internet service provider (ISP) Most common Internet activities: e-mail and accessing the World Wide Web (WWW) “Internet” refers to the physical structure of that network, the World Wide ...
... Internet: largest and most well-known computer network in the world Individuals connect to the Internet using an Internet service provider (ISP) Most common Internet activities: e-mail and accessing the World Wide Web (WWW) “Internet” refers to the physical structure of that network, the World Wide ...
Symantec Enterprise Firewalls
... – If a VPN session is active, the proxy-secured, VPN technology decrypts the packet and drops it into the data stream. Next, the firewall performs session checks at the circuit layer and once again, drops and logs bad packets. The integrated intrusion prevention and intrusion detection technologies ...
... – If a VPN session is active, the proxy-secured, VPN technology decrypts the packet and drops it into the data stream. Next, the firewall performs session checks at the circuit layer and once again, drops and logs bad packets. The integrated intrusion prevention and intrusion detection technologies ...
Cisco Platform Exchange Grid (pxGrid) Overview At-A-Glance
... partner platforms the ability to reach into the Cisco network infrastructure to execute network actions on users and devices — such as quarantine and blocking access — via pxGrid and collaboration with Cisco ONE. ...
... partner platforms the ability to reach into the Cisco network infrastructure to execute network actions on users and devices — such as quarantine and blocking access — via pxGrid and collaboration with Cisco ONE. ...
Project proposal
... • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to the user, such as Serial port ...
... • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to the user, such as Serial port ...