Telecommunications
... A PBX system can manage voice and data within a building. Not only does the PBX internally route calls, but it can be used to connect a few external phone lines to numerous internal lines. WATS refers to the use of toll-free numbers. The company pays a fee to the phone company, depending on the vol ...
... A PBX system can manage voice and data within a building. Not only does the PBX internally route calls, but it can be used to connect a few external phone lines to numerous internal lines. WATS refers to the use of toll-free numbers. The company pays a fee to the phone company, depending on the vol ...
Data Source Configuration Guide for McAfee Network Security
... 3. Within the Device List window, select the desired NSM sensor to apply the blacklist setting. Click OK. ...
... 3. Within the Device List window, select the desired NSM sensor to apply the blacklist setting. Click OK. ...
Server hardening - Cisco Security Solutions
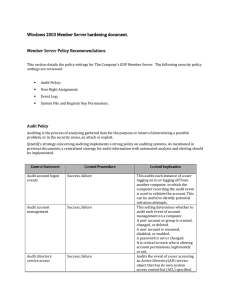
... Audits each instance of a user logging on to, logging off from, or making a network connection to the computer recording the audit event. Useful for forensics purposes. Audits the event of a user accessing an object that has its own system ACLs specified. The object also requires auditing settings t ...
... Audits each instance of a user logging on to, logging off from, or making a network connection to the computer recording the audit event. Useful for forensics purposes. Audits the event of a user accessing an object that has its own system ACLs specified. The object also requires auditing settings t ...
Information Technology - McGraw Hill Higher Education
... Applications software – software designed for a specific task or use Artificial intelligence – behavior performed by a machine that, if performed by a human being, would be called intelligent Operating ...
... Applications software – software designed for a specific task or use Artificial intelligence – behavior performed by a machine that, if performed by a human being, would be called intelligent Operating ...
cis620-14
... • DNS is a naming system used for locating domain names on the Internet and on private TCP/IP networks. DNS provides a service for mapping DNS domain names to IP addresses, and vice versa • Similarities: window 2000 uses DNS naming standards for hierarchical naming of Active Directory domains and co ...
... • DNS is a naming system used for locating domain names on the Internet and on private TCP/IP networks. DNS provides a service for mapping DNS domain names to IP addresses, and vice versa • Similarities: window 2000 uses DNS naming standards for hierarchical naming of Active Directory domains and co ...
SURFboard® SBG6580 DOCSIS 3.0 Wireless Gateway
... seamless interaction among devices such as laptops, PCs, tablets, mobile phones, gaming consoles or any connected device enabling high-quality media streaming, and supporting efficient sharing of media within and outside of the connected home. Capable of supporting IP-based entertainment services, t ...
... seamless interaction among devices such as laptops, PCs, tablets, mobile phones, gaming consoles or any connected device enabling high-quality media streaming, and supporting efficient sharing of media within and outside of the connected home. Capable of supporting IP-based entertainment services, t ...
Cryptanalysis of Stream Cipher
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
IPSec: Cryptography basics
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
PK b
... B adds to the H1-list and responds
to A by setting H1(Wi)=hi.
Note that hi is uniform in G1 and is independent
of A’s current view as required.
Similarly, A queries to H2. B responds to H2(t) by
picking a new random V {0,1}log p for each new t and
setting H2(t)=V. Then, B adds (t, ...
... B adds
Chapter 4
... The threat from outside the organization, who have no legitimate rights to corporate system or information. External threats like “love bug” can create huge economic losses to corporate company with in a short time. Types of external threats: ...
... The threat from outside the organization, who have no legitimate rights to corporate system or information. External threats like “love bug” can create huge economic losses to corporate company with in a short time. Types of external threats: ...
CISSP Common Body of Knowledge
... encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks. The candidate is expected to demonstrate an understanding of communication ...
... encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks. The candidate is expected to demonstrate an understanding of communication ...
PDF
... become important in increasingly large range of applications, such as battlefields and other military environments, disaster areas, and some other activities. A MANET is a multi-hop wireless network (without wire) that is formed dynamically from an accumulation of mobile nodes without the assistance ...
... become important in increasingly large range of applications, such as battlefields and other military environments, disaster areas, and some other activities. A MANET is a multi-hop wireless network (without wire) that is formed dynamically from an accumulation of mobile nodes without the assistance ...
Lecture 13, Part 1
... • But also attacks from major companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
... • But also attacks from major companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
Introduction CS 239 Security for Networks and System
... • But also attacks from major companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
... • But also attacks from major companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
20000525 052 THESIS . I
... the access to information by the users. A mandatory access control policy reflects a set of rules for comparing access classes or classifications. Mandatory access controls are persistent, meaning that the sensivity of information stays the same at all times and global, meaning that information reta ...
... the access to information by the users. A mandatory access control policy reflects a set of rules for comparing access classes or classifications. Mandatory access controls are persistent, meaning that the sensivity of information stays the same at all times and global, meaning that information reta ...
The Layers of OSI Model
... De facto (and after that de jure) standards Open (All modification and newly proposed protocols are published in a form of RFC (Request for Comments) RFC as well as drafts are published on the Internet can be found on many URL (one is www.rfceditor.org) ...
... De facto (and after that de jure) standards Open (All modification and newly proposed protocols are published in a form of RFC (Request for Comments) RFC as well as drafts are published on the Internet can be found on many URL (one is www.rfceditor.org) ...
Lecture 7
... Cyber-crimes and Cyber-criminals • Cyber-crimes are criminal acts conducted through the use of a computer: – Fraud – Identity theft ...
... Cyber-crimes and Cyber-criminals • Cyber-crimes are criminal acts conducted through the use of a computer: – Fraud – Identity theft ...
MOBILE/WIRELESS NETWORKS
... – not only a complex acronym, but also the heart of the channel access providing priorities and different access schemes. – divides the medium access of different competing nodes into ...
... – not only a complex acronym, but also the heart of the channel access providing priorities and different access schemes. – divides the medium access of different competing nodes into ...
product - TechTarget
... network and security teams to provide input into the Lumigent product. You will need system and database administrative credentials for the target databases as well as admin-level access for the system that is going to house the Audit DB reporting engine. Network administrators will help identify pl ...
... network and security teams to provide input into the Lumigent product. You will need system and database administrative credentials for the target databases as well as admin-level access for the system that is going to house the Audit DB reporting engine. Network administrators will help identify pl ...
2/e, by William Stallings and Lawrie Brown, Chapter 9
... advantage of problems within the TCP/IP specification and protocol stack, such as network layer address spoofing . Many packet filter firewalls cannot detect a network packet in which the OSI Layer 3 addressing information has been altered. Spoofing attacks are generally employed by intruders to byp ...
... advantage of problems within the TCP/IP specification and protocol stack, such as network layer address spoofing . Many packet filter firewalls cannot detect a network packet in which the OSI Layer 3 addressing information has been altered. Spoofing attacks are generally employed by intruders to byp ...
TK6383 Rangkaian Komputer
... LAN technology reducing the cost by reducing number of connection But connected computers have to compete for using shared connection Using principle of locality of reference to acquire computer communication pattern. ...
... LAN technology reducing the cost by reducing number of connection But connected computers have to compete for using shared connection Using principle of locality of reference to acquire computer communication pattern. ...
ISO27001 and 27002
... Where did 17799 come from? • BS7799 was conceived, as a technology-neutral, vendorneutral management system that, properly implemented, would enable an organization's management to assure itself that its information security measures and arrangements were effective. • From the outset, BS7799 focuse ...
... Where did 17799 come from? • BS7799 was conceived, as a technology-neutral, vendorneutral management system that, properly implemented, would enable an organization's management to assure itself that its information security measures and arrangements were effective. • From the outset, BS7799 focuse ...
HSTP-CITS-Reqs - Global ITS communication requirements
... range communication - Part 4: Equipment application ...
... range communication - Part 4: Equipment application ...