Top-Down Network Design
... • Deploy network and host IDSs to monitor server subnets and individual servers • Configure filters that limit connectivity from the server in case the server is compromised • Fix known security bugs in server operating ...
... • Deploy network and host IDSs to monitor server subnets and individual servers • Configure filters that limit connectivity from the server in case the server is compromised • Fix known security bugs in server operating ...
CyberShield Command Core
... Managing the cyber battlefield and the proactive cyber defense array to ensure confidentiality, availability and integrity of critical cyber assets ...
... Managing the cyber battlefield and the proactive cyber defense array to ensure confidentiality, availability and integrity of critical cyber assets ...
Database Security - University of Scranton: Computing Sciences Dept.
... people that are allowed to access data and provides a complete mechanism of accessibility To ensure security, the identity is authenticated and it keeps the sensitive data secure and from being modified by any ordinary user. ...
... people that are allowed to access data and provides a complete mechanism of accessibility To ensure security, the identity is authenticated and it keeps the sensitive data secure and from being modified by any ordinary user. ...
William Stallings, Cryptography and Network Security 3/e
... perimeter or a network. • A firewall is simply a program or hardware device that filters the information coming through the Internet connection into your private network or computer system. If an incoming packet of information is flagged by the filters, it is not allowed through. ...
... perimeter or a network. • A firewall is simply a program or hardware device that filters the information coming through the Internet connection into your private network or computer system. If an incoming packet of information is flagged by the filters, it is not allowed through. ...
Nauman Parkar
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC details. ...
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC details. ...
Document
... • Allows the computer system to communicate with the network • Every device that is connected to the LAN will need a NIC, for example, computer, printer and scanner. • It take the data sent by your computer – stores it in its own memory locations, – then adapts it ensuring it follows the communicati ...
... • Allows the computer system to communicate with the network • Every device that is connected to the LAN will need a NIC, for example, computer, printer and scanner. • It take the data sent by your computer – stores it in its own memory locations, – then adapts it ensuring it follows the communicati ...
Communications & Networks
... • Allows the computer system to communicate with the network • Every device that is connected to the LAN will need a NIC, for example, computer, printer and scanner. • It take the data sent by your computer – stores it in its own memory locations, – then adapts it ensuring it follows the communicati ...
... • Allows the computer system to communicate with the network • Every device that is connected to the LAN will need a NIC, for example, computer, printer and scanner. • It take the data sent by your computer – stores it in its own memory locations, – then adapts it ensuring it follows the communicati ...
19-DS-05-2016_OZGUR
... • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Protection, Digital Identities ...
... • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Protection, Digital Identities ...
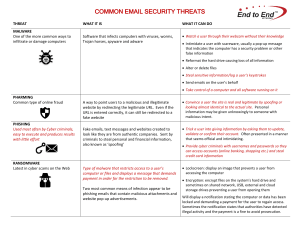
COMMON EMAIL SECURITY THREATS
... website by redirecting the legitimate URL. Even if the URL is entered correctly, it can still be redirected to a fake website ...
... website by redirecting the legitimate URL. Even if the URL is entered correctly, it can still be redirected to a fake website ...
Incident Response and Honeypots
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, then resume operation. 5. Investigate until root cause discovered, then restore system from backups and patch security holes. 6. Call law enforcement before proceeding f ...
... Kill attacker’s processes and/or accounts. Block attacker’s network access to system. Patch and repair what you think was changed, then resume operation. 5. Investigate until root cause discovered, then restore system from backups and patch security holes. 6. Call law enforcement before proceeding f ...
Powerpoint on social impact issuses
... – develop a virus program(usually by hackers) and put it in a network, which not only destroy the data on disks but also spread the network ...
... – develop a virus program(usually by hackers) and put it in a network, which not only destroy the data on disks but also spread the network ...
CSCE 790: Computer Network Security
... Internet Security Association and Key Management Protocol Provide framework for key management Define procedures and packet formats to establish, negotiate, modify, and delete SAs Independent of key exchange protocol, encryption algorithm, and authentication ...
... Internet Security Association and Key Management Protocol Provide framework for key management Define procedures and packet formats to establish, negotiate, modify, and delete SAs Independent of key exchange protocol, encryption algorithm, and authentication ...
Case Study - T-Tech
... Below average connectivity and lacking a well defined data back-up strategy Software Radio Technology had been making do with a technology infrastructure that had past its prime. Although advanced in their early move to cloud computing, the technology had since moved on and improvements needed to be ...
... Below average connectivity and lacking a well defined data back-up strategy Software Radio Technology had been making do with a technology infrastructure that had past its prime. Although advanced in their early move to cloud computing, the technology had since moved on and improvements needed to be ...
File
... • Computer hardware that holds and spins a magnetic or optical disk and reads and writes information on it • They store changing digital information in a relatively permanent form. They give computers the ability to remember things when the power goes out. • Nearly every desktop computer and server ...
... • Computer hardware that holds and spins a magnetic or optical disk and reads and writes information on it • They store changing digital information in a relatively permanent form. They give computers the ability to remember things when the power goes out. • Nearly every desktop computer and server ...
computer security - GH Raisoni Polytechnic, Nagpur
... only those individuals who have the Authority can view a piece of information. 2. Authentication: Authentication deals with the desire to ensure that an individual is who they claim to be. The need for this in an online transaction is obvious. 3. Integrity: Integrity is a related concept but deals w ...
... only those individuals who have the Authority can view a piece of information. 2. Authentication: Authentication deals with the desire to ensure that an individual is who they claim to be. The need for this in an online transaction is obvious. 3. Integrity: Integrity is a related concept but deals w ...
Secure Network Routing: Ariadne and Skipchains
... Solutions Must Pervade Layers • Many security properties are vulnerable at several layers: Application – Availability – Location privacy ...
... Solutions Must Pervade Layers • Many security properties are vulnerable at several layers: Application – Availability – Location privacy ...
Chapter 3 slides
... and web servers connected to the Internet. ◦ In realistic, expect to include several billion nodes and hundreds of millions of active hosts. ◦ These numbers indicate the future changes in size and load that the Internet must handle. ◦ network technologies cope with that or not? ◦ substantial changes ...
... and web servers connected to the Internet. ◦ In realistic, expect to include several billion nodes and hundreds of millions of active hosts. ◦ These numbers indicate the future changes in size and load that the Internet must handle. ◦ network technologies cope with that or not? ◦ substantial changes ...
Riviera Utilities Position Description IT Network Engineer RIVIERA
... benefits of potential actions to choose the most appropriate one. 14. Ability to use inductive and deductive reasoning to combine information and apply general rules to problems in order to analyze information and make decisions. 15. Ability to multi-task, apply time management skills, and successfu ...
... benefits of potential actions to choose the most appropriate one. 14. Ability to use inductive and deductive reasoning to combine information and apply general rules to problems in order to analyze information and make decisions. 15. Ability to multi-task, apply time management skills, and successfu ...
Computer Security and Penetration Testing Chapter 16 Windows
... • Vulnerabilities affecting one or more of these systems include password security, default accounts, file sharing defaults, Windows registry security defaults, trust relationships between domains, Event Viewer buffer overflow, NBNS protocol spoofing, RPC service failure, SMTP authentication, Telnet ...
... • Vulnerabilities affecting one or more of these systems include password security, default accounts, file sharing defaults, Windows registry security defaults, trust relationships between domains, Event Viewer buffer overflow, NBNS protocol spoofing, RPC service failure, SMTP authentication, Telnet ...
BIO-ELECTRO-INFO TECHNOLOGIES TO COMBAT TERRORISM
... Network wiretap comes with a feature called “protocol analysis,” which allows them to decode the computer traffic and make sense of it. Network sniffing has a distinct advantage over telephone wiretaps as many networks use shared media dispensing the need to break into a wiring closet to install the ...
... Network wiretap comes with a feature called “protocol analysis,” which allows them to decode the computer traffic and make sense of it. Network sniffing has a distinct advantage over telephone wiretaps as many networks use shared media dispensing the need to break into a wiring closet to install the ...