Presentation Prepared By: Mohamad Almajali
... contain a high density of weakly protected systems) but appears to be especially concentrated in address ranges commonly associated with home broadband users. Using the previous techniques, many attackers have built sizable networks of DDoS agents, each comprised of thousands of compromised systems. ...
... contain a high density of weakly protected systems) but appears to be especially concentrated in address ranges commonly associated with home broadband users. Using the previous techniques, many attackers have built sizable networks of DDoS agents, each comprised of thousands of compromised systems. ...
Security+ Guide to Network Security Fundamentals, Fourth Edition
... Security+ Guide to Network Security Fundamentals, Fourth Edition ...
... Security+ Guide to Network Security Fundamentals, Fourth Edition ...
A Knowledge Plane for Reasoning about Network
... Differentiating providers and peers. Critical applications can have stringent network reliability and performance requirements. Users of such applications currently differentiate between ISPs based solely on reputation and monitoring. By having devices self-report their properties, NetQuery enables ...
... Differentiating providers and peers. Critical applications can have stringent network reliability and performance requirements. Users of such applications currently differentiate between ISPs based solely on reputation and monitoring. By having devices self-report their properties, NetQuery enables ...
click here
... enable MAC (Media Access Control) filtering. This creates an access control allowing only registered devices to access the wireless network. ...
... enable MAC (Media Access Control) filtering. This creates an access control allowing only registered devices to access the wireless network. ...
glossary - So you Start
... IRC: Internet Chat Relay is an internet text messaging communications protocol. For example, it is used for instant communication, mainly in the form of group chat via discussions forums known as channels or chat rooms. ISP/Access Provider: Internet service provider/internet access provider. Linux K ...
... IRC: Internet Chat Relay is an internet text messaging communications protocol. For example, it is used for instant communication, mainly in the form of group chat via discussions forums known as channels or chat rooms. ISP/Access Provider: Internet service provider/internet access provider. Linux K ...
kjjhghgff
... straight lines between microwave stations Communication satellites are placed in orbit and maintain a constant position above one point of the Earth’s surface IrDA media (also called infrared transmission) send signals using infrared light waves. ...
... straight lines between microwave stations Communication satellites are placed in orbit and maintain a constant position above one point of the Earth’s surface IrDA media (also called infrared transmission) send signals using infrared light waves. ...
Expanded Notes: Common Network Threats Parts 1 and 2
... system from inside the defenses of the network. Social engineering pressure can be applied in multiple forms. An employee can receive a phone call from someone claiming to be from the IT department asking for his or her credentials. It may occur in person. The social engineering can also occur throu ...
... system from inside the defenses of the network. Social engineering pressure can be applied in multiple forms. An employee can receive a phone call from someone claiming to be from the IT department asking for his or her credentials. It may occur in person. The social engineering can also occur throu ...
HumanAut (or SecHCI: Secure Human
... online attacks, since humans can only carry out attacks with much lower speed than computers. ...
... online attacks, since humans can only carry out attacks with much lower speed than computers. ...
BUNDLE PROTOCOL
... IP Address Spoofing • Changing or disguising the source IP address • used by Nmap in decoy mode • Used by Dsniff in dnsspoof attack – DNS response sent by Dsniff contains source address of the DNS server ...
... IP Address Spoofing • Changing or disguising the source IP address • used by Nmap in decoy mode • Used by Dsniff in dnsspoof attack – DNS response sent by Dsniff contains source address of the DNS server ...
MJ-CV-1 - Snap Tech IT
... Installed and upgraded applications, antivirus, applied security updates, patches, service packs and drivers, added printers, configured desktops and migrated users/customers’ profile and data from old ones. Installed, configured, managed and monitored Antivirus on Windows Server 2003 and deploy ...
... Installed and upgraded applications, antivirus, applied security updates, patches, service packs and drivers, added printers, configured desktops and migrated users/customers’ profile and data from old ones. Installed, configured, managed and monitored Antivirus on Windows Server 2003 and deploy ...
Internet Security
... forward or discards the packet The filter is typically set up as a list of rules based on matches to fields in the IP or TCP header The fields are source/destination IP address, port ...
... forward or discards the packet The filter is typically set up as a list of rules based on matches to fields in the IP or TCP header The fields are source/destination IP address, port ...
Unit 27: Planning and Maintaining a Microsoft Windows
... This unit may be delivered stand alone by using the Microsoft Official Curriculum. For students wishing to do all the Microsoft units this will complement Unit 28. They may wish to complete both 27 and unit 28 before attempting the two Microsoft examinations as the knowledge required for both units ...
... This unit may be delivered stand alone by using the Microsoft Official Curriculum. For students wishing to do all the Microsoft units this will complement Unit 28. They may wish to complete both 27 and unit 28 before attempting the two Microsoft examinations as the knowledge required for both units ...
IT Service Delivery and Support Week Four
... connect to the wiring system. Software in the operating system (called drivers) operates the network interface cards. ...
... connect to the wiring system. Software in the operating system (called drivers) operates the network interface cards. ...
The Future of Online Internet Marketing:
... unchangeable characteristics instead of knowledge and it cannot be lost or stolen (Koltzsch 2007). Secondly, biometric identification is more convenient and it is always accessible. After all, one does not have to remember to “carry” biometric identification. It is simply a part of the user. Finally ...
... unchangeable characteristics instead of knowledge and it cannot be lost or stolen (Koltzsch 2007). Secondly, biometric identification is more convenient and it is always accessible. After all, one does not have to remember to “carry” biometric identification. It is simply a part of the user. Finally ...
DoS Attacks On Wireless Voice Over IP Systems
... • as lack of interoperability between systems and platforms, incompatible hardware, difficult upgrades of software and hardware. ...
... • as lack of interoperability between systems and platforms, incompatible hardware, difficult upgrades of software and hardware. ...
The Power of Modern Information Systems
... networks designed by different vendors into a network of networks (the "Internet"). It was initially successful because it delivered a few basic services that everyone needs (file transfer, electronic mail, remote logon) across a very large number of client and server systems. Several computers in a ...
... networks designed by different vendors into a network of networks (the "Internet"). It was initially successful because it delivered a few basic services that everyone needs (file transfer, electronic mail, remote logon) across a very large number of client and server systems. Several computers in a ...
Wannacry Ransomware Alert
... process. Ideally, this data should be kept on a separate device, and backups should be stored offline. Don’t open attachments in unsolicited emails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited email, even if the link seems benign. In cases ...
... process. Ideally, this data should be kept on a separate device, and backups should be stored offline. Don’t open attachments in unsolicited emails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited email, even if the link seems benign. In cases ...
A Wireless Intrusion Detection System and a new
... just saturated. We propose here an attack detection mechanism based on shared monitoring of the network by all nodes. ...
... just saturated. We propose here an attack detection mechanism based on shared monitoring of the network by all nodes. ...
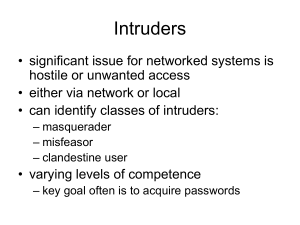
updated system threat and requirements analysis for high assurance
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...
Torguard Ip Checker
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
Document
... Routing is achieved by analyzing the packets of data being sent across a network by a router. Instead of sending the message to all computers in the entire LAN, it is decided by this higher level device. This allows parallel communication to occur within the LAN without being effected by the higher ...
... Routing is achieved by analyzing the packets of data being sent across a network by a router. Instead of sending the message to all computers in the entire LAN, it is decided by this higher level device. This allows parallel communication to occur within the LAN without being effected by the higher ...
Information Technology Security Policy and Minimum Standards for Security of Networked Devices (UCB)
... momentum in the desired direction. Each Berkeley Campus “control unit” head was asked to appoint a member to the Campus Information Security Committee (CISC). Thus, the Committee consists of representatives from a wide range of academic departments and administrative areas. CISC members have respons ...
... momentum in the desired direction. Each Berkeley Campus “control unit” head was asked to appoint a member to the Campus Information Security Committee (CISC). Thus, the Committee consists of representatives from a wide range of academic departments and administrative areas. CISC members have respons ...
Connecting a Computer/ Smartphone/Tablet to the Wireless Network
... Full Support: Licensed versions of Windows 10, 8, 7; Mac OS 10.7 or above and updated versions of the Internet Explorer (for Windows), Safari (for Mac), or Firefox (for Windows or Mac) web browsers. Limited Support: Licensed versions of Windows Vista; Mac OS 10.6; other Internet browsers such as Chr ...
... Full Support: Licensed versions of Windows 10, 8, 7; Mac OS 10.7 or above and updated versions of the Internet Explorer (for Windows), Safari (for Mac), or Firefox (for Windows or Mac) web browsers. Limited Support: Licensed versions of Windows Vista; Mac OS 10.6; other Internet browsers such as Chr ...