Security Management System - Remote Client
... internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. This is common practice followed for security of computers on the internal network. However in some case, it may be needed to grant access to a fe ...
... internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. This is common practice followed for security of computers on the internal network. However in some case, it may be needed to grant access to a fe ...
Design of Secure Multi-Tier Web
... • Transparently weaves adaptive code into CORBA object request brokers (ORBs) at run time using a generic CORBA request interceptor. • The woven code intercepts and adapts the requests, replies, and exceptions that pass through the ORBs ...
... • Transparently weaves adaptive code into CORBA object request brokers (ORBs) at run time using a generic CORBA request interceptor. • The woven code intercepts and adapts the requests, replies, and exceptions that pass through the ORBs ...
Next Generation Security Operation Center for NCHC
... reporting and notifying of events for IP enabled devices • A Self-developed system based on open source software to provides cost-efficient network management services ...
... reporting and notifying of events for IP enabled devices • A Self-developed system based on open source software to provides cost-efficient network management services ...
Designing Technomadic Systems
... For Behemoth, we developed an audio crossbar around the Mitel 8816 microcontroller, vastly simplifying those Spur-of-the moment connections that are irresistibly associated with having lots of devices. It took only a few lines of Forth, for example, to respond to a latitudelongitude change without t ...
... For Behemoth, we developed an audio crossbar around the Mitel 8816 microcontroller, vastly simplifying those Spur-of-the moment connections that are irresistibly associated with having lots of devices. It took only a few lines of Forth, for example, to respond to a latitudelongitude change without t ...
SetNo11
... The Security+ exam is an internationally recognized validation of foundation-level security skills and knowledge ...
... The Security+ exam is an internationally recognized validation of foundation-level security skills and knowledge ...
Document
... primary areas of concern (design goals, security zones, technologies, and business requirements). Describe each area including key topics in each area. 3. Discuss software threats classified as malicious code on page 81 of your text. ...
... primary areas of concern (design goals, security zones, technologies, and business requirements). Describe each area including key topics in each area. 3. Discuss software threats classified as malicious code on page 81 of your text. ...
paper template (word format) for sample
... networks are much more prone denial of service. As a result, the security needs in the wireless ad hoc networks are much higher than those in the wired networks. It has been observed that the existing IDS/IPS performs poorly in detection as well as the false positive rate is higher. It has recently ...
... networks are much more prone denial of service. As a result, the security needs in the wireless ad hoc networks are much higher than those in the wired networks. It has been observed that the existing IDS/IPS performs poorly in detection as well as the false positive rate is higher. It has recently ...
Chapter 6 slides, Computer Networking, 3rd edition
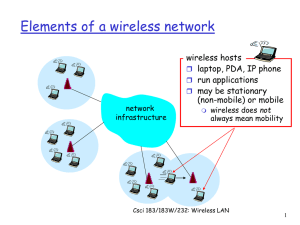
... Ad Hoc Network Approach No access point (i.e., base station) “peer-to-peer” mode ...
... Ad Hoc Network Approach No access point (i.e., base station) “peer-to-peer” mode ...
IDS
... Interfaces to network management applications : SNMP (send traps) Interfaces to network elements : firewall control sessions/connections Service availability aspects Legal aspects : “returning fire” ...
... Interfaces to network management applications : SNMP (send traps) Interfaces to network elements : firewall control sessions/connections Service availability aspects Legal aspects : “returning fire” ...
Synapse Network Operating System
... Self-Healing: Messages automatically re-route around failed nodes ...
... Self-Healing: Messages automatically re-route around failed nodes ...
On Mobile Mesh Networks - International Journal of Open
... Autonomous Mobile Mesh Networks (AMMNET). In a standard wireless mesh network, stationary mesh nodes provide routing and relay capabilities. They form a meshlike wireless network that allows mobile mesh clients to communicate with each other through multi-hop communications. When a mesh node fails, ...
... Autonomous Mobile Mesh Networks (AMMNET). In a standard wireless mesh network, stationary mesh nodes provide routing and relay capabilities. They form a meshlike wireless network that allows mobile mesh clients to communicate with each other through multi-hop communications. When a mesh node fails, ...
ch 13 Information Security
... Wired Equivalent Privacy (WEP) standard - a key encryption technique that assigns keys to wireless nodes. ...
... Wired Equivalent Privacy (WEP) standard - a key encryption technique that assigns keys to wireless nodes. ...
Chapter 6
... • Switched Ethernet, however, runs at up to 95% capacity on 10BaseT. • Another performance improvement can be made by using a 10/100 switch that uses a 100BaseT connection for the server(s) and/or routers, i.e., the network segments experiencing the highest volume of LAN traffic. ...
... • Switched Ethernet, however, runs at up to 95% capacity on 10BaseT. • Another performance improvement can be made by using a 10/100 switch that uses a 100BaseT connection for the server(s) and/or routers, i.e., the network segments experiencing the highest volume of LAN traffic. ...
IF2313881390
... by a group of video sensor nodes that have computing, storage and communication capacity. Video-surveillance in agricultural plots helps the farmers to protect their crops and farm equipment from intruders [9]. Security tasks include intrusion detection and identification. In addition, video surveil ...
... by a group of video sensor nodes that have computing, storage and communication capacity. Video-surveillance in agricultural plots helps the farmers to protect their crops and farm equipment from intruders [9]. Security tasks include intrusion detection and identification. In addition, video surveil ...
Chapter 1. Introduction to Data Communications
... • Switched Ethernet, however, runs at up to 95% capacity on 10BaseT. • Another performance improvement can be made by using a 10/100 switch that uses a 100BaseT connection for the server(s) and/or routers, i.e., the network segments experiencing the highest volume of LAN traffic. ...
... • Switched Ethernet, however, runs at up to 95% capacity on 10BaseT. • Another performance improvement can be made by using a 10/100 switch that uses a 100BaseT connection for the server(s) and/or routers, i.e., the network segments experiencing the highest volume of LAN traffic. ...
P7780
... insufficient to protect computer networks. As crackers hacked away at networks and systems, courses arose that emphasized the latest attacks. Currently, many educators believe that to train people to secure networks, they must also learn to think like a cracker. The following background information ...
... insufficient to protect computer networks. As crackers hacked away at networks and systems, courses arose that emphasized the latest attacks. Currently, many educators believe that to train people to secure networks, they must also learn to think like a cracker. The following background information ...
Go_Net_Security
... Network Adapters • Devices connected to or installed in nodes: – Network interface cards (NIC) – External network adapter ...
... Network Adapters • Devices connected to or installed in nodes: – Network interface cards (NIC) – External network adapter ...
Lesson 1 Computers and Computer Systems
... The term client/server network describes a network design model. In most instances, the client is a software program such as Internet Explorer. The server is hardware (a computer) and can be one of many types, such as a mail server, a database server, an FTP server, an application server, or a Web s ...
... The term client/server network describes a network design model. In most instances, the client is a software program such as Internet Explorer. The server is hardware (a computer) and can be one of many types, such as a mail server, a database server, an FTP server, an application server, or a Web s ...
Access Control
... • Used to authenticate a remote client to a network server (PPP connection on routers) • 3-way handshake that does not send the password – Network access server sends a challenge (session ID and random string) to remote client – Remote client uses a MD5 hash function to create a fixed length string ...
... • Used to authenticate a remote client to a network server (PPP connection on routers) • 3-way handshake that does not send the password – Network access server sends a challenge (session ID and random string) to remote client – Remote client uses a MD5 hash function to create a fixed length string ...
An Investigation into Signal Strength of 802.11n WLAN
... With the continual improvement in IEEE 802.11 standards wireless networks are being deployed in ever increasing numbers. As technology advances the data rates and coverage of Wi-Fi increases and so the usage for different high bandwidth requirement applications increases. These enhancements to the t ...
... With the continual improvement in IEEE 802.11 standards wireless networks are being deployed in ever increasing numbers. As technology advances the data rates and coverage of Wi-Fi increases and so the usage for different high bandwidth requirement applications increases. These enhancements to the t ...
security threats: a guide for small and medium
... attacker needs to target an organization. The firm itself does not need to be specifically picked out but may simply become a victim of an attack aimed at a particular vulnerable software package. Even when user accounts on the network are supposed to have reduced privileges, there may be times wher ...
... attacker needs to target an organization. The firm itself does not need to be specifically picked out but may simply become a victim of an attack aimed at a particular vulnerable software package. Even when user accounts on the network are supposed to have reduced privileges, there may be times wher ...
MCi250 Quick Start Guide
... 2 Repeat step 1 for all encryption keys. If all of the 4 encryption keys are not used in your network, enter “0” (zero) for no encryption key. Wired and wireless connections: If the Streamium does not connect to the Internet The Streamium may not connect to the Internet because a connection error ha ...
... 2 Repeat step 1 for all encryption keys. If all of the 4 encryption keys are not used in your network, enter “0” (zero) for no encryption key. Wired and wireless connections: If the Streamium does not connect to the Internet The Streamium may not connect to the Internet because a connection error ha ...
XORs in The Air: Practical Wireless Network Coding
... • COPE[2](Sigcomm 06) • MORE[3](Sigcomm 07) • MIXIT[4](Sigcomm 08) ...
... • COPE[2](Sigcomm 06) • MORE[3](Sigcomm 07) • MIXIT[4](Sigcomm 08) ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.