Chapter 14 Network Security - Cambridge Regional College
... • Both TCP and UDP use port numbers to address specific applications running on a host. • Both TCP and UDP use port numbers to address specific applications running on a host. • Firewall software must guess at what connectionless traffic is invited and what connectionless traffic is not. • The most ...
... • Both TCP and UDP use port numbers to address specific applications running on a host. • Both TCP and UDP use port numbers to address specific applications running on a host. • Firewall software must guess at what connectionless traffic is invited and what connectionless traffic is not. • The most ...
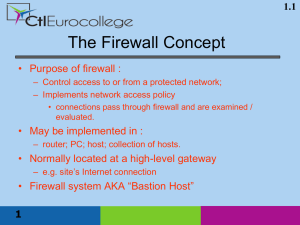
Firewall - theodoros christophides site
... – topology may not lend itself to firewall – cost of introducing firewall may exceed cost of vulnerabilities – alternative solutions may be appropriate ...
... – topology may not lend itself to firewall – cost of introducing firewall may exceed cost of vulnerabilities – alternative solutions may be appropriate ...
File
... It checks the protocol which the packet being delivered and also check port number to which it is being sent. The main function of firewall is to provide centralized access control on how users use the network. ...
... It checks the protocol which the packet being delivered and also check port number to which it is being sent. The main function of firewall is to provide centralized access control on how users use the network. ...
Hands-On Ethical Hacking and Network Security
... – Packet filtering to control incoming traffic – Application filtering through the examination of protocols – Intrusion detection filters – Access policies to control outgoing traffic ...
... – Packet filtering to control incoming traffic – Application filtering through the examination of protocols – Intrusion detection filters – Access policies to control outgoing traffic ...
AppGate Distributed Device Firewall ™ Protecting user devices and the network
... updates firewall rules in the network. Different policies can be defined for different groups of systems on the network based on client type and network address. High availability Multiple Policy Managers can be used to achieve redundancy and load sharing if needed. Auditable system security Adminis ...
... updates firewall rules in the network. Different policies can be defined for different groups of systems on the network based on client type and network address. High availability Multiple Policy Managers can be used to achieve redundancy and load sharing if needed. Auditable system security Adminis ...
BUS 352 Week 4 Discussion 2 (Security components)
... Your businesses network border is the point where your organizations managed network interfaces with un-trusted networks. From a defense in depth perspective, the network perimeter encompasses every point where the internal network is connected to networks and hosts that are not managed by the organ ...
... Your businesses network border is the point where your organizations managed network interfaces with un-trusted networks. From a defense in depth perspective, the network perimeter encompasses every point where the internal network is connected to networks and hosts that are not managed by the organ ...
... regular text – Digital signature: encryption technique used to verify the identity of a message sender for processing online _________ transactions – Firewall: a device that sits between an internal network and the Internet, limiting _________ into and out of a network based on access policies ...
ppt in chapter 11
... for security are based on a some recipe of internal and perimeter routers plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this using access lists. You can see where each of these ...
... for security are based on a some recipe of internal and perimeter routers plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this using access lists. You can see where each of these ...
Using port pairing to simplify transparent mode
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
CH09-CompSec2e - MCST-CS
... segments between server and user must have proxy code for each application may restrict application features supported tend to be more secure than packet filters disadvantage is the additional processing overhead on ...
... segments between server and user must have proxy code for each application may restrict application features supported tend to be more secure than packet filters disadvantage is the additional processing overhead on ...
Firewall Categorization Methods
... Firewalls can be categorized by processing mode, development era, or intended ...
... Firewalls can be categorized by processing mode, development era, or intended ...
Network Technology Foundations
... A secure computer system placed between a trusted network and an untrusted one, such as the Internet • The most common location for a firewall is between a corporate LAN and the Internet Allows users from a protected network to access a public network while simultaneously making the protected compan ...
... A secure computer system placed between a trusted network and an untrusted one, such as the Internet • The most common location for a firewall is between a corporate LAN and the Internet Allows users from a protected network to access a public network while simultaneously making the protected compan ...
Firewalls
... Application Layer Firewall • These are usually hosts that are running proxy servers. • Proxy servers allow for indirect connections between a network and the Internet. • Slower than a Network Firewall, but offers more protection. ...
... Application Layer Firewall • These are usually hosts that are running proxy servers. • Proxy servers allow for indirect connections between a network and the Internet. • Slower than a Network Firewall, but offers more protection. ...
William Stallings, Cryptography and Network Security 3/e
... added on a case-by-case basic, more visible to users who are more likely to see the firewall as a hindrance –Default = forward: that not expressly prohibited is permitted increases ease of use for end users but provides reduced security; the security administrator must, in essence, react to each new ...
... added on a case-by-case basic, more visible to users who are more likely to see the firewall as a hindrance –Default = forward: that not expressly prohibited is permitted increases ease of use for end users but provides reduced security; the security administrator must, in essence, react to each new ...
File
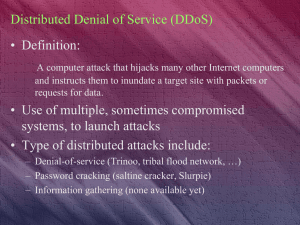
... Cyber stalking is a very a big issue that not many people understand, and what we don’t know is that 1 out of every 10 people is very muck likely to be the prey of one of these stalkers, which also means me and you. That is why people are organizing campaigns for awareness of Internet safety. As a r ...
... Cyber stalking is a very a big issue that not many people understand, and what we don’t know is that 1 out of every 10 people is very muck likely to be the prey of one of these stalkers, which also means me and you. That is why people are organizing campaigns for awareness of Internet safety. As a r ...
Defense Techniques
... • but accesses higher-level protocol information – allows to track sessions (e.g. ftp) – virtual sessions for connection-less protocols (e.g. UDP) • firewall stores ports used in a particular UDP transaction • temporarily creates an exception to let the answer pass ...
... • but accesses higher-level protocol information – allows to track sessions (e.g. ftp) – virtual sessions for connection-less protocols (e.g. UDP) • firewall stores ports used in a particular UDP transaction • temporarily creates an exception to let the answer pass ...
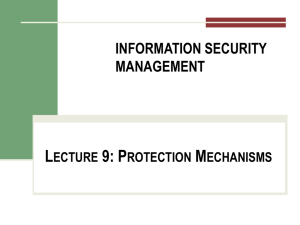
Ch10aProtectionMechanisms
... Consists of dedicated computers kept separate from the first filtering router (edge router) ...
... Consists of dedicated computers kept separate from the first filtering router (edge router) ...
Application level gateway Firewalls - Mercer University
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
... Application level firewalls decide whether to drop a packet or send them through based on the application information. They do this by setting up various proxies on a single firewall for different applications. Both the client and the server connect to these proxies instead of connecting directly t ...
Identity-Based Security
... Permits the administrator to automatically blacklist – or block from all network access – any client that violates specific firewall rules even a single time. This is particularly useful when single-purpose devices such as voice over IP handsets are used. If the Aruba mobility controller detects a v ...
... Permits the administrator to automatically blacklist – or block from all network access – any client that violates specific firewall rules even a single time. This is particularly useful when single-purpose devices such as voice over IP handsets are used. If the Aruba mobility controller detects a v ...
Firewalls
... – Prevents anyone from directly connecting to the firewall over the network (to protect from attacks) – First rule in the firewall rulebase (unless limited connections are explicitly allowed by previous rules) ...
... – Prevents anyone from directly connecting to the firewall over the network (to protect from attacks) – First rule in the firewall rulebase (unless limited connections are explicitly allowed by previous rules) ...
Firewalls
... • IP addresses of hosts on the protected side of the filter can be readily determined by observing the packet traffic on the unprotected side of the filter • filters cannot check all of the fragments of higher level protocols (like TCP) as the TCP header information is only available in the first fr ...
... • IP addresses of hosts on the protected side of the filter can be readily determined by observing the packet traffic on the unprotected side of the filter • filters cannot check all of the fragments of higher level protocols (like TCP) as the TCP header information is only available in the first fr ...
Firewalls
... • IP addresses of hosts on the protected side of the filter can be readily determined by observing the packet traffic on the unprotected side of the filter • filters cannot check all of the fragments of higher level protocols (like TCP) as the TCP header information is only available in the first fr ...
... • IP addresses of hosts on the protected side of the filter can be readily determined by observing the packet traffic on the unprotected side of the filter • filters cannot check all of the fragments of higher level protocols (like TCP) as the TCP header information is only available in the first fr ...