Internet Security
... Packet-filtering routers are simple, transparent to users, and fast Minuses The router cannot prevent attacks that employ application-specific vulnerabilities or functions The logging functionality in the router is limited Most routers do not support advanced user ...
... Packet-filtering routers are simple, transparent to users, and fast Minuses The router cannot prevent attacks that employ application-specific vulnerabilities or functions The logging functionality in the router is limited Most routers do not support advanced user ...
Document
... An attack specifically designed to prevent the normal functioning of a system and thereby to prevent lawful access to the system by authorized users. Hackers can cause denial of service attacks by destroying or modifying data or by overloading the system's servers until service to authorized users i ...
... An attack specifically designed to prevent the normal functioning of a system and thereby to prevent lawful access to the system by authorized users. Hackers can cause denial of service attacks by destroying or modifying data or by overloading the system's servers until service to authorized users i ...
Network Architectures - Computing Sciences
... then discards/forwards them based on rules – Protects against outside attempts to access unauthorized resources, and against malicious network packets intended to disable or cripple a corporate network and its resources – If placed between Internet and corporate network, can restrict users’ access t ...
... then discards/forwards them based on rules – Protects against outside attempts to access unauthorized resources, and against malicious network packets intended to disable or cripple a corporate network and its resources – If placed between Internet and corporate network, can restrict users’ access t ...
d6828939f80d9f863813..
... Assume overall ownership and management of the IT projects and on-going support services. Ensure vendor development, engagement and management. Control and monitor the outsourced services. Procure and manage IT assets. Ascertain security requirements as and when required Provide training to outsourc ...
... Assume overall ownership and management of the IT projects and on-going support services. Ensure vendor development, engagement and management. Control and monitor the outsourced services. Procure and manage IT assets. Ascertain security requirements as and when required Provide training to outsourc ...
Securing a Host Computer
... Windows systems are the most attacked systems on the internet. It is important that system and application updates are done regularly before connecting to the internet. It is also important to configure a current antivirus protection software with all Windows systems due to its high attack rate. ...
... Windows systems are the most attacked systems on the internet. It is important that system and application updates are done regularly before connecting to the internet. It is also important to configure a current antivirus protection software with all Windows systems due to its high attack rate. ...
Suraj September 14, 2013 The Genius Hour: Day 1/2 Hackers: a
... As of now they have just made the firewall stronger so it can check things more deeply and more easily recognize bad things There are many different types of firewalls depending on where the communications is taking place or where it is intercepted Network Layer Firewalls/ Packet filters - allow pac ...
... As of now they have just made the firewall stronger so it can check things more deeply and more easily recognize bad things There are many different types of firewalls depending on where the communications is taking place or where it is intercepted Network Layer Firewalls/ Packet filters - allow pac ...
... Ministry’s network systems; Designs, develops and implements a comprehensive disaster recovery plan and strategies incorporating data and systems configuration backup, redundant devices and a test lab; Manages VOIP infrastructure including adding and reconfiguring IP phones, configuring pick up grou ...
Lesson 7
... Packet Filtering – Also called packet screening: decide to allow or reject specific packets as they enter your network Stateful Inspection – looks at contents of packet not just header Application Level Gateway -- also known as proxy gateways, used to forward service-specific traffic (e.g. email). – ...
... Packet Filtering – Also called packet screening: decide to allow or reject specific packets as they enter your network Stateful Inspection – looks at contents of packet not just header Application Level Gateway -- also known as proxy gateways, used to forward service-specific traffic (e.g. email). – ...
The need for an information policy
... develop a clear policy regarding information access and protection policy to specify who is granted access to which information the rules an individual must follow in disseminating the information to others a statement of how the organisation will react to violations may seem obvious many organisati ...
... develop a clear policy regarding information access and protection policy to specify who is granted access to which information the rules an individual must follow in disseminating the information to others a statement of how the organisation will react to violations may seem obvious many organisati ...
TMDE Web Site
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
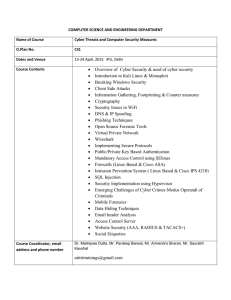
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
NETWORK PLANNING TASK FORCE “FY `06 FALL SESSIONS”
... VPN or Other Options ■ Opportunity: If NetBios is blocked either at the edge or on internal routers, faculty, staff, students with legitimate need for remote access to Windows file sharing, Exchange, etc. need a mechanism or approach to get through the filters. ■ Option 1: Central Campus VPN Servic ...
... VPN or Other Options ■ Opportunity: If NetBios is blocked either at the edge or on internal routers, faculty, staff, students with legitimate need for remote access to Windows file sharing, Exchange, etc. need a mechanism or approach to get through the filters. ■ Option 1: Central Campus VPN Servic ...
Firewalls: An Effective Solution for Internet Security
... connection between two hosts and fabricating packets that bear the address of the host from which the connection has originated. By sending these packets to the destination host, the originating host's connection is dropped, and the attacker picks up the connection. Another Internet security threat ...
... connection between two hosts and fabricating packets that bear the address of the host from which the connection has originated. By sending these packets to the destination host, the originating host's connection is dropped, and the attacker picks up the connection. Another Internet security threat ...
Reading Organizer Instructor Version
... Personal firewalls reside on host computers and are not designed for LAN implementations. They may be available by default from the OS or may be installed from an outside vendor. 21. What is a demilitarized zone or DMZ? In computer networking, a DMZ refers to an area of the network that is accessibl ...
... Personal firewalls reside on host computers and are not designed for LAN implementations. They may be available by default from the OS or may be installed from an outside vendor. 21. What is a demilitarized zone or DMZ? In computer networking, a DMZ refers to an area of the network that is accessibl ...
powerpoint
... • Get an account on the CS Linux servers and run nmap to gain an understanding on the network, the services available for access, their versioning information. • Explain how you can write to /etc/passwd file using passwd command though you do not have rights (as the regular user) to modify the conte ...
... • Get an account on the CS Linux servers and run nmap to gain an understanding on the network, the services available for access, their versioning information. • Explain how you can write to /etc/passwd file using passwd command though you do not have rights (as the regular user) to modify the conte ...
Presentation Slides
... Your network should be behind a hardware firewall, particularly with a high-speed high speed connection. Install a personal firewall to block any content that the hardware may miss. ...
... Your network should be behind a hardware firewall, particularly with a high-speed high speed connection. Install a personal firewall to block any content that the hardware may miss. ...
How Client/Server Networks Work
... access data and files, send e-mail, access the Internet, and print out reports is a small piece of a larger puzzle known as a network. Whether it involves two computers connected by a cable or hundreds of computers linked by telephone lines, networks are becoming increasingly popular in offices and ...
... access data and files, send e-mail, access the Internet, and print out reports is a small piece of a larger puzzle known as a network. Whether it involves two computers connected by a cable or hundreds of computers linked by telephone lines, networks are becoming increasingly popular in offices and ...
CENT 305 Information Security
... Traffic between internal network and Internet traverses two firewalls and DMZ network Hosts in DMZ act as publically accessible servers Traffic entering inner firewally must originate from a host in the DMZ Internal firewalls provide protection between internal subnets ...
... Traffic between internal network and Internet traverses two firewalls and DMZ network Hosts in DMZ act as publically accessible servers Traffic entering inner firewally must originate from a host in the DMZ Internal firewalls provide protection between internal subnets ...
Computer network
... • Firewall A machine and its software that serve as a special gateway to a network, protecting it from inappropriate access – Filter the network traffic that comes in – Check the validity of the messages ...
... • Firewall A machine and its software that serve as a special gateway to a network, protecting it from inappropriate access – Filter the network traffic that comes in – Check the validity of the messages ...
MIDCOM-1
... Static Filtering Policy is not Enough Filtering policy in firewalls can be set up anywhere in the range between the ultimate (see previous slide) and completely open firewall (see what Microsoft suggests to enable NetMeeting in networks with firewalls) The problem: all these policies static; th ...
... Static Filtering Policy is not Enough Filtering policy in firewalls can be set up anywhere in the range between the ultimate (see previous slide) and completely open firewall (see what Microsoft suggests to enable NetMeeting in networks with firewalls) The problem: all these policies static; th ...
Distributed Information System 2010 SUMMARY
... principles behind transport layer services: multiplexing, demultiplexing reliable data transfer flow control congestion control ...
... principles behind transport layer services: multiplexing, demultiplexing reliable data transfer flow control congestion control ...
firewalls
... as the implementation strategy is simple If administrative interfaces use physical network ports as the highest-level construct ...
... as the implementation strategy is simple If administrative interfaces use physical network ports as the highest-level construct ...
Secure Group Communications in Wireless Sensor Networks
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
Network Security
... application such as FTP Circuit-level gateway: used while a connection is being established Proxy server: improves network performance by filtering requests; all requests go through proxy before reaching the real network ...
... application such as FTP Circuit-level gateway: used while a connection is being established Proxy server: improves network performance by filtering requests; all requests go through proxy before reaching the real network ...