Customizable Resource Management for Value
... – Vastly different router & link capacities » Send packets from source to destination by hopping through networks – Router connect one network to another – Different paths to destination may exist ...
... – Vastly different router & link capacities » Send packets from source to destination by hopping through networks – Router connect one network to another – Different paths to destination may exist ...
Higher Computing – Unit 3
... Encrypting data is a method of coding it, in order to make it difficult or even impossible for someone to read it unless they have authorisation from you. Some governments make encrypting data illegal, others regard it as an individual right. As with all security systems, there is a trade-off betwee ...
... Encrypting data is a method of coding it, in order to make it difficult or even impossible for someone to read it unless they have authorisation from you. Some governments make encrypting data illegal, others regard it as an individual right. As with all security systems, there is a trade-off betwee ...
2014 - Bhulabhai Vanmalibhai Patel Institute of Business
... LANs are normally installed and maintained by the organization. LANs have data rates in the range 7 to 16. The physical layer deals with the transfer of bits over a communication channel. Network architecture is optional for network designers. The 1990 saw the emergence of the world wide war. Transf ...
... LANs are normally installed and maintained by the organization. LANs have data rates in the range 7 to 16. The physical layer deals with the transfer of bits over a communication channel. Network architecture is optional for network designers. The 1990 saw the emergence of the world wide war. Transf ...
Bearer Independent Call Control
... services across a broadband backbone network without impacting the interfaces to the existing N-ISDN network and end-to-end services. • The BICC call control signaling protocol is based on N-ISUP ...
... services across a broadband backbone network without impacting the interfaces to the existing N-ISDN network and end-to-end services. • The BICC call control signaling protocol is based on N-ISUP ...
RTP Real-Time Transport Protocol
... – RFC 1889 approved in 1996 – RFC 3550 approved in 2003 • Functionally identical with 1880 • Updates to rules and algorithms governing how the protocol is to be used ...
... – RFC 1889 approved in 1996 – RFC 3550 approved in 2003 • Functionally identical with 1880 • Updates to rules and algorithms governing how the protocol is to be used ...
IP connectivity access network
... In 2G mobile networks the visited service control is in use when a user is roaming, an entity (visited mobile service switching centre) in the visited network provides services and controls the traffic for the user In the early days of Release 5 both visited and home service control models wer ...
... In 2G mobile networks the visited service control is in use when a user is roaming, an entity (visited mobile service switching centre) in the visited network provides services and controls the traffic for the user In the early days of Release 5 both visited and home service control models wer ...
No Slide Title
... • It may consist of many interlinked local area networks and also use leased lines in a wide area network. ...
... • It may consist of many interlinked local area networks and also use leased lines in a wide area network. ...
Recurrent Security Gaps In 802.11ac Routers
... wireless network standards and amendment since the initial 802.11 standard in 1997, namely 802.11a, 802.11b, 802.11g, security amendment 802.11i, 802.11n and the 802.11ac [1]. Each standard implemented a few improved characteristics, such as better security using 802.11i standard. A router is a netw ...
... wireless network standards and amendment since the initial 802.11 standard in 1997, namely 802.11a, 802.11b, 802.11g, security amendment 802.11i, 802.11n and the 802.11ac [1]. Each standard implemented a few improved characteristics, such as better security using 802.11i standard. A router is a netw ...
Student Workbook
... 12. Describe the components of a typical high-speed data access system for a service offering by a cable telecommunications company, and explain how a subscriber is part of a LAN. In your descriptions, be sure to include the physical form of the digital signal at the interfaces to each component. ...
... 12. Describe the components of a typical high-speed data access system for a service offering by a cable telecommunications company, and explain how a subscriber is part of a LAN. In your descriptions, be sure to include the physical form of the digital signal at the interfaces to each component. ...
Ambient Networks – An Architecture for Communication Networks Beyond 3G
... architectural principles and tenets, which guide the development of a new Internet architecture. In parallel to these efforts, which adopt a top-down analysis, several technology-focused activities exist working on solutions for new naming and addressing schemes, QoS support and routing (e.g. [5]). ...
... architectural principles and tenets, which guide the development of a new Internet architecture. In parallel to these efforts, which adopt a top-down analysis, several technology-focused activities exist working on solutions for new naming and addressing schemes, QoS support and routing (e.g. [5]). ...
Selective and Early Threat Detection in Large Networked
... alert management and distributed architectures for intrusion detection. The process of automatically ranking alerts on the basis of threat level has been defined alert verification in [21] and [22]. According to the taxonomy proposed in these papers, our proposal can be classified as a passive alert ...
... alert management and distributed architectures for intrusion detection. The process of automatically ranking alerts on the basis of threat level has been defined alert verification in [21] and [22]. According to the taxonomy proposed in these papers, our proposal can be classified as a passive alert ...
429-07a-TCPIP
... Make a call to the “resolver” (or, in most PCs, the “stub resolver”) to get a numeric address. The answer may come from local storage, or may itself require a network transmission using the Domain Name System (DNS) protocols. The name space and the address space are unrelated, except that they ...
... Make a call to the “resolver” (or, in most PCs, the “stub resolver”) to get a numeric address. The answer may come from local storage, or may itself require a network transmission using the Domain Name System (DNS) protocols. The name space and the address space are unrelated, except that they ...
paper
... systems, lambda management, SONET/SDH multiservice nodes and gateways (Alcatel's term for optical switches), and a control plane based on a GMPLS protocol and ASON standards (in the future). It has a centralized algorithm for automatic discovery of spare network capacity. By taking into account a pr ...
... systems, lambda management, SONET/SDH multiservice nodes and gateways (Alcatel's term for optical switches), and a control plane based on a GMPLS protocol and ASON standards (in the future). It has a centralized algorithm for automatic discovery of spare network capacity. By taking into account a pr ...
network
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure ...
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure ...
20050718-Abilene-Cotter
... telecoms for raw assets & ancillary services • Upwards of 30,000 route-miles of inter-city dark fiber are held by the U.S. R&E community • > 60% in the regionals ...
... telecoms for raw assets & ancillary services • Upwards of 30,000 route-miles of inter-city dark fiber are held by the U.S. R&E community • > 60% in the regionals ...
Lecture 10 Overview!
... ! Corporate and Organisational Security – Enabling the use of wireless networks in applications where (WiFi) presents a security risk! ! Location-Based Services – Highly accurate locationspecific information services such as advertising and navigation that enables the recipient to receive appropri ...
... ! Corporate and Organisational Security – Enabling the use of wireless networks in applications where (WiFi) presents a security risk! ! Location-Based Services – Highly accurate locationspecific information services such as advertising and navigation that enables the recipient to receive appropri ...
Snort - an network intrusion prevention and detection system
... signature, protocol and anomaly inspection methods the most widely deployed intrusion detection and prevention technology and it has become the de facto standard technology worldwide in the industry. ...
... signature, protocol and anomaly inspection methods the most widely deployed intrusion detection and prevention technology and it has become the de facto standard technology worldwide in the industry. ...
Introduction to Computer Security
... – A network device that provides service to the network users by managing shared resources. ...
... – A network device that provides service to the network users by managing shared resources. ...
Issue - GiaSpace
... Computer with ePHI does not have object level auditing on (11 pts) Issue: Object level auditing helps identify users who have accessed files and other system resources. Object level auditing may impose an unacceptable performance impact and should be considered for use on high risk computers or envi ...
... Computer with ePHI does not have object level auditing on (11 pts) Issue: Object level auditing helps identify users who have accessed files and other system resources. Object level auditing may impose an unacceptable performance impact and should be considered for use on high risk computers or envi ...
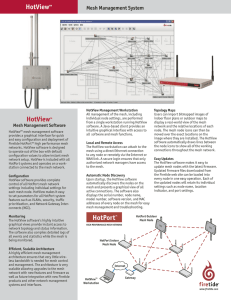
HotViewTM HotView™
... The main HotView screen provides a graphical view of the mesh network, displaying an icon for each of the nodes with lines showing the various connections among the nodes. Icons can be moved to any position on the screen, allowing users to place them in their relative positions over the background i ...
... The main HotView screen provides a graphical view of the mesh network, displaying an icon for each of the nodes with lines showing the various connections among the nodes. Icons can be moved to any position on the screen, allowing users to place them in their relative positions over the background i ...