Cisco Medianet Readiness Assessment
... meet user needs and expectations, regardless of their location, the device they are using, or the content they are accessing. IT groups are tasked with specifying and implementing the network requirements that will support video for rich media applications addressing a broad range of organization ne ...
... meet user needs and expectations, regardless of their location, the device they are using, or the content they are accessing. IT groups are tasked with specifying and implementing the network requirements that will support video for rich media applications addressing a broad range of organization ne ...
OSI Network Layer
... 5.2.2 Why Separate Hosts Into Networks? Performance Dividing large networks so that hosts who need to communicate are grouped together reduces the traffic across the internetworks. Broadcasts are contained within a network, so a network is also known as a broadcast domain. ...
... 5.2.2 Why Separate Hosts Into Networks? Performance Dividing large networks so that hosts who need to communicate are grouped together reduces the traffic across the internetworks. Broadcasts are contained within a network, so a network is also known as a broadcast domain. ...
Cisco Medianet Readiness Assessment
... meet user needs and expectations, regardless of their location, the device they are using, or the content they are accessing. IT groups are tasked with specifying and implementing the network requirements that will support video for rich media applications addressing a broad range of organization ne ...
... meet user needs and expectations, regardless of their location, the device they are using, or the content they are accessing. IT groups are tasked with specifying and implementing the network requirements that will support video for rich media applications addressing a broad range of organization ne ...
EVVBU Marketing Strategy Development Session
... • By tying EAP into the bigger picture, so to speak. EAP conducts the authentication process. It ties Point-to-Point Protocol (PPP) to the physical layer, OSI Layer 1. • EAP over LAN (EAPOL) is EAP encapsulated into 802 frames. This is how the Authenticator and Supplicant actually communicate during ...
... • By tying EAP into the bigger picture, so to speak. EAP conducts the authentication process. It ties Point-to-Point Protocol (PPP) to the physical layer, OSI Layer 1. • EAP over LAN (EAPOL) is EAP encapsulated into 802 frames. This is how the Authenticator and Supplicant actually communicate during ...
INM2007
... 1. Migration software signals to “network” that IPa will (soon) migrate from PEa to PEb 2. “Network” creates a tunnel between PEa and PEb 3. Server migration executed between PSa and PSb 4. Migration software signals to “network” that switchover should take place 5. PEa switches all traffic towards ...
... 1. Migration software signals to “network” that IPa will (soon) migrate from PEa to PEb 2. “Network” creates a tunnel between PEa and PEb 3. Server migration executed between PSa and PSb 4. Migration software signals to “network” that switchover should take place 5. PEa switches all traffic towards ...
The Announcement Layer: Beacon Coordination for
... – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
... – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
NetVanta 6330 Series - Walker and Associates
... customer’s voice quality. A variety of ease-of-use features and graphical information are available for troubleshooting, rapid firmware updates or configuration upgrades. Security The NetVanta 6330 provides a powerful, high performance, stateful inspection firewall that can identify and protect agai ...
... customer’s voice quality. A variety of ease-of-use features and graphical information are available for troubleshooting, rapid firmware updates or configuration upgrades. Security The NetVanta 6330 provides a powerful, high performance, stateful inspection firewall that can identify and protect agai ...
Socket Programming - Wichita State University
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
Middleware and Distributed Systems
... Distributed Middleware Provides a comprehensive set of higher-level distributed computing capabilities and a set of interfaces to access the capabilities of the system. Includes software technologies to help manage complexity and heterogeneity inherent to the development of distributed systems ...
... Distributed Middleware Provides a comprehensive set of higher-level distributed computing capabilities and a set of interfaces to access the capabilities of the system. Includes software technologies to help manage complexity and heterogeneity inherent to the development of distributed systems ...
PPT
... ◦ instead of multicasting protocol to register and release the multicast membership. ◦ receive and transmit the IGMP messages on behalf of IP STB. ...
... ◦ instead of multicasting protocol to register and release the multicast membership. ◦ receive and transmit the IGMP messages on behalf of IP STB. ...
Socket Programming
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
Socket Programming
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
... destination node based on its address • Types of addresses – unicast: node-specific – broadcast: all nodes on the network – multicast: some subset of nodes on the network ...
2._ids_with_snort_1
... to permit detection. These generate many false alarms and hence compromise the effectiveness of the IDS. ...
... to permit detection. These generate many false alarms and hence compromise the effectiveness of the IDS. ...
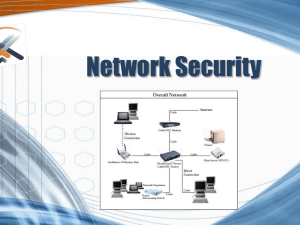
Network Security
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
The OSI Model: Understanding the Seven Layers of Computer
... Initially, software manufacturers, such as Novell, developed proprietary layer 3 addressing. However, the networking industry has evolved to the point that it requires a common layer 3 addressing system. The Internet Protocol (IP) addresses make networks easier to both set up and connect with one an ...
... Initially, software manufacturers, such as Novell, developed proprietary layer 3 addressing. However, the networking industry has evolved to the point that it requires a common layer 3 addressing system. The Internet Protocol (IP) addresses make networks easier to both set up and connect with one an ...
Slide 1
... Identify flows by connection identifier rather than source/destination address (tag switching) ENTS689L: Packet Processing and Switching Networking Technologies ...
... Identify flows by connection identifier rather than source/destination address (tag switching) ENTS689L: Packet Processing and Switching Networking Technologies ...
Peer-to-Peer Networks For Content Sharing
... (Turcan, 2002). In other words, no one will ever be totally sure how the Napster protocol specification is like, except for the creator of Napster himself. Project OpenNap has made it possible to run a Napster server on many platforms without using the original Napster application and the index serv ...
... (Turcan, 2002). In other words, no one will ever be totally sure how the Napster protocol specification is like, except for the creator of Napster himself. Project OpenNap has made it possible to run a Napster server on many platforms without using the original Napster application and the index serv ...
Catalyst 3560-E Series Aggregation Switch Solutions BDM
... maintaining quality of service for day-to-day procedures and system availability.” Stephane Tsacas, Head of computer networking, Institut Curie ...
... maintaining quality of service for day-to-day procedures and system availability.” Stephane Tsacas, Head of computer networking, Institut Curie ...
Large-Scale Network Topology Emulation and Inference
... of ASes that were not discovered by our scamper probing. • 3 to 272 ASes not discovered; mean of 61 ASes missed. • In the after-failures probing round, disconnections are evident • 1 to 285 ASes missed; mean of 5 ASes missed. ...
... of ASes that were not discovered by our scamper probing. • 3 to 272 ASes not discovered; mean of 61 ASes missed. • In the after-failures probing round, disconnections are evident • 1 to 285 ASes missed; mean of 5 ASes missed. ...
PowerPoint Sunusu
... Q: How does a host get IP address? • hard-coded by system admin in a file – Windows: control-panel->network>configuration->tcp/ip->properties – UNIX: /etc/rc.config ...
... Q: How does a host get IP address? • hard-coded by system admin in a file – Windows: control-panel->network>configuration->tcp/ip->properties – UNIX: /etc/rc.config ...
Distributed Call Admission Control for Ad Hoc Networks
... This procedure will continue for all packets in the backlogged queue. If the ratio of the nonconforming traffic to the total submitted traffic is larger than a preselected threshold, the connection cannot be supported by the network and it should be terminated. The acceptance threshold is a paramete ...
... This procedure will continue for all packets in the backlogged queue. If the ratio of the nonconforming traffic to the total submitted traffic is larger than a preselected threshold, the connection cannot be supported by the network and it should be terminated. The acceptance threshold is a paramete ...
Liu-TMC07-slide
... Support both mobile and stationary query nodes Entry point can be anywhere in the network and occurs at any time Assume that the speed of the mobile node is much smaller than that of communication in the sense that disconnection does not happen during a query process Assume all nodes in the network ...
... Support both mobile and stationary query nodes Entry point can be anywhere in the network and occurs at any time Assume that the speed of the mobile node is much smaller than that of communication in the sense that disconnection does not happen during a query process Assume all nodes in the network ...