Liu-TMC07-slide
... Support both mobile and stationary query nodes Entry point can be anywhere in the network and occurs at any time Assume that the speed of the mobile node is much smaller than that of communication in the sense that disconnection does not happen during a query process Assume all nodes in the network ...
... Support both mobile and stationary query nodes Entry point can be anywhere in the network and occurs at any time Assume that the speed of the mobile node is much smaller than that of communication in the sense that disconnection does not happen during a query process Assume all nodes in the network ...
03_tcom5272_tcpip
... Static routing means that the network administrator directly assigns the path router are to take to the destination Static routing is most often used with stub networks where only one path exists to the destination ...
... Static routing means that the network administrator directly assigns the path router are to take to the destination Static routing is most often used with stub networks where only one path exists to the destination ...
Basics of Networking
... structures and converting from the representation used inside the computer to the network standard representation an visa versa. In English terms, the Presentation layer basically takes the packets and re-assembles them so you can open the e-mail or the attachment. If any packets got lost along the ...
... structures and converting from the representation used inside the computer to the network standard representation an visa versa. In English terms, the Presentation layer basically takes the packets and re-assembles them so you can open the e-mail or the attachment. If any packets got lost along the ...
ppt
... of address • Do not use classes to determine network ID • Use common part of address as network number • E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number 192.4.16/20 ...
... of address • Do not use classes to determine network ID • Use common part of address as network number • E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number 192.4.16/20 ...
White Paper - DC
... • Signals appear and disappear simply because you move your phone six inches • You can hear the other person, but they can’t hear you • Calls get “Dropped” and require re-connection • Problems are compounded by reflections inside of buildings (multipath) • Interference from other RF sources garbles ...
... • Signals appear and disappear simply because you move your phone six inches • You can hear the other person, but they can’t hear you • Calls get “Dropped” and require re-connection • Problems are compounded by reflections inside of buildings (multipath) • Interference from other RF sources garbles ...
Requirements and a draft architecture of the second version of UCLP
... • An interface web service is a web service representation of a slot/port/channel. It provides a set of services such as addDrop, unAddDrop, … • An Articulated Private Network, APN, is a collection of individual lightpath and interface web services from different network operators that are linked to ...
... • An interface web service is a web service representation of a slot/port/channel. It provides a set of services such as addDrop, unAddDrop, … • An Articulated Private Network, APN, is a collection of individual lightpath and interface web services from different network operators that are linked to ...
Important Questions for (CS) Board Examination-2016-17
... (d) Briefly mention two advantages and disadvantages of Ring topology in network. ...
... (d) Briefly mention two advantages and disadvantages of Ring topology in network. ...
Slide 1
... Segmenting a Network • Decreases amount of traffic on overall network • Done through use of bridges and switches – More intelligent than hubs; make decisions about whether or not to allow traffic to pass, or where to forward that traffic – Use MAC addresses, which they store in routing tables, to d ...
... Segmenting a Network • Decreases amount of traffic on overall network • Done through use of bridges and switches – More intelligent than hubs; make decisions about whether or not to allow traffic to pass, or where to forward that traffic – Use MAC addresses, which they store in routing tables, to d ...
Know When It`s Time to Replace Enterprise Network Equipment
... upgrades, but these former norms have changed considerably. Due to the increased standardization and stable requirements of edge switching, limited lifetime warranties offered by several vendors and increasing MTBF, the useful life of this type of equipment has increased to seven to 10 years. As a r ...
... upgrades, but these former norms have changed considerably. Due to the increased standardization and stable requirements of edge switching, limited lifetime warranties offered by several vendors and increasing MTBF, the useful life of this type of equipment has increased to seven to 10 years. As a r ...
Red Teaming: The Art of Ethical Hacking
... [JP1] 2. With respect to classified matter, the condition that prevents unauthorized persons from having access to official information that is safeguarded in the interests of national security. [After JP1] 3. Measures taken by a military unit, an activity or installation to protect itself against a ...
... [JP1] 2. With respect to classified matter, the condition that prevents unauthorized persons from having access to official information that is safeguarded in the interests of national security. [After JP1] 3. Measures taken by a military unit, an activity or installation to protect itself against a ...
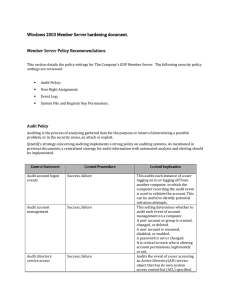
Server hardening - Cisco Security Solutions
... local guest account and other accounts that have no business reason for accessing the computer over the network, provides an additional layer of protection. N.B.: an important exception to this list is any service account that is used to launch services that need to connect to the computer over the ...
... local guest account and other accounts that have no business reason for accessing the computer over the network, provides an additional layer of protection. N.B.: an important exception to this list is any service account that is used to launch services that need to connect to the computer over the ...
Gateways - Sistel IMT 2010
... • Gateways B and D each have copies of the other's routing tables, as well. • These copies are transmitted at intervals so the gateways can maintain an up-to-date picture of the connections available through the other gateway. • The gateways use EGP to send the messages. (They would use GGP if they ...
... • Gateways B and D each have copies of the other's routing tables, as well. • These copies are transmitted at intervals so the gateways can maintain an up-to-date picture of the connections available through the other gateway. • The gateways use EGP to send the messages. (They would use GGP if they ...
course-file-web
... the Open Systems Interconnection (OSI) reference model in 1977. It has since become the most widely accepted model for understanding network communication; once you understand how the OSI model works, you can use it to compare network implementations on different systems. When you want to communicat ...
... the Open Systems Interconnection (OSI) reference model in 1977. It has since become the most widely accepted model for understanding network communication; once you understand how the OSI model works, you can use it to compare network implementations on different systems. When you want to communicat ...
7.1 ENUM and number portability
... types of addressing can be used. Unfortunately, this would require the user to know on what type of network the destination is. When IP telephony is largely deployed, customers do not necessary even know the underlying technology of their own connection. As we saw in section 2.1, E.164 numbers can c ...
... types of addressing can be used. Unfortunately, this would require the user to know on what type of network the destination is. When IP telephony is largely deployed, customers do not necessary even know the underlying technology of their own connection. As we saw in section 2.1, E.164 numbers can c ...
Chapter 1. Introduction to Data Communications
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
... Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of ...
3. Centralized versus Distributed Mobility
... More than ever, mobile users are consuming Internet content, including that of local Content Delivery Networks (CDNs). Such traffic imposes new requirements on mobile core networks for data traffic delivery. To prevent exceeding the available core network capacity, service providers need to implemen ...
... More than ever, mobile users are consuming Internet content, including that of local Content Delivery Networks (CDNs). Such traffic imposes new requirements on mobile core networks for data traffic delivery. To prevent exceeding the available core network capacity, service providers need to implemen ...
Traffic Engineering in IP over Optical Area Environments
... Figure 2: Evolution path towards data-optimized networks............................................................................... 3 Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Ca ...
... Figure 2: Evolution path towards data-optimized networks............................................................................... 3 Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Ca ...
H.323 Hardware and Software Vulnerabilities
... Both ends need to be configured for H.323 “Phase I: H.323 terminal (A) starts by sending a “Setup message” to another H.323 terminal (B) containing its destination address. Terminal (B) responds by sending a Q.931 “Alerting message” followed by a “Connect message” if the call is accepted. During thi ...
... Both ends need to be configured for H.323 “Phase I: H.323 terminal (A) starts by sending a “Setup message” to another H.323 terminal (B) containing its destination address. Terminal (B) responds by sending a Q.931 “Alerting message” followed by a “Connect message” if the call is accepted. During thi ...
Cisco Platform Exchange Grid (pxGrid) Overview At-A-Glance
... • Share context between multiple systems to decipher relevance of network events – Many IT operations systems provide only basic information associated with a security, performance, or other type of alarm (IP address, for example). This requires operators to look at multiple operational consoles to ...
... • Share context between multiple systems to decipher relevance of network events – Many IT operations systems provide only basic information associated with a security, performance, or other type of alarm (IP address, for example). This requires operators to look at multiple operational consoles to ...
Emergency Communication - dumbo-isif
... Maintaining all routes to reachable destinations (tabledriven routing) Using continues control messages to set up routes ...
... Maintaining all routes to reachable destinations (tabledriven routing) Using continues control messages to set up routes ...
Communication - Princeton University
... Challenges of Intra-AS Mapping • Firewalls at the network edge – Cannot typically map inside another stub AS – … because the probe packets will be blocked by firewall – So, typically used only to study service providers ...
... Challenges of Intra-AS Mapping • Firewalls at the network edge – Cannot typically map inside another stub AS – … because the probe packets will be blocked by firewall – So, typically used only to study service providers ...
Blueprint For Security Chapter 6
... Advantages and Disadvantages of HIDPSs Can detect local events on host systems and detect attacks that may elude a network-based IDPS Functions on host system, where encrypted traffic will have been decrypted and is available for processing Not affected by use of switched network protocols ...
... Advantages and Disadvantages of HIDPSs Can detect local events on host systems and detect attacks that may elude a network-based IDPS Functions on host system, where encrypted traffic will have been decrypted and is available for processing Not affected by use of switched network protocols ...