How Network Address Translation Works
... DRAM could theoretically process 26,214 simultaneous translations, which is more than enough for most applications. IANA has set aside specific ranges of IP addresses for use as non-routable, internal network addresses. These addresses are considered unregistered (for more information check out RFC ...
... DRAM could theoretically process 26,214 simultaneous translations, which is more than enough for most applications. IANA has set aside specific ranges of IP addresses for use as non-routable, internal network addresses. These addresses are considered unregistered (for more information check out RFC ...
the document - Support
... No SMS message received during the authentication process, affecting authentication No SMS message! ...
... No SMS message received during the authentication process, affecting authentication No SMS message! ...
Secure Universal Mobility for Wireless Internet
... A user should be able to roam seamlessly between heterogeneous radio systems, such as public cellular networks (e.g., GPRS, cdma2000, WCDMA networks), public wire-line networks, enterprise (private) wireless local area networks (LANs) and public wireless LAN hotspot networks that may use IEEE 802.11 ...
... A user should be able to roam seamlessly between heterogeneous radio systems, such as public cellular networks (e.g., GPRS, cdma2000, WCDMA networks), public wire-line networks, enterprise (private) wireless local area networks (LANs) and public wireless LAN hotspot networks that may use IEEE 802.11 ...
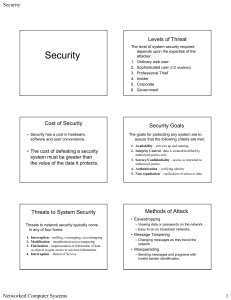
Threats To Windows Users and Countermeasures
... Anyone with File and Print sharing enabled and usi ng share level access are exposed to this threat, a common source of security problem under Windows operating systems. The flaw in an unsecured windows shares can be exploited by intruders in an automated way to place tools on large numbers of Windo ...
... Anyone with File and Print sharing enabled and usi ng share level access are exposed to this threat, a common source of security problem under Windows operating systems. The flaw in an unsecured windows shares can be exploited by intruders in an automated way to place tools on large numbers of Windo ...
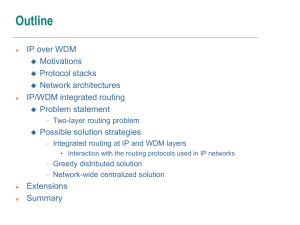
i-2 routing scalability
... 3. Reliability: fast convergence upon topology changes while minimizing communication costs to maintain coherent non-local knowledge about network topology 4. Name-independent routing: accommodate node addresses/labels assigned independently of the topology (otherwise need to split locator and ID pa ...
... 3. Reliability: fast convergence upon topology changes while minimizing communication costs to maintain coherent non-local knowledge about network topology 4. Name-independent routing: accommodate node addresses/labels assigned independently of the topology (otherwise need to split locator and ID pa ...
Network Support for IP Traceback - David Wetherall
... attack. For example, an attack may consist of packets sent from many different slave machines, themselves under the control of a remote master machine. Such indirection may be achieved either explicitly (by compromising the individual slave hosts directly) or implicitly (by sending false requests to ...
... attack. For example, an attack may consist of packets sent from many different slave machines, themselves under the control of a remote master machine. Such indirection may be achieved either explicitly (by compromising the individual slave hosts directly) or implicitly (by sending false requests to ...
Tier-1 ISP - Universidad Carlos III de Madrid
... Networking: A Top Down Approach” generously made available by their authors (see copyright below). The slides have been adapted, where required, to the teaching needs of the subject above. ...
... Networking: A Top Down Approach” generously made available by their authors (see copyright below). The slides have been adapted, where required, to the teaching needs of the subject above. ...
PDF Datasheet – NSA Series
... protection up to date from emerging threats. Dell SonicWALL goes a step beyond traditional solutions with an intrusion prevention system that features sophisticated anti-evasion technology. It scans all network traffic for worms, Trojans, software vulnerabilities, backdoor exploits and other types o ...
... protection up to date from emerging threats. Dell SonicWALL goes a step beyond traditional solutions with an intrusion prevention system that features sophisticated anti-evasion technology. It scans all network traffic for worms, Trojans, software vulnerabilities, backdoor exploits and other types o ...
TeleReach - GURU Control Systems
... anytime access. TeleReach gives you IP access from any PC via Internet Explorer 4.0 or greaterwith no need to install proprietary software onto the remote PC. Network Independent Remote Access When the network is down at 2:00 AM, and youre 30 miles away, remote access through the LAN/WAN just isn ...
... anytime access. TeleReach gives you IP access from any PC via Internet Explorer 4.0 or greaterwith no need to install proprietary software onto the remote PC. Network Independent Remote Access When the network is down at 2:00 AM, and youre 30 miles away, remote access through the LAN/WAN just isn ...
Vulnerability Management: Tools, Challenges and Best Practices
... states there are “many organizations I have counseled [who] lack an effective asset inventory. Without an asset inventory, how are the systems and network engineering groups supposed to sift through security alerts and know which ones apply to them and which can be discarded?” (Gregory, par. 3). Fur ...
... states there are “many organizations I have counseled [who] lack an effective asset inventory. Without an asset inventory, how are the systems and network engineering groups supposed to sift through security alerts and know which ones apply to them and which can be discarded?” (Gregory, par. 3). Fur ...
network
... • A creates datagram with source A, destination B • A uses ARP to get R’s MAC address for 111.111.111.110 • A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram ...
... • A creates datagram with source A, destination B • A uses ARP to get R’s MAC address for 111.111.111.110 • A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram ...
Distance Vector Algorithm Bellman
... carried in OSPF messages directly over IP (rather than TCP or UDP Network Layer 4-29 ...
... carried in OSPF messages directly over IP (rather than TCP or UDP Network Layer 4-29 ...
SCORE: A Scalable Architecture for Implementing Resource
... - More layers of functionality more possible unintended interaction between layers - E.g., corruption drops on wireless interpreted as congestion drops by TCP ...
... - More layers of functionality more possible unintended interaction between layers - E.g., corruption drops on wireless interpreted as congestion drops by TCP ...
Document
... A sink tree does not contain any loops, so each packet will be delivered within a finite and bounded number of hops. Links and routers can go down and come back up during operation, so different routers may have different ideas about the current topology. One of the issue is whether each router has ...
... A sink tree does not contain any loops, so each packet will be delivered within a finite and bounded number of hops. Links and routers can go down and come back up during operation, so different routers may have different ideas about the current topology. One of the issue is whether each router has ...
Decentralized Resource Management for a Distributed
... we focus on the design of a resource management system for RedHi that can exploit the resources of its DCMS network to achieve these performance objectives. Our proposed resource management system is based on a fully decentralized approach to achieve optimal scalability and robustness. In general, t ...
... we focus on the design of a resource management system for RedHi that can exploit the resources of its DCMS network to achieve these performance objectives. Our proposed resource management system is based on a fully decentralized approach to achieve optimal scalability and robustness. In general, t ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... routing protocols that are considered in the analysis are Ad-Hoc On-demand Distance Vector (AODV), DSR (Dynamic Source Routing) and Optimized Link State Routing (OLSR) etc. 2.1 AODV (Ad-hoc on-demand and distance vector): AODV protocol is a mixture of on-demand and distance vector. A node required t ...
... routing protocols that are considered in the analysis are Ad-Hoc On-demand Distance Vector (AODV), DSR (Dynamic Source Routing) and Optimized Link State Routing (OLSR) etc. 2.1 AODV (Ad-hoc on-demand and distance vector): AODV protocol is a mixture of on-demand and distance vector. A node required t ...
Slides on Security
... 1. To establish an encrypted, not necessarily authenticated, communication channel between client and server. 2. To authenticate the server, and establish a secure channel ...
... 1. To establish an encrypted, not necessarily authenticated, communication channel between client and server. 2. To authenticate the server, and establish a secure channel ...
The Influence of Proportional Jitter and Delay on End to... Differentiated Service Network
... RJPS and WTP separately Among some proportional delay schedulers (BPR, MDP, WTP) we believe that WTP is the best scheduler because WTP can estimate delay differentiation very well. Furthermore we choose Concord algorithm described in [5] for adjusting the playout buffer delay at the receiver. This a ...
... RJPS and WTP separately Among some proportional delay schedulers (BPR, MDP, WTP) we believe that WTP is the best scheduler because WTP can estimate delay differentiation very well. Furthermore we choose Concord algorithm described in [5] for adjusting the playout buffer delay at the receiver. This a ...
PDF
... connectivity. However, the subscriber has a small network of PCs and wants to have Internet access for all the devices. The solution is to configure Network Address Translation (NAT) on the Cisco ADSL WIC. NAT is designed for IP address simplification and conservation. It enables private IP internet ...
... connectivity. However, the subscriber has a small network of PCs and wants to have Internet access for all the devices. The solution is to configure Network Address Translation (NAT) on the Cisco ADSL WIC. NAT is designed for IP address simplification and conservation. It enables private IP internet ...
Csci5211: Computer Networks
... • used to get frames from one interface to another physicallyconnected interface (same physical network, i.e., p2p or LAN) • 48 bit MAC address (for most LANs) – fixed for each adaptor, burned in the adapter ROM – MAC address allocation administered by IEEE ...
... • used to get frames from one interface to another physicallyconnected interface (same physical network, i.e., p2p or LAN) • 48 bit MAC address (for most LANs) – fixed for each adaptor, burned in the adapter ROM – MAC address allocation administered by IEEE ...
Wireless and Mobile Network Architectures
... Provides authentication, resource management, least-cost routing, and administration for user identity and service profile. ...
... Provides authentication, resource management, least-cost routing, and administration for user identity and service profile. ...
Understanding Network Performance in Extreme Congestion Scenario
... communications over Internet. Characterized enterprise and residential networks over a wide variety of network scenarios Classifier that accurately predicts when network issues most likely to cause audio quality degradation WiFi relay that significantly improve VoIP qualify for WiFi clients ...
... communications over Internet. Characterized enterprise and residential networks over a wide variety of network scenarios Classifier that accurately predicts when network issues most likely to cause audio quality degradation WiFi relay that significantly improve VoIP qualify for WiFi clients ...
ppt
... Specifies formats of packets sent across the Internet Connectionless protocol Source to destination forwarding of packets (called datagrams) Every host connected to the Internet has a unique address, called IP Address • Address representation is dotted decimal notation, e.g. ...
... Specifies formats of packets sent across the Internet Connectionless protocol Source to destination forwarding of packets (called datagrams) Every host connected to the Internet has a unique address, called IP Address • Address representation is dotted decimal notation, e.g. ...