A Survey of Active Network Research
... At present generally web caches do not cache the stock quotes because of its dynamic nature and even if it caches, the granularity of the object(entire web page) is inappropriate. ...
... At present generally web caches do not cache the stock quotes because of its dynamic nature and even if it caches, the granularity of the object(entire web page) is inappropriate. ...
Are You suprised - Anna University
... and basic requirement of any IT system. In network the speed of transfer of information flowing is always depends upon both Bandwidth of the network and traffic flow across the system. A poorly designed network may be the bottleneck for any organization to achieve the desired level of goals. The net ...
... and basic requirement of any IT system. In network the speed of transfer of information flowing is always depends upon both Bandwidth of the network and traffic flow across the system. A poorly designed network may be the bottleneck for any organization to achieve the desired level of goals. The net ...
Chapter1R
... To make all programs, equipment (ex: printers, scanners, and CD burners), and especially data available to anyone on the network without regard to the physical location of the resource an the user. ...
... To make all programs, equipment (ex: printers, scanners, and CD burners), and especially data available to anyone on the network without regard to the physical location of the resource an the user. ...
The protocol
... Mobile and Wireless Networks: Background What is wireless? Brief history….. •The physical phenomena known as radio waves were first known as ‘Hertzian Waves’. Hertz showed that the electromagnetic phenomena (under study by Tesla) could be used to transfer energy between locations without a physical ...
... Mobile and Wireless Networks: Background What is wireless? Brief history….. •The physical phenomena known as radio waves were first known as ‘Hertzian Waves’. Hertz showed that the electromagnetic phenomena (under study by Tesla) could be used to transfer energy between locations without a physical ...
Marks for each part of each question are
... One solution is to use the Next-Hop Resolution Protocol. This requires a Next Hop server in addition to the AAS. The NHS is informed of mappings on both subnets. Hosts consult the NHS as well as the AAS. If the NHS returns an address on the local ATM network then a diorect VCC is set up. c) The diag ...
... One solution is to use the Next-Hop Resolution Protocol. This requires a Next Hop server in addition to the AAS. The NHS is informed of mappings on both subnets. Hosts consult the NHS as well as the AAS. If the NHS returns an address on the local ATM network then a diorect VCC is set up. c) The diag ...
Network Layer Security
... Internet Security Association and Key Management Protocol Provide framework for key management Define procedures and packet formats to establish, negotiate, modify, and delete SAs Independent of key exchange protocol, encryption algorithm, and authentication ...
... Internet Security Association and Key Management Protocol Provide framework for key management Define procedures and packet formats to establish, negotiate, modify, and delete SAs Independent of key exchange protocol, encryption algorithm, and authentication ...
CS 455: Computer Networks and Data Communication Sample Final Examination Points: 125
... to the internet using a single IP address (203.45.103.67) provided by its ISP. Show how packets sent from a specific WS (10.23.52.201) to another workstation (125.25.43.98) are handled by the NAT. (Use the specific data given. Don’t simply write some generic answer.) ...
... to the internet using a single IP address (203.45.103.67) provided by its ISP. Show how packets sent from a specific WS (10.23.52.201) to another workstation (125.25.43.98) are handled by the NAT. (Use the specific data given. Don’t simply write some generic answer.) ...
lecture1
... savings. For example, it is cheaper to buy a single high-speed printer with advanced features that can be shared by an entire workgroup than it is to buy separate printers for each user in the group. ...
... savings. For example, it is cheaper to buy a single high-speed printer with advanced features that can be shared by an entire workgroup than it is to buy separate printers for each user in the group. ...
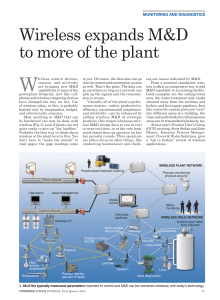
Wireless Expands M D to More of the Plant
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
Chapter 1 - IPFW ETCS
... Sending too much data Protocol attacks: TCP, UDP, ICMP (Internet Control Message Protocol) ...
... Sending too much data Protocol attacks: TCP, UDP, ICMP (Internet Control Message Protocol) ...
Aswin Chidambaram
... various kinds of sophisticated cyber-attacks which can have a serious impact on the Critical Infrastructure such as the power grid. Most of the time, the success of the attack is based on the static characteristics of the system, thereby enabling an easier profiling of the target system(s) by the ad ...
... various kinds of sophisticated cyber-attacks which can have a serious impact on the Critical Infrastructure such as the power grid. Most of the time, the success of the attack is based on the static characteristics of the system, thereby enabling an easier profiling of the target system(s) by the ad ...
ppt
... – By default, ufw starts with a default policy that blocks all inbound traffic and allows outbound traffic ...
... – By default, ufw starts with a default policy that blocks all inbound traffic and allows outbound traffic ...
ppt
... • Wants to appear to rest of corporation as if working internally • From address 10.6.6.6 • Gives access to internal services (e.g., ability to send mail) ...
... • Wants to appear to rest of corporation as if working internally • From address 10.6.6.6 • Gives access to internal services (e.g., ability to send mail) ...
TCP/IP architecture
... Otherwise, send to default router Needs to find the physical address of the next hop router. The router checks its routing table for the next hop and send to it. ...
... Otherwise, send to default router Needs to find the physical address of the next hop router. The router checks its routing table for the next hop and send to it. ...
William Stallings, Cryptography and Network Security 3/e
... until the acknowledgment comes back. – The effect is to accumulate characters into larger chunks and pace them out to the network at a rate matching the round-trip time of the given connection. – This method is usually good for all TCP-based traffic and helps when connectivity to the router is poor ...
... until the acknowledgment comes back. – The effect is to accumulate characters into larger chunks and pace them out to the network at a rate matching the round-trip time of the given connection. – This method is usually good for all TCP-based traffic and helps when connectivity to the router is poor ...
Nefflow based intrusion detection system
... There are several types of anomaly attacks: reconnaissance, exploits and DOS. Reconnaissance attacks include ping sweeps, TCP or UDP port scans, etc. In the exploits attack, the intruders use known or unknown hidden features or bugs to gain access to the system. In the DOS attacks, the intruder atte ...
... There are several types of anomaly attacks: reconnaissance, exploits and DOS. Reconnaissance attacks include ping sweeps, TCP or UDP port scans, etc. In the exploits attack, the intruders use known or unknown hidden features or bugs to gain access to the system. In the DOS attacks, the intruder atte ...
The Internet and World Wide Web
... • Torrent file – a computer file that contains metadata about files and folders to be distributed, and usually also a list of the network locations of trackers • Uses Peer-to-peer connections (P2P) ...
... • Torrent file – a computer file that contains metadata about files and folders to be distributed, and usually also a list of the network locations of trackers • Uses Peer-to-peer connections (P2P) ...
Understanding the Basic of Computer Network
... • Modern switches build a port map of all IP address which respond on each port, and only broadcasts on all ports when it doesn't have a packet's target IP address already in its port map. ...
... • Modern switches build a port map of all IP address which respond on each port, and only broadcasts on all ports when it doesn't have a packet's target IP address already in its port map. ...
Chapter 5 - Department of Computer Science and Information Systems
... Packet-filter firewalls examine all the data flowing back and forth between the trusted network Application layer firewalls filter traffic based on the application they request Proxy severs are firewalls that communicate with the Internet on the private network’s behalf ...
... Packet-filter firewalls examine all the data flowing back and forth between the trusted network Application layer firewalls filter traffic based on the application they request Proxy severs are firewalls that communicate with the Internet on the private network’s behalf ...
CS219: Advanced Topics in Internet Research
... – Ability to switch interfaces on the fly to migrate between failure-prone networks – Ability to provide quality of service: what is QoS in this environment? ...
... – Ability to switch interfaces on the fly to migrate between failure-prone networks – Ability to provide quality of service: what is QoS in this environment? ...
LANs & WANs Requirements and Internet
... Converts analogue phone signals to digital data which the computer can understand. Converts digital data to analogue phone signals so they can be transmitted through the phone line ...
... Converts analogue phone signals to digital data which the computer can understand. Converts digital data to analogue phone signals so they can be transmitted through the phone line ...