Distributed Monitoring of Mesh Networks
... RREQ, RREP, RERR, Hello received packet counters UDP payload and timestamp ...
... RREQ, RREP, RERR, Hello received packet counters UDP payload and timestamp ...
1 – Find the Gateway (Router) Address Open the DOS Command
... Apply. Make sure the preferred DNS server is set to 8.8.8.8. The default ports are as follows; Server Port - 8000, HTTP Port - 85, RTSP Port - 554. If you need to change these to something else you can do so in the More Settings tab. This may be necessary if some other application is already using t ...
... Apply. Make sure the preferred DNS server is set to 8.8.8.8. The default ports are as follows; Server Port - 8000, HTTP Port - 85, RTSP Port - 554. If you need to change these to something else you can do so in the More Settings tab. This may be necessary if some other application is already using t ...
16-Channel monitor w/Interruption
... Enclosure size: 5.5” (14 cm) x 2.5” (6.3 cm) x 1.2” (3 cm), ABS-94 flame retardant Surge protection: Wireless mesh total isolation system, normally open measurement relays and MOV’s 300ft (100 m) line-of-sight range to Watchdog base station ...
... Enclosure size: 5.5” (14 cm) x 2.5” (6.3 cm) x 1.2” (3 cm), ABS-94 flame retardant Surge protection: Wireless mesh total isolation system, normally open measurement relays and MOV’s 300ft (100 m) line-of-sight range to Watchdog base station ...
View File - University of Engineering and Technology, Taxila
... existing protocol or propose a new protocol to thwart such threats. Because the solutions are designed explicitly with certain attack models in mind, they work well in the presence of designated attacks but may collapse under anticipated attacks. Therefore, a more ambitious goal for ad hoc network s ...
... existing protocol or propose a new protocol to thwart such threats. Because the solutions are designed explicitly with certain attack models in mind, they work well in the presence of designated attacks but may collapse under anticipated attacks. Therefore, a more ambitious goal for ad hoc network s ...
ISCW642-825 - GogoTraining
... Cable modems primarily deliver broadband Internet access in the form of cable Internet. Cable modems also utilize unused bandwidth on a cable television network. Cable modem services require access to two protocols: TFTP (Trivial File Transfer Protocol) and DHCP (Dynamic Host Configuration Protocol) ...
... Cable modems primarily deliver broadband Internet access in the form of cable Internet. Cable modems also utilize unused bandwidth on a cable television network. Cable modem services require access to two protocols: TFTP (Trivial File Transfer Protocol) and DHCP (Dynamic Host Configuration Protocol) ...
Commercial Sales
... According to the Gartner Group by 2003 100% of enterprises will supplement their WAN infrastructures with VPNs Evolution VPNs: Originally private voice networks Traditional Model: leased lines to connect routers ...
... According to the Gartner Group by 2003 100% of enterprises will supplement their WAN infrastructures with VPNs Evolution VPNs: Originally private voice networks Traditional Model: leased lines to connect routers ...
IEEE Communications-2017 - Levine Lectronics and Lectric
... • Virtual LAN (VLAN): a network of computers that behave as if they are connected to the same wire even though they may actually be physically located on different segments of a LAN • Quality of service (QoS): Allows prioritization of packets to occur or improve performance for key channels • Rapid ...
... • Virtual LAN (VLAN): a network of computers that behave as if they are connected to the same wire even though they may actually be physically located on different segments of a LAN • Quality of service (QoS): Allows prioritization of packets to occur or improve performance for key channels • Rapid ...
A Secure Intrusion - Detection System for Vulnerable Attacks in
... made it possible in many applications. Among all the contemporary wireless networks, Mobile Ad hoc Network (MANET) is one of the most important and unique applications. On the contrary to traditional network architecture, MANET does not require a fixed network infrastructure; every single node works ...
... made it possible in many applications. Among all the contemporary wireless networks, Mobile Ad hoc Network (MANET) is one of the most important and unique applications. On the contrary to traditional network architecture, MANET does not require a fixed network infrastructure; every single node works ...
planetLab
... • The Scout module manages all TCP and UDP ports and ICMP IDs to ensure that there are no collisions between safe raw sockets and TCP/UDP/ICMP sockets • For each IP address, all ports are either free or "owned" by a slice. • Two slices may split ownership of a port by binding it to different IP addr ...
... • The Scout module manages all TCP and UDP ports and ICMP IDs to ensure that there are no collisions between safe raw sockets and TCP/UDP/ICMP sockets • For each IP address, all ports are either free or "owned" by a slice. • Two slices may split ownership of a port by binding it to different IP addr ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... stations for wireless cellular networks). By multi-hop wireless, we mean that in a MANET, the routes between end users may consist of multiple wireless hops, as compared to the single wireless hop in a wireless local area network (WLAN) or a cellular network, where only the last hop (e.g., from the ...
... stations for wireless cellular networks). By multi-hop wireless, we mean that in a MANET, the routes between end users may consist of multiple wireless hops, as compared to the single wireless hop in a wireless local area network (WLAN) or a cellular network, where only the last hop (e.g., from the ...
View Presentation - InfoSec Nashville
... (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for customer service and filing claims). Note: when there is a dental, vision, or chiropractic pl ...
... (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for customer service and filing claims). Note: when there is a dental, vision, or chiropractic pl ...
ACCEPTABLE USE POLICY
... encryption circumvention devices, or Trojan Horse programs. Unauthorized port scanning is strictly prohibited; Copy, distribute, or sublicense any proprietary software provided in connection with the Service by airHOP or any third party, except that you may make one copy of each software program f ...
... encryption circumvention devices, or Trojan Horse programs. Unauthorized port scanning is strictly prohibited; Copy, distribute, or sublicense any proprietary software provided in connection with the Service by airHOP or any third party, except that you may make one copy of each software program f ...
NP_ch04
... Processors continue to increase in speed Some conventional hardware present in all systems ...
... Processors continue to increase in speed Some conventional hardware present in all systems ...
chapter4d
... IP Addressing IP address: network part (high order bits) host part (low order bits) What’s a network ? (from IP address perspective) device interfaces with same network part of IP address can physically reach each other without intervening router ...
... IP Addressing IP address: network part (high order bits) host part (low order bits) What’s a network ? (from IP address perspective) device interfaces with same network part of IP address can physically reach each other without intervening router ...
Jitendra Bulsara
... routine maintenance of supported systems. Proficient in configuring and using DHCP, DNS and WINS services. Upgraded router and switch IOS via TFTP server Was responsible for setup and maintenance of a help-desk system for the University. Support included documenting and resolving user reported pro ...
... routine maintenance of supported systems. Proficient in configuring and using DHCP, DNS and WINS services. Upgraded router and switch IOS via TFTP server Was responsible for setup and maintenance of a help-desk system for the University. Support included documenting and resolving user reported pro ...
Chapter 5
... 052300 When you’re setting up a wireless network, you see an option asking if you want to broadcast the network SSID. You should: A. Change the default SSID and broadcast it. B. Turn SSID broadcasting off so that hackers don’t know the network’s encryption key. C. Make sure SSID is broadcast ...
... 052300 When you’re setting up a wireless network, you see an option asking if you want to broadcast the network SSID. You should: A. Change the default SSID and broadcast it. B. Turn SSID broadcasting off so that hackers don’t know the network’s encryption key. C. Make sure SSID is broadcast ...
AirLive WL-5460AP Manual
... This device provides four operational applications with Access Point, Bridge, Client (Ad-hoc) and Client (Infrastructure) modes, which are mutually exclusive. This device is shipped with configuration that is functional right out of the box. If you want to change the settings in order to perform mor ...
... This device provides four operational applications with Access Point, Bridge, Client (Ad-hoc) and Client (Infrastructure) modes, which are mutually exclusive. This device is shipped with configuration that is functional right out of the box. If you want to change the settings in order to perform mor ...
Engineer`s Toolset - Sigma Software Distribution
... Query an IP address range to locate used and unused IP addresses; obtain data about each system in the range. ...
... Query an IP address range to locate used and unused IP addresses; obtain data about each system in the range. ...
Focus area #6
... Functionality; ipv6, multicast, official IP-adresses, mobility etc. available only on parts of the campus network. Lack of efficient management tools covering all networking and services areas. Innovation by use of NRENs often stops somewhere in the campus organization. The unreleased potential for ...
... Functionality; ipv6, multicast, official IP-adresses, mobility etc. available only on parts of the campus network. Lack of efficient management tools covering all networking and services areas. Innovation by use of NRENs often stops somewhere in the campus organization. The unreleased potential for ...
Peakflow SP
... Traffic of specific types exceeding what should be normal for a network. Misuse anomalies cover the following types of traffic: ...
... Traffic of specific types exceeding what should be normal for a network. Misuse anomalies cover the following types of traffic: ...
Networks - Burgate ICT
... • Special software is required to run the network. • Microsoft Windows NT Server 4.0 is a multipurpose server operating system. A multipurpose operating system integrates a variety of network services. The services it provides are designed to address customer requirements and are managed in a single ...
... • Special software is required to run the network. • Microsoft Windows NT Server 4.0 is a multipurpose server operating system. A multipurpose operating system integrates a variety of network services. The services it provides are designed to address customer requirements and are managed in a single ...
The Network Layer in the Internet
... Exterior gateway protocol routers have to worry about politics a great deal. Policies are manually configured into each BGP router. They are not a part of the protocol itself. Two BGP routers are considered connected if they share a common network. BGP is fundamentally a distance vector protocol. In ...
... Exterior gateway protocol routers have to worry about politics a great deal. Policies are manually configured into each BGP router. They are not a part of the protocol itself. Two BGP routers are considered connected if they share a common network. BGP is fundamentally a distance vector protocol. In ...
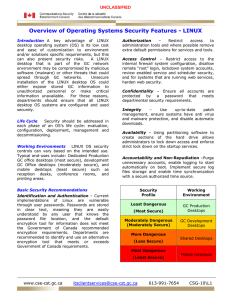
Overview of Operating Systems Security Features
... desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that ...
... desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that ...
IT 141: Information Systems I - Tonga Institute of Higher Education
... Packets contain the actual data, the destination address, and the address of the sender The receiver will wait until all the packets are received and then process the data ...
... Packets contain the actual data, the destination address, and the address of the sender The receiver will wait until all the packets are received and then process the data ...