009_namingaddressing
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...
The Internet - The University of Tennessee at Martin
... Engineering Steering Group (IESG ) are recorded and published as standards track RFCs. As a result, the RFC publication process plays an important role in the Internet standards process. RFCs must first be published as Internet Drafts. ...
... Engineering Steering Group (IESG ) are recorded and published as standards track RFCs. As a result, the RFC publication process plays an important role in the Internet standards process. RFCs must first be published as Internet Drafts. ...
Overview - Computer Science Division
... • Switched communication networks – Information is transmitted to a sub-set of designated nodes • Examples: WANs (Telephony Network, Internet) ...
... • Switched communication networks – Information is transmitted to a sub-set of designated nodes • Examples: WANs (Telephony Network, Internet) ...
PPT - pantherFILE
... – Like the Greek Trojan horse, these programs have a hidden, negative, subversive, and thus potentially harmful aspect. – Trojan horses are programs that masquerade as useful programs, but contain malicious code to attack the system or leak information. An unsuspecting user would typically run a Tro ...
... – Like the Greek Trojan horse, these programs have a hidden, negative, subversive, and thus potentially harmful aspect. – Trojan horses are programs that masquerade as useful programs, but contain malicious code to attack the system or leak information. An unsuspecting user would typically run a Tro ...
Elman Network
... The NN model used Elman network with FletcherReeves Update as the BP network training algorithm and gradient descent with momentum as the weight/bias learning function was designed. Several options for the number of neurons in the hidden layer were tried, in order to arrive at an optimum design Duri ...
... The NN model used Elman network with FletcherReeves Update as the BP network training algorithm and gradient descent with momentum as the weight/bias learning function was designed. Several options for the number of neurons in the hidden layer were tried, in order to arrive at an optimum design Duri ...
ETRI
... Technology standards for wired network need to observes BcN standard model QoS (Quality of Service) and security guarantee Integration with wireless networks (wireless local loop) Broadband convergence of wired networks in order to support future converged multimedia services that integrates v ...
... Technology standards for wired network need to observes BcN standard model QoS (Quality of Service) and security guarantee Integration with wireless networks (wireless local loop) Broadband convergence of wired networks in order to support future converged multimedia services that integrates v ...
Network Management Concepts and Practice
... Transparent bridge divides a LAN into segments that use the same media access control specification and it controls what traffic is passed between segments. uses bridge table to learn which devices are on which segments. Translating bridges connects networks using different MAC layer specificati ...
... Transparent bridge divides a LAN into segments that use the same media access control specification and it controls what traffic is passed between segments. uses bridge table to learn which devices are on which segments. Translating bridges connects networks using different MAC layer specificati ...
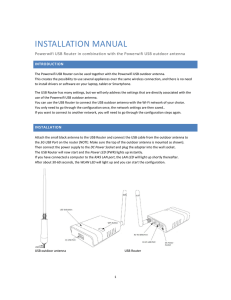
installation manual
... The Powerwifi USB Router can be used together with the Powerwifi USB outdoor antenna. This creates the possibility to use several appliances over the same wireless connection, and there is no need to install drivers or software on your laptop, tablet or Smartphone. The USB Router has many settings, ...
... The Powerwifi USB Router can be used together with the Powerwifi USB outdoor antenna. This creates the possibility to use several appliances over the same wireless connection, and there is no need to install drivers or software on your laptop, tablet or Smartphone. The USB Router has many settings, ...
CMPU1022 Operating Systems 1
... computer systems. A Host is a is a specific computer system in a site that provides services. A Node is the name assigned to the host to identify it to other computers. ...
... computer systems. A Host is a is a specific computer system in a site that provides services. A Node is the name assigned to the host to identify it to other computers. ...
Document
... for teaching security concepts and practices – We designed and implemented an animated simulator for packet sniffer ...
... for teaching security concepts and practices – We designed and implemented an animated simulator for packet sniffer ...
Cetak Test 2 Vetting Compiled 21 April Zahilah Johan Maznah
... “ In order for the user to access the remote account, the user must provide the identification and password. After providing this authorization information, the user can transfer files from the local file system to the remote file system and vice versa (Kurose and James, 2011). …” A) SMTP B) UDP C) ...
... “ In order for the user to access the remote account, the user must provide the identification and password. After providing this authorization information, the user can transfer files from the local file system to the remote file system and vice versa (Kurose and James, 2011). …” A) SMTP B) UDP C) ...
Presentation3
... – Narrow (and multiple) memory buses – Some other ad-hoc solutions for network processing, e.g., ...
... – Narrow (and multiple) memory buses – Some other ad-hoc solutions for network processing, e.g., ...
8.9.2 Lab Configure DHCP in 7
... For Host A, plug one end of the Ethernet patch cable into “Port 1” on the back of the router. For Host A, plug the other end of the Ethernet patch cable into the network port on the NIC in your computer. For Host B, plug one end of the Ethernet patch cable into “Port 2” on the back of the router. Fo ...
... For Host A, plug one end of the Ethernet patch cable into “Port 1” on the back of the router. For Host A, plug the other end of the Ethernet patch cable into the network port on the NIC in your computer. For Host B, plug one end of the Ethernet patch cable into “Port 2” on the back of the router. Fo ...
network
... • Consequently, fragments can waste resources • Not recommended !!! • Hosts encouraged to perform MTU path discovery • Avoid fragments if possible ...
... • Consequently, fragments can waste resources • Not recommended !!! • Hosts encouraged to perform MTU path discovery • Avoid fragments if possible ...
802.21 - TGu Joint Session
... different that impacts our interface (802.11 > 802.21) • Does 802.21 expect 802.11u to provide any service beyond network selection which is already defined? • E.g., does 802.21 expect 802.11u to pre-provision QoS? • From 802.21 perspective there is NO difference in the two cases • IS can be used i ...
... different that impacts our interface (802.11 > 802.21) • Does 802.21 expect 802.11u to provide any service beyond network selection which is already defined? • E.g., does 802.21 expect 802.11u to pre-provision QoS? • From 802.21 perspective there is NO difference in the two cases • IS can be used i ...
Complex Networks
... Static properties (like node out-degree) do not capture operational conditions and network dynamics ...
... Static properties (like node out-degree) do not capture operational conditions and network dynamics ...
Document
... MTU, TCP kernel, Buffer memory, AQM optimized for commodity Internet, etc 2. Packet loss can result from congestion, but also underlying BER – achieve a gigabit per second with TCP on a coast-to-coast path (rtt = 40 msec), with 1500 byte packets, the loss rate can not exceed ...
... MTU, TCP kernel, Buffer memory, AQM optimized for commodity Internet, etc 2. Packet loss can result from congestion, but also underlying BER – achieve a gigabit per second with TCP on a coast-to-coast path (rtt = 40 msec), with 1500 byte packets, the loss rate can not exceed ...
Hands-On Laboratory Experiments in Data Communications and
... mode) simply consists of a set of wireless stations that communicate directly with one another without using an AP. The point of this lab is to configure a wireless connection working in both infrastructure mode and ad hoc mode with 2 computers, and in ad hoc mode with 4 computers. Students will als ...
... mode) simply consists of a set of wireless stations that communicate directly with one another without using an AP. The point of this lab is to configure a wireless connection working in both infrastructure mode and ad hoc mode with 2 computers, and in ad hoc mode with 4 computers. Students will als ...
Set 1 File
... The transport layer is responsible for ensuring that packets are received in the order they were sent and making sure that no data is lost or corrupted. If a packet is lost, the transport layer can ask the sender to retransmit the packet. Transmission Control Protocol (TCP), is a high-overhead proto ...
... The transport layer is responsible for ensuring that packets are received in the order they were sent and making sure that no data is lost or corrupted. If a packet is lost, the transport layer can ask the sender to retransmit the packet. Transmission Control Protocol (TCP), is a high-overhead proto ...
Unit 8 - WordPress.com
... 3. There is no master computer on controller. Every computer has equal chance to place the data and access the token. 4. There are no collisions. 5. Data packets travel at greater speeds. 6. It is easier to locate the problems with device and cable i.e. fault isolation is simplified. If one device d ...
... 3. There is no master computer on controller. Every computer has equal chance to place the data and access the token. 4. There are no collisions. 5. Data packets travel at greater speeds. 6. It is easier to locate the problems with device and cable i.e. fault isolation is simplified. If one device d ...
Implementing IEEE 802.11b/g wireless Local Area Networks
... Two types or modes of WLANs exist; the technology that provides connectivity to the infrastructure network and the technology that provides the connectivity of one device to another or an adhoc network. This is also depicted in Figure 1.1 [3-5]. IEEE 802.11-based WLANs work in both modes. WLANs do n ...
... Two types or modes of WLANs exist; the technology that provides connectivity to the infrastructure network and the technology that provides the connectivity of one device to another or an adhoc network. This is also depicted in Figure 1.1 [3-5]. IEEE 802.11-based WLANs work in both modes. WLANs do n ...