TCP: Software for Reliable Communication
... Different computers use different internal representation (Ex: ASCII, EBDIC) for integers and characters; How to translate from one representation to another Computer Networks Applications ...
... Different computers use different internal representation (Ex: ASCII, EBDIC) for integers and characters; How to translate from one representation to another Computer Networks Applications ...
stributed Computing : Current Theories and Current Practices
... Servers organized into what is known as the domain name system (DNS) provide the name resolution or translation service, based on a distributed database of records of names and IP address mappings. Thousands of DNS servers run continually on the Internet, and form what is probably the largest and mo ...
... Servers organized into what is known as the domain name system (DNS) provide the name resolution or translation service, based on a distributed database of records of names and IP address mappings. Thousands of DNS servers run continually on the Internet, and form what is probably the largest and mo ...
Slide 1
... 76Mb Firewall @ 64Byte packets 96Mb of 3DES IPsec Stateful Inspection Firewall, NAT & QoS >50Mb@64byte packets Stateful Inspection Firewall, NAT, QoS, IPsec VPN (with AES 256 bit encryption) >20Mb@72byte packets ...
... 76Mb Firewall @ 64Byte packets 96Mb of 3DES IPsec Stateful Inspection Firewall, NAT & QoS >50Mb@64byte packets Stateful Inspection Firewall, NAT, QoS, IPsec VPN (with AES 256 bit encryption) >20Mb@72byte packets ...
What Is A Network
... You will learn what is a network, how they work and what are the different types. ...
... You will learn what is a network, how they work and what are the different types. ...
Click Here for Kirk`s BLT-26 HSMM-MESH Introduction
... radio access nodes in a mesh topology • Think about a cell phone network ...
... radio access nodes in a mesh topology • Think about a cell phone network ...
- EdShare
... Coaxial is and previous method of cabling networks. It use to be the popular choice of medium for networking, but in the late 1980s and early 1990s, it was quickly replaced by UTP (unshielded twisted pair). Today it has currently made a comeback because of its use with broadband/ADSL service and the ...
... Coaxial is and previous method of cabling networks. It use to be the popular choice of medium for networking, but in the late 1980s and early 1990s, it was quickly replaced by UTP (unshielded twisted pair). Today it has currently made a comeback because of its use with broadband/ADSL service and the ...
Virtual - Microsoft Center
... • You need bandwidth controls • Physical adapters don’t support it • Limited number of VMs that can use it per host • You lose the capabilities of the vSwitch ...
... • You need bandwidth controls • Physical adapters don’t support it • Limited number of VMs that can use it per host • You lose the capabilities of the vSwitch ...
BDC5eChapter19
... – User(s) may be abusing access privileges and burdening the network at the expense of other users – Users may be making inefficient use of the network – Network manager can plan better for network growth if user activity is known in sufficient detail. ...
... – User(s) may be abusing access privileges and burdening the network at the expense of other users – Users may be making inefficient use of the network – Network manager can plan better for network growth if user activity is known in sufficient detail. ...
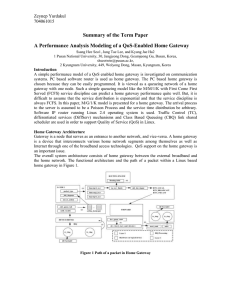
A performance analysis modeling of a QoS
... was dropped. This means that the QoS mechanism was achieved. Since the UDP1 traffic has the lowest priority although the UDP1 traffic has the lowest sending rate. Also, UDP1 and VoIP traffic were dropped at 1.7M. But, the UDP0 traffic was not, because of the drop of VoIP traffic. As greater bandwidt ...
... was dropped. This means that the QoS mechanism was achieved. Since the UDP1 traffic has the lowest priority although the UDP1 traffic has the lowest sending rate. Also, UDP1 and VoIP traffic were dropped at 1.7M. But, the UDP0 traffic was not, because of the drop of VoIP traffic. As greater bandwidt ...
Meiden Review 2013 No.3 (Series No.159)
... deterioration issue with efficiency of the overall system transmission which is caused by a low speed part. However, it is not always better to do faster. As shown in the Fig. 4, packets are discarded when an unbalance between hub input and output is occured. When 1Gbps is changed down to 100Mbps on ...
... deterioration issue with efficiency of the overall system transmission which is caused by a low speed part. However, it is not always better to do faster. As shown in the Fig. 4, packets are discarded when an unbalance between hub input and output is occured. When 1Gbps is changed down to 100Mbps on ...
Introduction - Wapanucka Public Schools
... reasonable available precautions to restrict access by users to inappropriate material. The district network has blocking and filtering software installed which is designed to prevent access to users to visual depictions which are obscene, child pornography, and other materials which may be harmful ...
... reasonable available precautions to restrict access by users to inappropriate material. The district network has blocking and filtering software installed which is designed to prevent access to users to visual depictions which are obscene, child pornography, and other materials which may be harmful ...
Chapter 1 - UniMAP Portal
... networks Host computers prepare IP packets and transmit them over their attached network Routers forward IP packets across networks Best-effort IP transfer service, no retransmission ...
... networks Host computers prepare IP packets and transmit them over their attached network Routers forward IP packets across networks Best-effort IP transfer service, no retransmission ...
Aalborg Universitet Multimedia Cross–Platform Content Distribution for Mobile Peer–to–Peer Networks
... to the decoder represented by the bottom layer in the figure. In Figure 1 the decoder receives k packets, and will with high probability be able to decode the original data as long as g ≤ k. As shown by this example one of the main advantages of network coding over traditional packet routing is that ...
... to the decoder represented by the bottom layer in the figure. In Figure 1 the decoder receives k packets, and will with high probability be able to decode the original data as long as g ≤ k. As shown by this example one of the main advantages of network coding over traditional packet routing is that ...
Chapter 10
... Data Communications and Computer Networks: A Business User's Approach, Fifth Edition ...
... Data Communications and Computer Networks: A Business User's Approach, Fifth Edition ...
Technology in Action Network Topics Networking Advantages Client
... • All nodes are connected in sequence on a single cable • Used most often on peer--topeer to-peer networks • Networked computers communicate with each other • One computer transmits data at a time ...
... • All nodes are connected in sequence on a single cable • Used most often on peer--topeer to-peer networks • Networked computers communicate with each other • One computer transmits data at a time ...
Access Security Requirements
... 5.1 Protect Internet connections with dedicated, industry-recognized Firewalls that are configured and managed using industry best security practices. 5.2 Internal private Internet Protocol (IP) addresses must not be publicly accessible or natively routed to the Internet. Network address translation ...
... 5.1 Protect Internet connections with dedicated, industry-recognized Firewalls that are configured and managed using industry best security practices. 5.2 Internal private Internet Protocol (IP) addresses must not be publicly accessible or natively routed to the Internet. Network address translation ...
A network operating system (NOS) is a computer
... in Comparison of Centralized (Client-Server) and Decentralized (Peer-to-Peer) Networking. [edit]Advantages ...
... in Comparison of Centralized (Client-Server) and Decentralized (Peer-to-Peer) Networking. [edit]Advantages ...
Network Automation Solutions
... These load break switches are used in all types of overhead distribution networks in rural and suburban areas. Devices are available as manually or remotely controlled versions. They are designed to be easily integrated in remotely controlled SCADA systems. Modular design of the load break switches ...
... These load break switches are used in all types of overhead distribution networks in rural and suburban areas. Devices are available as manually or remotely controlled versions. They are designed to be easily integrated in remotely controlled SCADA systems. Modular design of the load break switches ...
Lecture 1 Introduction to the Computers
... • Tables of DNs & IP addresses are distributed throughout the Internet on numerous servers • There is a DNS server at most ISPs. It converts the domain names in our Internet requests to actual IP addresses • In case it does not have a particular domain name in its table, it makes a request to anothe ...
... • Tables of DNs & IP addresses are distributed throughout the Internet on numerous servers • There is a DNS server at most ISPs. It converts the domain names in our Internet requests to actual IP addresses • In case it does not have a particular domain name in its table, it makes a request to anothe ...
1 In addition to assigning addresses from predefined pools, which
... dhcp relay-agent dhcp-relay 16 What is the default lease time for addresses assigned to clients through Easy IP? twenty-four hours forty-eight hours one week two weeks ...
... dhcp relay-agent dhcp-relay 16 What is the default lease time for addresses assigned to clients through Easy IP? twenty-four hours forty-eight hours one week two weeks ...
Assets, Threats and Vulnerabilities: Discovery and
... inside safe from access by non-authorized users from the outside. Encryption on the other hand was simply intended to prevent unauthorized users from being able to read vital information even if they did get access to it. The major shortcoming with point solutions, such as firewalls and encryption, ...
... inside safe from access by non-authorized users from the outside. Encryption on the other hand was simply intended to prevent unauthorized users from being able to read vital information even if they did get access to it. The major shortcoming with point solutions, such as firewalls and encryption, ...
009_namingaddressing
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...