appendix 8 eazy networking
... Note: EaZy Networking is not a free service. We will initially provide 2GB data allowance (approx. 2185 minutes) for free. When 2GB is up, the network transmission will be down to 1 FPS. To restore the fluency of live view, users need to subscribe a data plan from EagleEyes, or configure the network ...
... Note: EaZy Networking is not a free service. We will initially provide 2GB data allowance (approx. 2185 minutes) for free. When 2GB is up, the network transmission will be down to 1 FPS. To restore the fluency of live view, users need to subscribe a data plan from EagleEyes, or configure the network ...
Networking
... software programs which run on networking devices such as servers, bridges, and routers to monitor and report the status of those devices. forward this network management information to enterprise network management system which compile and report network operation statistics to the end-user, most o ...
... software programs which run on networking devices such as servers, bridges, and routers to monitor and report the status of those devices. forward this network management information to enterprise network management system which compile and report network operation statistics to the end-user, most o ...
NETWORKING AND DATA COMMUNICATION
... LAN is the smallest size of network & it normally covers an area within the radius of 10M – 3 Km. LAN is usually owned by one organization. However, one LAN can be connected to other LANs over any distance via data transmission lines or wireless media. A LAN connects several Personal Computers to a ...
... LAN is the smallest size of network & it normally covers an area within the radius of 10M – 3 Km. LAN is usually owned by one organization. However, one LAN can be connected to other LANs over any distance via data transmission lines or wireless media. A LAN connects several Personal Computers to a ...
Document
... Use a default router if nothing matches Not necessary for all 1s in subnet mask to be ...
... Use a default router if nothing matches Not necessary for all 1s in subnet mask to be ...
Chapter 4: Advanced Internetworking
... Tree like structure: there is a single backbone and autonomous systems are connected only as parents and children and not as peers ...
... Tree like structure: there is a single backbone and autonomous systems are connected only as parents and children and not as peers ...
Chapter 4 - Elsevier
... Tree like structure: there is a single backbone and autonomous systems are connected only as parents and children and not as peers ...
... Tree like structure: there is a single backbone and autonomous systems are connected only as parents and children and not as peers ...
chap12
... Data collected every Data combined time you fill out with information form or click from public advertisement on sources Web Merchants Merchants sell sell the Marketing firms contents of their sell your databases to electronic profile national marketing Next to any company firms and Internet p.12.27 ...
... Data collected every Data combined time you fill out with information form or click from public advertisement on sources Web Merchants Merchants sell sell the Marketing firms contents of their sell your databases to electronic profile national marketing Next to any company firms and Internet p.12.27 ...
Computer Networks(Routing and IPv6).
... RARP, BOOTP, and DHCP • When a computer is booted how does it get the IP address. • RARP – Broadcast a packet to ask RARP server. – Packet cannot be forwarded by routers, so RARP server is needed on each network. ...
... RARP, BOOTP, and DHCP • When a computer is booted how does it get the IP address. • RARP – Broadcast a packet to ask RARP server. – Packet cannot be forwarded by routers, so RARP server is needed on each network. ...
1 - Cisco Support Community
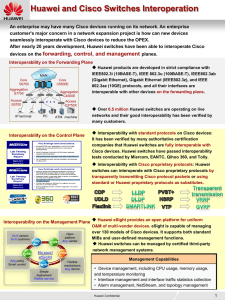
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
Chapter-6 Presentation
... Lower the administrative distance the more trustworthy the information. If the router hears about a route to the same network from more than one source it will use the administrative distance to decide which route to put in the routing table. ...
... Lower the administrative distance the more trustworthy the information. If the router hears about a route to the same network from more than one source it will use the administrative distance to decide which route to put in the routing table. ...
GSM/UMTS Network
... Separation of call control and connectivity/bearer control Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway ...
... Separation of call control and connectivity/bearer control Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway ...
Computer Networks - Network Optiminization Research Group
... RARP, BOOTP, and DHCP • When a computer is booted how does it get the IP address. • RARP – Broadcast a packet to ask RARP server. – Packet cannot be forwarded by routers, so RARP server is needed on each network. ...
... RARP, BOOTP, and DHCP • When a computer is booted how does it get the IP address. • RARP – Broadcast a packet to ask RARP server. – Packet cannot be forwarded by routers, so RARP server is needed on each network. ...
Slide 1
... Automatic Repeat Request (ARQ) – Based on the retransmission of packets that have been detected to be in error. Packets carry a checksum which is used by the receiver to detect errors. Requires a feedback channel. With FEC one pays an a priori battery power consumption overhead and packet delay by ...
... Automatic Repeat Request (ARQ) – Based on the retransmission of packets that have been detected to be in error. Packets carry a checksum which is used by the receiver to detect errors. Requires a feedback channel. With FEC one pays an a priori battery power consumption overhead and packet delay by ...
Capacity Scaling with Multiple Radios and Multiple Channels in
... as much as possible. In narrowband systems such as FDMA, the extent of spatial reuse is directly proportional to the number of orthogonal channels available. Currently, only a very limited number of such orthogonal channels are available: 3 in 802.11b in the 2.4 GHz band and between 9 and 12 in 802. ...
... as much as possible. In narrowband systems such as FDMA, the extent of spatial reuse is directly proportional to the number of orthogonal channels available. Currently, only a very limited number of such orthogonal channels are available: 3 in 802.11b in the 2.4 GHz band and between 9 and 12 in 802. ...
Identity Management and Resource Allocation in the Network
... What is Network Virtualization? (Revisited) Network virtualization is a networking environment that allows multiple service providers to dynamically compose multiple heterogeneous virtual networks that coexist together in isolation from each other, and to deploy customized end-toend services on-the ...
... What is Network Virtualization? (Revisited) Network virtualization is a networking environment that allows multiple service providers to dynamically compose multiple heterogeneous virtual networks that coexist together in isolation from each other, and to deploy customized end-toend services on-the ...
Internet2 Presentation Template
... How do you define deterministic behavior? How close to end nodes should optical waves be switched? Where is the new edge? How dynamic must optically switched paths be? What duration do we expect of dynamic paths? What is the interaction between the packet infrastructure and the dynamically created p ...
... How do you define deterministic behavior? How close to end nodes should optical waves be switched? Where is the new edge? How dynamic must optically switched paths be? What duration do we expect of dynamic paths? What is the interaction between the packet infrastructure and the dynamically created p ...
LoRaWAN - LoRa Alliance
... The protocol and network architecture have the most influence in determining the battery lifetime of a node, the network capacity, the quality of service, the security, and the variety of applications served by the network. ...
... The protocol and network architecture have the most influence in determining the battery lifetime of a node, the network capacity, the quality of service, the security, and the variety of applications served by the network. ...
Institutionen för systemteknik
... to networks-on-chip and components used in network components and terminals. This research has among others resulted in the SoCBUS NOC and a flow based network protocol processor. The main objective of this project was to integrate these components into an IP router with two or more Gigabit Ethernet ...
... to networks-on-chip and components used in network components and terminals. This research has among others resulted in the SoCBUS NOC and a flow based network protocol processor. The main objective of this project was to integrate these components into an IP router with two or more Gigabit Ethernet ...
Document
... bye stream originating on one machine to be delivered without error on any other machine in the internet. TCP also handles flow control. ...
... bye stream originating on one machine to be delivered without error on any other machine in the internet. TCP also handles flow control. ...
3rd Edition: Chapter 4
... Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
... Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
Chapter 7
... • In Novell NetWare LAN implementations, the services advertising protocol (SAP) is implemented at the OSI application layer. Inherent in this protocol is the presence of a server table in each server and router. • When the server is initiated, one of its startup functions is to broadcast a SAP mess ...
... • In Novell NetWare LAN implementations, the services advertising protocol (SAP) is implemented at the OSI application layer. Inherent in this protocol is the presence of a server table in each server and router. • When the server is initiated, one of its startup functions is to broadcast a SAP mess ...
Senstar Integration
... The integration between DVTEL’s Latitude NVMS and Senstar Network Manager allows for Senstar alarms to trigger multiple actions within Latitude NVMS including, but not limited to, pre and post recording, associated video camera pop ups, alarm incident creation as well as the ability to use other adv ...
... The integration between DVTEL’s Latitude NVMS and Senstar Network Manager allows for Senstar alarms to trigger multiple actions within Latitude NVMS including, but not limited to, pre and post recording, associated video camera pop ups, alarm incident creation as well as the ability to use other adv ...