sigcomm`11 - Cornell Computer Science
... disconnectivity and security vulnerabilities. However, diagnosing problems in networks remains a black art. Operators often rely on heuristics — sending probes, reviewing logs, even observing mailing lists and making phone calls — that slow response to failures.1 To address this, automated tools for ...
... disconnectivity and security vulnerabilities. However, diagnosing problems in networks remains a black art. Operators often rely on heuristics — sending probes, reviewing logs, even observing mailing lists and making phone calls — that slow response to failures.1 To address this, automated tools for ...
Security Audit Proposal
... network switches and any other network devices. This will exclude devices such as printers. The process of network audit requires that technical details are collected. These details will be entered into our data collection document. This part of the process would take the most time to complete, as s ...
... network switches and any other network devices. This will exclude devices such as printers. The process of network audit requires that technical details are collected. These details will be entered into our data collection document. This part of the process would take the most time to complete, as s ...
INE1020 Lecture Notes
... taken on message transmission and receipt. Addressing: defines where to deliver the messages. INE1020: Introduction to Internet Engineering ...
... taken on message transmission and receipt. Addressing: defines where to deliver the messages. INE1020: Introduction to Internet Engineering ...
lecture10 - Academic Server| Cleveland State University
... – Compile a list of networks, or hosts, that are not reachable – Then use the converse of that map to determine where things probably are ...
... – Compile a list of networks, or hosts, that are not reachable – Then use the converse of that map to determine where things probably are ...
Module 10 - Home - KSU Faculty Member websites
... • Routing protocols allow routers to choose the best path for data from source to destination • Routers use routing protocols to exchange routing tables and share routing information • Routing protocols enable routers to route routed protocols • Examples of routing protocols include: – Routing Infor ...
... • Routing protocols allow routers to choose the best path for data from source to destination • Routers use routing protocols to exchange routing tables and share routing information • Routing protocols enable routers to route routed protocols • Examples of routing protocols include: – Routing Infor ...
ch01 - kuroski.net
... Use of switch satisfies need for fast communication Resource sharing using peer-to-peer network Internet access easily added ...
... Use of switch satisfies need for fast communication Resource sharing using peer-to-peer network Internet access easily added ...
FREE Sample Here
... directory means that the owner of the directory, members of a group, and everyone else (Other) have read, write, and execute permissions for that directory. Because each category has three unique permissions, and each permission can be expressed as true or false (on or off), three bits are used. You ...
... directory means that the owner of the directory, members of a group, and everyone else (Other) have read, write, and execute permissions for that directory. Because each category has three unique permissions, and each permission can be expressed as true or false (on or off), three bits are used. You ...
IPSec
... • In order to communicate, each pair of hosts must set up SA with each other • Acts as virtual connection for which various parameters are set: ...
... • In order to communicate, each pair of hosts must set up SA with each other • Acts as virtual connection for which various parameters are set: ...
Network+ Guide to Networks 5th Edition
... segments received into smaller packets ensures that packets are not larger than the network’s maximum transmission unit size • This is usually avoided by adjusting the Maximum Segment Size in the Transport layer, because it makes data transfer inefficient • Router : device that connects network seg ...
... segments received into smaller packets ensures that packets are not larger than the network’s maximum transmission unit size • This is usually avoided by adjusting the Maximum Segment Size in the Transport layer, because it makes data transfer inefficient • Router : device that connects network seg ...
MultiRack Setup Instruction
... Remote Control Tab The Remote Control tab sets the connection between MultiRack and a console. This enables an integrated workflow in which the console controls MultiRack remotely. Here you see the consoles that the network has discovered. You can then set up a connection with one of them. Once conn ...
... Remote Control Tab The Remote Control tab sets the connection between MultiRack and a console. This enables an integrated workflow in which the console controls MultiRack remotely. Here you see the consoles that the network has discovered. You can then set up a connection with one of them. Once conn ...
Mobilink Software User Guide - cdma-mobi.com.ua
... SMS Messaging charges and character limit are network operator dependent. Contact your network operator for details. ...
... SMS Messaging charges and character limit are network operator dependent. Contact your network operator for details. ...
TCP/IP - Austin Community College
... – Such as Network Address Translation (NAT), firewall protection, and quality of service (QoS) ...
... – Such as Network Address Translation (NAT), firewall protection, and quality of service (QoS) ...
Chapter 3: Wireless Access Point Web Management
... The TPL-310AP 200Mbps Powerline AV Wireless N Access Point is an excellent solution that can be used to extend your network using your home or small office electrical wiring. In a home or small office building, use TPL-310AP adapters to link multiple locations without the need to run long Ethernet c ...
... The TPL-310AP 200Mbps Powerline AV Wireless N Access Point is an excellent solution that can be used to extend your network using your home or small office electrical wiring. In a home or small office building, use TPL-310AP adapters to link multiple locations without the need to run long Ethernet c ...
Routing
... packet may encounter several relay points and a variety of data link types beyond the LANs. ...
... packet may encounter several relay points and a variety of data link types beyond the LANs. ...
SO WHAT IS VOIP - Xtranet internet service provider
... samples per second, with the tolerance on that rate 50 parts per million (ppm). Non-uniform quantization (logarithmic) with 8 bits is used to represent each sample, resulting in a 64 kbit/s bit rate. There are two slightly different versions; μ-law, which is used primarily in North America, and A-la ...
... samples per second, with the tolerance on that rate 50 parts per million (ppm). Non-uniform quantization (logarithmic) with 8 bits is used to represent each sample, resulting in a 64 kbit/s bit rate. There are two slightly different versions; μ-law, which is used primarily in North America, and A-la ...
OSI Model
... segmenting long data streams into smaller data chunks (based on allowed “packet” size for a given transmission medium) ...
... segmenting long data streams into smaller data chunks (based on allowed “packet” size for a given transmission medium) ...
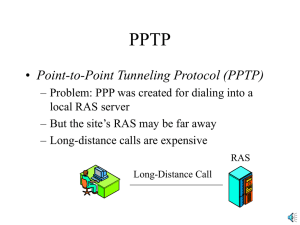
PPTP
... – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
... – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
Chapter 11 Interior Routing Protocols
... [Get Next Node] Find neighboring node not in T with least-cost path from s Incorporate node into T Also incorporate edge incident on that node and node in T that contributes to the path. This can be expressed as: ...
... [Get Next Node] Find neighboring node not in T with least-cost path from s Incorporate node into T Also incorporate edge incident on that node and node in T that contributes to the path. This can be expressed as: ...
AFOSR_review_Jul10 - Northwestern University
... Network Level Defense • Network gateways/routers are the vantage points for detecting large scale attacks • Only host based detection/prevention is not enough – Some users do not apply the host-based schemes due to the reliability, overhead, and conflicts – Many users do not update or patch their s ...
... Network Level Defense • Network gateways/routers are the vantage points for detecting large scale attacks • Only host based detection/prevention is not enough – Some users do not apply the host-based schemes due to the reliability, overhead, and conflicts – Many users do not update or patch their s ...
Chapter 14: Distributed Operating Systems
... Clusters – a collection of semi-autonomous machines that acts as ...
... Clusters – a collection of semi-autonomous machines that acts as ...