IE Looks at 192.168.50.10 : 8080
... directory service, and many other Microsoft applications, servers, and services. ...
... directory service, and many other Microsoft applications, servers, and services. ...
Presentation
... interfaces to common functions - configuration storage, identity management, user status e.g. presence, location held by Home Subscriber Server (HSS); billing services by a Charging Gateway Function (CGF), control of voice/video calls, messaging Control: Routes signaling, enables transport plane t ...
... interfaces to common functions - configuration storage, identity management, user status e.g. presence, location held by Home Subscriber Server (HSS); billing services by a Charging Gateway Function (CGF), control of voice/video calls, messaging Control: Routes signaling, enables transport plane t ...
TREND Big Picture on Energy-Efficient Backbone Networks Esther Le Rouzic, Raluca-Maria Indre
... amount of power is used by the facilities for power supply and distribution, and by the cooling infrastructure. However, the physical efficiency is not enough to guarantee the overall efficiency of the data center that has to be also related to the computational efficiency that, in its turn, depends ...
... amount of power is used by the facilities for power supply and distribution, and by the cooling infrastructure. However, the physical efficiency is not enough to guarantee the overall efficiency of the data center that has to be also related to the computational efficiency that, in its turn, depends ...
Lect03
... • TCP breaks this data into segments, each of which fits into an IP datagram. • Original stream is numbered by bytes. • Segment contains sequence number of data bytes. TCP/IP: Basics ...
... • TCP breaks this data into segments, each of which fits into an IP datagram. • Original stream is numbered by bytes. • Segment contains sequence number of data bytes. TCP/IP: Basics ...
A Review on Intrusion Detection System to Protect Cloud Data
... performance cost on the monitored systems. 2. Network-Based Intrusion Detection System Network-based Intrusion Detection Systems stress on the network rather than a specific host. Network-based IDS detects attacks by capturing and analyzing network packets. By listening on a network segment, a netwo ...
... performance cost on the monitored systems. 2. Network-Based Intrusion Detection System Network-based Intrusion Detection Systems stress on the network rather than a specific host. Network-based IDS detects attacks by capturing and analyzing network packets. By listening on a network segment, a netwo ...
Network Types and Topologies
... – Local Area Network (LAN): covers a small local area such as a home, office, or other building – Wireless LAN: covers a limited geographic area and is popular in places where cables are difficult to install – Metropolitan Area Network (MAN): covers a large campus or city – Wide Area Network (WAN): ...
... – Local Area Network (LAN): covers a small local area such as a home, office, or other building – Wireless LAN: covers a limited geographic area and is popular in places where cables are difficult to install – Metropolitan Area Network (MAN): covers a large campus or city – Wide Area Network (WAN): ...
WAPs (Wireless Access Point)
... A switch is a small hardware device that joins multiple computers together within one local area network (LAN). A switch is a telecommunication device that receives a message from any device connected to it and then transmits the message only to the device for which the message was meant ( It don’t ...
... A switch is a small hardware device that joins multiple computers together within one local area network (LAN). A switch is a telecommunication device that receives a message from any device connected to it and then transmits the message only to the device for which the message was meant ( It don’t ...
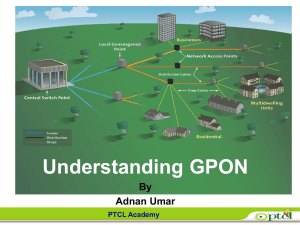
GPON 1
... APON (ATM Passive Optical Network). First Passive optical network standard. Used primarily for business applications was based on ATM (Asynchronous Transfer Mode) Initial offering 155.52 Mbps Downstream, 155.52 Mbps upstream. ...
... APON (ATM Passive Optical Network). First Passive optical network standard. Used primarily for business applications was based on ATM (Asynchronous Transfer Mode) Initial offering 155.52 Mbps Downstream, 155.52 Mbps upstream. ...
MediaPlayer™ versus RealPlayer - Computer Science
... Large application frames sent over UDP can result in IP fragmentation. Figure 1 shows the network layer packet arrival pattern for one high encoding rate pair (a 250 Kbps MediaPlayer clip and a 217 Kbps RealPlayer clip). The MediaPlayer packets have a very regular pattern, with groups of packets and ...
... Large application frames sent over UDP can result in IP fragmentation. Figure 1 shows the network layer packet arrival pattern for one high encoding rate pair (a 250 Kbps MediaPlayer clip and a 217 Kbps RealPlayer clip). The MediaPlayer packets have a very regular pattern, with groups of packets and ...
571Lecture7
... • In a circuit switch, path of a sample is determined at time of connection establishment. No need for header. • In a packet switch, packets carry a destination field or label. Need to look up destination port on-the-fly. – Datagram switches: lookup based on destination address – Label switches: loo ...
... • In a circuit switch, path of a sample is determined at time of connection establishment. No need for header. • In a packet switch, packets carry a destination field or label. Need to look up destination port on-the-fly. – Datagram switches: lookup based on destination address – Label switches: loo ...
Media: Voice and Video in your SIP Environment
... – A large frame is fragmented into a series of packets for transmission over network – I-Frame fragmentation • Receiver must receive all fragments to properly reconstruct frame ...
... – A large frame is fragmented into a series of packets for transmission over network – I-Frame fragmentation • Receiver must receive all fragments to properly reconstruct frame ...
SAINT: Secure and Active Internetworking
... To date: Analytical model of sender-initiated collision-avoidance protocols in ad hoc networks with omni antennas; collision-free MAC protocols based on 2-hop neighborhood; basic hybrid routing using link-state information. 6 months: Extensions of analytical model for collision-avoidance to address ...
... To date: Analytical model of sender-initiated collision-avoidance protocols in ad hoc networks with omni antennas; collision-free MAC protocols based on 2-hop neighborhood; basic hybrid routing using link-state information. 6 months: Extensions of analytical model for collision-avoidance to address ...
Bruk Assefa Yirdaw Tuning a Campus Network
... departments in a single building or a set of buildings. The word campus network derives from networks built on university campuses. Nowadays, the term is used more commonly to embrace networks that cover businesses or campuses, consisting of buildings, portions of a building, or a collection of coll ...
... departments in a single building or a set of buildings. The word campus network derives from networks built on university campuses. Nowadays, the term is used more commonly to embrace networks that cover businesses or campuses, consisting of buildings, portions of a building, or a collection of coll ...
T01
... • Trailer: Frame Check Sequence (FCS) - This field is four bytes long. It contains a 32 bit Cyclic Redundancy Check (CRC). ...
... • Trailer: Frame Check Sequence (FCS) - This field is four bytes long. It contains a 32 bit Cyclic Redundancy Check (CRC). ...
Intrusion Detection
... Mac OS MacTCP, 7.6.1 OpenTransport 1.1.2 and 8.0 NetApp NFS server 4.1d and 4.3 NetBSD 1.1 to 1.3 (Fixed after required updates) NeXTSTEP 3.0 and 3.1 ...
... Mac OS MacTCP, 7.6.1 OpenTransport 1.1.2 and 8.0 NetApp NFS server 4.1d and 4.3 NetBSD 1.1 to 1.3 (Fixed after required updates) NeXTSTEP 3.0 and 3.1 ...
NCB521W User Manual
... 1) On “Local PC Information” Area, if you PC have more than 1 network Adapter, please chooses the one which you are using now. 2) If you have the firewall software in your PC, when run the B1Search_en.exe, it may pop up a window to say “whether you want to block this program or not”, then you should ...
... 1) On “Local PC Information” Area, if you PC have more than 1 network Adapter, please chooses the one which you are using now. 2) If you have the firewall software in your PC, when run the B1Search_en.exe, it may pop up a window to say “whether you want to block this program or not”, then you should ...
投影片1
... In February, then-FCC Chairman Michael Powell gives a speech called “Preserving Internet Freedom: Guiding Principles for the Industry,” outlining the idea of four Internet Freedoms in response to calls for some type of network neutrality. ...
... In February, then-FCC Chairman Michael Powell gives a speech called “Preserving Internet Freedom: Guiding Principles for the Industry,” outlining the idea of four Internet Freedoms in response to calls for some type of network neutrality. ...
Network
... cable. Ex: RJ-45 connectors (twisted pair cable) Network interface cards: PC expansion board. Allows computer to be connected to a network. Each NIC has a unique identifier Modem: Enable transmission over telephone lines. Digital signal converted to analog ...
... cable. Ex: RJ-45 connectors (twisted pair cable) Network interface cards: PC expansion board. Allows computer to be connected to a network. Each NIC has a unique identifier Modem: Enable transmission over telephone lines. Digital signal converted to analog ...
Y-Comm: A new architecture for heterogeneous networking
... available channels provided you know the amount of time a channel will be available. – That time is known as: • Time before vertical handover (TBVH) • Can significantly reduce packet loss during all vertical handovers ...
... available channels provided you know the amount of time a channel will be available. – That time is known as: • Time before vertical handover (TBVH) • Can significantly reduce packet loss during all vertical handovers ...