* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Identity Management and Resource Allocation in the Network
Distributed firewall wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
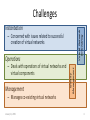
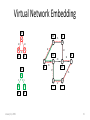
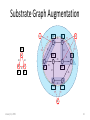
Identity Management and Resource Allocation in the Network Virtualization Environment Mosharaf Chowdhury School of Computer Science University of Waterloo January 21, 2009 1 NETWORK VIRTUALIZATION January 21, 2009 2 Why Network Virtualization? • Internet is almost ossified – Lots of band-aids and makeshift solutions (e.g., overlays) – A new architecture (aka clean-slate) is needed • Hard to come up with a one-size-fits-all architecture – Almost impossible to predict what future might unleash • Why not create an all-sizes-fit-into-one architecture instead! – Open and expandable – Coexistence of heterogeneous architectures January 21, 2009 3 What is Network Virtualization? • Transparent abstraction of networking platform and resources – Multiple logical interpretations of the physical characteristics • Multiple virtual networks (VNs) • Additional level of indirection – Indirect access to network resources • Resource partitioning and isolation – Physical and logical – Dynamic provisioning and configuration January 21, 2009 4 Network Virtualization Environment January 21, 2009 5 Challenges Virtual Network Embedding Instantiation – Concerned with issues related to successful creation of virtual networks – Deals with operations of virtual networks and virtual components Management – Manages co-existing virtual networks January 21, 2009 Identity Management Operations 6 Identity Management in the Network Virtualization Environment IMARK January 21, 2009 7 Motivation • High level of dynamism – Macro Level: Merge/Separate VNs – Micro Level: Add/Join/Migration of end hosts and virtual routers • Mobility – Geographical – Logical • Überhoming – Simultaneously connect to multiple InPs and VNs January 21, 2009 8 Design Principles 1. Separation of Identity and Location – Inherent support for mobility and Überhoming 2. Local Autonomy – Flexibility of naming and addressing in different VNs – Defined interfaces and mechanisms for cooperation 3. Global Identifier Space – Local identifiers have no end-to-end significance January 21, 2009 9 iMark Overview • Concepts 1. Identifier Spaces 2. Mappings • Components 1. Controllers 2. Adapters January 21, 2009 10 Operations: Macro Level • Federation – Multiple VNs create common administrative domain – Controller network • Hierarchy – Aggregation of mappings in representative controllers – Balanced and unbalanced January 21, 2009 11 Operations: Micro Level • Join – Add mappings • Lookup and Connection Setup – State setup in the network • Leave – Remove mappings • Mobility – Soft handoff January 21, 2009 12 Evaluation Mean Mapping Size Per Controller January 21, 2009 Mean Lookups Resolved 13 Intra-domain Resource Allocation through Virtual Network Embedding VINEYARD January 21, 2009 14 Virtual Network Embedding 10 80 a 10 12 b c 10 10 A 55 B 22 12 90 10 C 60 20 15 D 20 15 E January 21, 2009 5 d f 20 20 F 85 17 25 e 5 50 10 G 70 17 H 65 15 Substrate Graph Augmentation a ∞ 80 55 15 A ∞ 10 a 10 b 10 10 B 22 C c 60 10 ∞ ∞ 12 90 12 c ∞ D 15 50 10 20 E F 85 17 25 G H 17 70 65 ∞ ∞ b January 21, 2009 16 D-ViNE and R-ViNE For each VN request: – Augment the substrate graph – Solve the resulting LP – For each virtual node: • Calculate the probability for each meta-node to be selected for the corresponding virtual node • Selection: INITIALIZATION NODE MAPPING – D-ViNE: Select the meta-node with the highest probability – R-ViNE: Select a meta-node randomly with the calculated probability – Use MCF to map virtual edges LINK MAPPING – If the VN request is accepted FINALIZATION • January 21, 2009 Update residual capacities of the substrate resources 17 Acceptance Ratio January 21, 2009 18 Revenue Vs Cost Revenue January 21, 2009 Cost 19 Resource Utilization Node Utilization January 21, 2009 Link Utilization 20 What have we done? What will we do? SUMMARY January 21, 2009 21 Contributions • Survey of Network Virtualization (Submitted + TechReport) – Historical perspective – Categorization of existing projects – Enumeration of open problems • Identity Management Framework (IM’09) – Interoperability with flexibility to support mobility and Überhoming • Virtual Network Embedding Algorithms (INFOCOM’09) – Better embedding quality – Mathematical foundation January 21, 2009 22 Future Work • iMark Prototype Development – Further evaluation • Theoretical Analysis of D-ViNE and R-ViNE – Approximation factors – Economic models • Inter-domain VN embedding January 21, 2009 23 Collaborators • Fida-E Zaheer (iMark) • Muntasir Raihan Rahman (ViNEYard) • Network Virtualization Project Members January 21, 2009 24 Questions? Mosharaf Chowdhury http:// www.mosharaf.com/ January 21, 2009 25 BACKUP SLIDES January 21, 2009 26 Related Concepts 1. 2. 3. 4. Virtual Local Area Networks (VLAN) Virtual Private Networks (VPN) Active and Programmable Networks Overlay Networks January 21, 2009 27 Downsides of Overlay Networks • Largely used as narrow fixes for specific problems – No holistic view • Most overlays are designed in the application layer – Cannot support radically different concepts Anderson et al. January 21, 2009 28 What is a Virtual Network (VN)? • A collection of virtual nodes and virtual links forming a virtual topology – Subset of physical topology – Basic entity of the NVE • A virtual node is hosted on a particular physical node – Multiple virtual nodes can coexist • A virtual link spans over a physical path – Includes a portion of the underlying physical resources January 21, 2009 29 Business Model Players • Infrastructure Providers (InP) – • End User Create and manage virtual networks Deploy customized end-to-end services End Users – • Manage underlying physical networks Service Providers (SP) – – • Relationships Buy and use services from different service providers Brokers – Mediators/Arbiters January 21, 2009 SLA Broker EIA Service Provider NPA SIA Infrastructure Provider IIA 30 Hierarchy of Roles January 21, 2009 31 Basic Concepts Principles Design Goals • • • • • • • • • • • • • Concurrence Recursion Inheritance Revisitation January 21, 2009 Flexibility Manageability Scalability Isolation Stability and Convergence Programmability Heterogeneity Experimental and Deployment Facility Legacy Support 32 What is Network Virtualization? (Revisited) Network virtualization is a networking environment that allows multiple service providers to dynamically compose multiple heterogeneous virtual networks that coexist together in isolation from each other, and to deploy customized end-toend services on-the-fly as well as manage them on those virtual networks for the end-users by effectively sharing and utilizing underlying network resources leased from multiple infrastructure providers. January 21, 2009 33 Classification • Networking technology – Targeted technology for virtualization • Layer of virtualization – Particular layer in the network stack where virtualization is introduced • Architectural domain – Specific problem domain that virtualization addresses • Level of virtualization – Granularity at which virtualization is realized January 21, 2009 34 Existing Projects Project Architectural Domain Networking Technology VNRMS Virtual network management ATM/IP Tempest Enabling alternate control architectures ATM Link NetScript Dynamic composition of services IP Network Node Genesis Spawning virtual network architectures Network Node/Link January 21, 2009 Layer of Virtualization Level of Virtualization Node/Link 35 Existing Projects (Cont.) Project Architectural Domain VNET Virtual machine Grid computing VIOLIN Deploying on-demand value-added services on IP overlays X-Bone Layer of Virtualization Level of Virtualization Link Node IP Application Node Automating deployment of IP overlays IP Application Node/Link PlanetLab Deploy and manage overlay-based testbeds IP Application Node UCLP Dynamic provisioning and reconfiguration of lightpaths SONET Physical Link January 21, 2009 Networking Technology 36 Existing Projects (Cont.) Project Architectural Domain Networking Technology Layer of Virtualization AGAVE End-to-end QoS-aware service provisioning IP Network GENI Creating customized virtual network testbeds Heterogeneous VINI Evaluating protocols and services in a realistic environment CABO Deploying value-added end-to-end services on shared infrastructure January 21, 2009 Level of Virtualization Link Heterogeneous Full 37 Major Ongoing Projects Project Originated In Link 4WARD Europe http://www.4ward-project.eu/ AKARI Japan http://akari-project.nict.go.jp/ CABO USA http://www.cs.princeton.edu/~jrex/virtual.html Clean Slate USA http://cleanslate.stanford.edu/ GENI USA http://www.geni.net/ NouVeau Canada http://netlab.cs.uwaterloo.ca/virtual/ PlanetLab USA http://www.planet-lab.org/ Trilogy Europe http://www.trilogy-project.org/ UCLP Canada http://www.uclp.ca/ VINI USA http://www.vini-veritas.net/ January 21, 2009 38 Entities and Identifier Spaces Entities 1. Service Provider 2. Virtual Network 3. Virtual Resource 4. Infrastructure Provider / Physical Network 5. Physical Resource 6. End User January 21, 2009 Identifier Spaces 1. IDS_ISP 2. IDS_VN 3. IDS_VR 4. IDS_PR 5. IDS_EH 39 Relationships between Entities January 21, 2009 40 Mappings between Different Identifiers January 21, 2009 41 Sequence Diagram: Join January 21, 2009 42 Sequence Diagram: Lookup January 21, 2009 43 January 21, 2009 44 January 21, 2009 45 D-ViNE January 21, 2009 46 R-ViNE January 21, 2009 47 Summary of Compared Algorithms January 21, 2009 48 January 21, 2009 49 January 21, 2009 50 January 21, 2009 51