MLGW help Bang & Olufsen Masterlink Gateway Table of contents
... When DHCP is activated, the settings shown are the actual settings from the DHCP negotiation, so you can first use DHCP to find out the subnet, gateway and DNS server, and then go back to a fixed IP address on that subnet. Fixed IP configuration is preferable to DHCP whenever a controller needs to ...
... When DHCP is activated, the settings shown are the actual settings from the DHCP negotiation, so you can first use DHCP to find out the subnet, gateway and DNS server, and then go back to a fixed IP address on that subnet. Fixed IP configuration is preferable to DHCP whenever a controller needs to ...
Slides - TERENA Networking Conference 2008
... • Enable physicists, astronomers and researchers around the world to share their resources, their data and their knowledge • Provide the best possible network connectivity • High quality, Tailor-Made, Affordable • Different stakeholders working together to provide a quality service • That reaches th ...
... • Enable physicists, astronomers and researchers around the world to share their resources, their data and their knowledge • Provide the best possible network connectivity • High quality, Tailor-Made, Affordable • Different stakeholders working together to provide a quality service • That reaches th ...
show crypto ipsec transform-set
... Click the Create/Select an Access-List for IPSec Traffic radio button ...
... Click the Create/Select an Access-List for IPSec Traffic radio button ...
SurveyRoutingADHOC - start [kondor.etf.rs]
... adds inverse route (towards src) to its routing table: – Stores, together with other relevant information, the address of the neighbour (n1) that sent RREQ to it; – If that host later receives relevant RREP, it will automatically know that reply should be transferred to the neighbour (n1); – In that ...
... adds inverse route (towards src) to its routing table: – Stores, together with other relevant information, the address of the neighbour (n1) that sent RREQ to it; – If that host later receives relevant RREP, it will automatically know that reply should be transferred to the neighbour (n1); – In that ...
The Network Layer - London South Bank University
... packet thru only one of its ports as defined in the routing table. The router may discard the packet if it cannot find the destination address c) Questions: In dynamic routing, how does the router decides to which network should it pass the packet next? What routing algorithm is the routing based on ...
... packet thru only one of its ports as defined in the routing table. The router may discard the packet if it cannot find the destination address c) Questions: In dynamic routing, how does the router decides to which network should it pass the packet next? What routing algorithm is the routing based on ...
ppt - Applied Crypto Group at Stanford University
... A vulnerability related to the display of file names ... Hackers could … misrepresent the name of a file ... and trick a user into downloading an unsafe file. A vulnerability that would allow a Web page to improperly invoke an application installed on a user's system to open a file on a Web site. … ...
... A vulnerability related to the display of file names ... Hackers could … misrepresent the name of a file ... and trick a user into downloading an unsafe file. A vulnerability that would allow a Web page to improperly invoke an application installed on a user's system to open a file on a Web site. … ...
TDC 563-98-301/302, Spring 2002 2-14 TDC 563-98
... but like an outline). From this, the router can then ask for information it does not have. Describes the contents of the topological database. •Link-state Request: Requests pieces of the topological database from neighbor routers. These messages are exchanged after a router discovers (by examining d ...
... but like an outline). From this, the router can then ask for information it does not have. Describes the contents of the topological database. •Link-state Request: Requests pieces of the topological database from neighbor routers. These messages are exchanged after a router discovers (by examining d ...
TCP w/o Congestion Control
... • TCP w/o congestion control and without SACK is inefficient • p=0.1%, SACKEXP = 91% of goodput of lossless link, TCP SACK = 65% (at identical efficiencies of 91%) • As losses increase to 20%, SACKEXP = goodputs ~ 700% at similar efficiencies compared to TCP SACK • Plan: investigate performance of S ...
... • TCP w/o congestion control and without SACK is inefficient • p=0.1%, SACKEXP = 91% of goodput of lossless link, TCP SACK = 65% (at identical efficiencies of 91%) • As losses increase to 20%, SACKEXP = goodputs ~ 700% at similar efficiencies compared to TCP SACK • Plan: investigate performance of S ...
Delivery
... node in the group can receive any of the messages intended for that group Anycast (rarely) is useful in situations such as sending a message to a router, which typically has ...
... node in the group can receive any of the messages intended for that group Anycast (rarely) is useful in situations such as sending a message to a router, which typically has ...
SoC_CIGRE2014_140821
... Multiport Ethernet Switch with 1588 Transparent Clock, managed (VLAN, manual access to MAC table) Combinable with HSR/PRP Switch ...
... Multiport Ethernet Switch with 1588 Transparent Clock, managed (VLAN, manual access to MAC table) Combinable with HSR/PRP Switch ...
FlexPort 80 ® 80 GHz High-Capacity Wireless Carrier Backhaul Links
... capacity while migrating technologies from circuit-based SDH/ SONET networks to packet-based IP networks. BridgeWave’s FlexPort80 provides simultaneous native SDH/SONET and native Ethernet connectivity in a single, all-outdoor solution with user transmission rates up to 1200 Mbps. With FlexPort80, n ...
... capacity while migrating technologies from circuit-based SDH/ SONET networks to packet-based IP networks. BridgeWave’s FlexPort80 provides simultaneous native SDH/SONET and native Ethernet connectivity in a single, all-outdoor solution with user transmission rates up to 1200 Mbps. With FlexPort80, n ...
HPSpaper - University of California, Irvine
... The Ethernet buffer is an eight Kbyte memory split into a receive buffer and a transmit buffer where the data received and the data to be transmitted are stored. The size and location of the receive buffer is determined by the host controller by programming the ERXST, Ethernet Receive Buffer Start, ...
... The Ethernet buffer is an eight Kbyte memory split into a receive buffer and a transmit buffer where the data received and the data to be transmitted are stored. The size and location of the receive buffer is determined by the host controller by programming the ERXST, Ethernet Receive Buffer Start, ...
PDF
... Support for dynamic IP address allocation for the DMVPN spoke's GRE tunnel interface was introduced in Release 15.1(3)T. The spoke devices in DMVPN deployments must be configured statically for local DHCP pools so that they can distribute addresses to hosts on their inside LAN interface. This involv ...
... Support for dynamic IP address allocation for the DMVPN spoke's GRE tunnel interface was introduced in Release 15.1(3)T. The spoke devices in DMVPN deployments must be configured statically for local DHCP pools so that they can distribute addresses to hosts on their inside LAN interface. This involv ...
The Role of People in Security
... allows the system to run safely and securely. • Once the process has been completed, any similar systems can be configured with the same baseline to achieve the same level of security and protection. • Uniform baselines are critical in large-scale operations. ...
... allows the system to run safely and securely. • Once the process has been completed, any similar systems can be configured with the same baseline to achieve the same level of security and protection. • Uniform baselines are critical in large-scale operations. ...
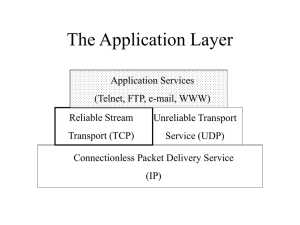
Networking Overview
... datagrams in avian carriers. This specification is primarily useful in Metropolitan Area Networks. This is an experimental, not recommended standard. … Overview and Rational Avian carriers can provide high delay, low throughput, and low altitude service. The connection topology is limited to a singl ...
... datagrams in avian carriers. This specification is primarily useful in Metropolitan Area Networks. This is an experimental, not recommended standard. … Overview and Rational Avian carriers can provide high delay, low throughput, and low altitude service. The connection topology is limited to a singl ...
document
... – Host-to-network (short), htons, convert a short int from network byte order to host byte order – Host-to-network (long), htonl, convert a long int from network byte order to host byte order ...
... – Host-to-network (short), htons, convert a short int from network byte order to host byte order – Host-to-network (long), htonl, convert a long int from network byte order to host byte order ...
Globally-Synchronized Frames for Guaranteed Quality-of-Service in On-Chip Networks Krste Asanovi´c
... lines appropriately [14]. Both schemes manage cache space but not access bandwidth. Virtual Private Caches (VPC) manage both shared cache bandwidth and storage [23]. The QoS-capable shared resources discussed in this section are important building blocks for guaranteed QoS systems, but QoS support f ...
... lines appropriately [14]. Both schemes manage cache space but not access bandwidth. Virtual Private Caches (VPC) manage both shared cache bandwidth and storage [23]. The QoS-capable shared resources discussed in this section are important building blocks for guaranteed QoS systems, but QoS support f ...
Analysis And Research Of System Security Based
... • Android runtime consists of two components. • First, a set of core libraries. • Second, the Virtual machine Dalvik. • Java programs are received and translated by the VM Dalvik. • Applications will be encapsulated in Dalvik. • A VM is available for each and every program even if some programs are ...
... • Android runtime consists of two components. • First, a set of core libraries. • Second, the Virtual machine Dalvik. • Java programs are received and translated by the VM Dalvik. • Applications will be encapsulated in Dalvik. • A VM is available for each and every program even if some programs are ...
Sele in In ctive C nforma Cachin ation C ng with Centric h Hop c
... providerr sends a Dataa packet. The ooffset must be lless than the CtC. Too satisfy this condition, wee can simply sset Offset ...
... providerr sends a Dataa packet. The ooffset must be lless than the CtC. Too satisfy this condition, wee can simply sset Offset ...
The Use of Technology in Providing Proactive Customer Support
... Using the Internet as an alternative Look at a Case Study to see how a WAN, Oracle Application Server, Oracle Database Server and PL/SQL could be used effectively to provide Proactive Support to Customers with the help of a sample application at the end by Eashwar Iyer ([email protected]) ...
... Using the Internet as an alternative Look at a Case Study to see how a WAN, Oracle Application Server, Oracle Database Server and PL/SQL could be used effectively to provide Proactive Support to Customers with the help of a sample application at the end by Eashwar Iyer ([email protected]) ...
A Security Model for VoIP Steganography
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
SonicWALL Tele3SP - Simply Better IT
... Simply Better It is an IT consultancy operating out of the proprietor’s home in New Mills. For its own use and to test out configurations prior to installations, it has its own Local Area Network with a connection to the Internet via a Demon Internet Broadband connection provided by BT Broadband ove ...
... Simply Better It is an IT consultancy operating out of the proprietor’s home in New Mills. For its own use and to test out configurations prior to installations, it has its own Local Area Network with a connection to the Internet via a Demon Internet Broadband connection provided by BT Broadband ove ...
A Security Model for VoIP Steganography
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
Aalborg Universitet Time Calculus
... bounds on delay, and queue utilization of a system. In RTC every service element is modelled individually, where a service element can be in an abstract form, e.g. a whole switch, or more specific, e.g. a specific input port. The inputs and outputs of service elements, are then connected to model th ...
... bounds on delay, and queue utilization of a system. In RTC every service element is modelled individually, where a service element can be in an abstract form, e.g. a whole switch, or more specific, e.g. a specific input port. The inputs and outputs of service elements, are then connected to model th ...


![SurveyRoutingADHOC - start [kondor.etf.rs]](http://s1.studyres.com/store/data/002358361_1-1eb8409683010799a87544900454d765-300x300.png)