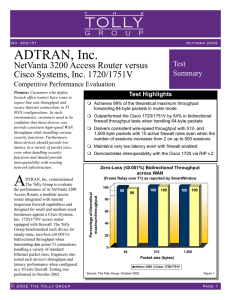
Reed - Virtual Local Area Networks in Security
... The use of VLANS on a network can also be used to reduce the amount of routers used on the network which will reduce the load on the routers and increase the performance of the routers and the network itself. VLANs also give the network administrator the ability to form virtual workgroups for depart ...
... The use of VLANS on a network can also be used to reduce the amount of routers used on the network which will reduce the load on the routers and increase the performance of the routers and the network itself. VLANs also give the network administrator the ability to form virtual workgroups for depart ...
Week 7
... HiperLAN/2 (European standard, 54 Mbps in 5 GHz band) To provide security, most systems use either Wired Equivalent Privacy (WEP), which provides either 40- or 128bit key protection, or a more advanced standard such as WPA (more on security in Chapter Thirteen). Wireless LANs may also be configured ...
... HiperLAN/2 (European standard, 54 Mbps in 5 GHz band) To provide security, most systems use either Wired Equivalent Privacy (WEP), which provides either 40- or 128bit key protection, or a more advanced standard such as WPA (more on security in Chapter Thirteen). Wireless LANs may also be configured ...
Control Panel Security
... In the past, stand-alone control systems provided “security through obscurity” without requiring the Internet. With the rapid growth of industrial Ethernet and EtherNet/IP, remote access into control systems has become essential to enable more productivity for companies. The drive to connect factory ...
... In the past, stand-alone control systems provided “security through obscurity” without requiring the Internet. With the rapid growth of industrial Ethernet and EtherNet/IP, remote access into control systems has become essential to enable more productivity for companies. The drive to connect factory ...
CS335 Networking & Network Administration
... Most hosts use static routing Host’s routing table contains two entries One for the network to which the host attaches A default entry that directs all other traffic to a specific router ...
... Most hosts use static routing Host’s routing table contains two entries One for the network to which the host attaches A default entry that directs all other traffic to a specific router ...
Virtual Private Network (VPN)
... Between networks and firewalls or encrypting routers to do the encrypting and decrypting of the traffic. Have a firewall, encrypting router, or VPN server at the destination end and special VPN client software on the desktop or laptop computers. ...
... Between networks and firewalls or encrypting routers to do the encrypting and decrypting of the traffic. Have a firewall, encrypting router, or VPN server at the destination end and special VPN client software on the desktop or laptop computers. ...
Agenda
... IP core routers with optical interfaces will be interconnected to DWDM equipment via a transponder device. Transponders perform the function of translating a standard optical signal (normally at 1330 nm) from a router line card to one of several wavelengths on a pre-specified grid of wavelengths (s ...
... IP core routers with optical interfaces will be interconnected to DWDM equipment via a transponder device. Transponders perform the function of translating a standard optical signal (normally at 1330 nm) from a router line card to one of several wavelengths on a pre-specified grid of wavelengths (s ...
Multi-Protocol Label Switch (MPLS)
... purposes, such as to guarantee a certain level of performance, to route around network congestion, or to create IP tunnels for network-based virtual private networks. In many ways, LSPs are no different than circuit-switched paths in ATM or Frame Relay networks, except that they are not dependent on ...
... purposes, such as to guarantee a certain level of performance, to route around network congestion, or to create IP tunnels for network-based virtual private networks. In many ways, LSPs are no different than circuit-switched paths in ATM or Frame Relay networks, except that they are not dependent on ...
Dynamics and Effective Topology Underlying
... sustained for several hundred milliseconds. Figure 4b also shows that the initial decline of activity from the peak of an NS to baseline is dominated by cellular-level processes: much of the force that restores the level of activity after the peak of an NS is insensitive to bicuculline, suggestive o ...
... sustained for several hundred milliseconds. Figure 4b also shows that the initial decline of activity from the peak of an NS to baseline is dominated by cellular-level processes: much of the force that restores the level of activity after the peak of an NS is insensitive to bicuculline, suggestive o ...
KM3218251830
... Each node in manet behave like host as well as router. Each nodes forward packet to other nodes. Research in this area is mostly simulation based Random waypoint is commonly used mobility model in this simulations. Random waypoint is simple model that may be applicable to some scenarios. In these ne ...
... Each node in manet behave like host as well as router. Each nodes forward packet to other nodes. Research in this area is mostly simulation based Random waypoint is commonly used mobility model in this simulations. Random waypoint is simple model that may be applicable to some scenarios. In these ne ...
Document
... messages, known as advertisements, to multiple routers. Each device advertises at least one address at which it can receive Simple Network Management Protocol (SNMP) messages. The advertisements also contain “time-to-live” or holdtime information, indicating the length of time that receiving devices ...
... messages, known as advertisements, to multiple routers. Each device advertises at least one address at which it can receive Simple Network Management Protocol (SNMP) messages. The advertisements also contain “time-to-live” or holdtime information, indicating the length of time that receiving devices ...
Transport Layer and Resource Allocation
... no-frills extension of “best-effort” IP What does UDP provide in addition to IP? • process-to-process deliver ...
... no-frills extension of “best-effort” IP What does UDP provide in addition to IP? • process-to-process deliver ...
lecture1 - Academic Csuohio
... Class Participation • You are also encouraged to send me comments/suggestions on how you would like me to improve my teaching so that it is more conducive • For each piece of advice/suggestion, it will be counted as 2 questions • If you max out the class participation credit, you will get extra cred ...
... Class Participation • You are also encouraged to send me comments/suggestions on how you would like me to improve my teaching so that it is more conducive • For each piece of advice/suggestion, it will be counted as 2 questions • If you max out the class participation credit, you will get extra cred ...
Flexible I/O for the Dynamic Data Center
... Mellanox adapters are part of a full 10/25/40/56/100 Gigabit Ethernet end-to-end portfolio for data centers, which includes switches, application acceleration packages, and cables. Mellanox’s SwitchX family of Ethernet switches and Unified Fabric Management software incorporate advanced tools that s ...
... Mellanox adapters are part of a full 10/25/40/56/100 Gigabit Ethernet end-to-end portfolio for data centers, which includes switches, application acceleration packages, and cables. Mellanox’s SwitchX family of Ethernet switches and Unified Fabric Management software incorporate advanced tools that s ...
paper
... process is performed over a field F2q , where 2q is the field size. Hence, traffic as a binary sequence is decomposed into symbol sequence with each symbol of the same length q. A packet 1 consists of N symbols and packets encoded with the same set of coding coefficients are referred to as in the sa ...
... process is performed over a field F2q , where 2q is the field size. Hence, traffic as a binary sequence is decomposed into symbol sequence with each symbol of the same length q. A packet 1 consists of N symbols and packets encoded with the same set of coding coefficients are referred to as in the sa ...
Diameter and LTE Evolved Packet System
... access-control protocols including RADIUS (Remote Authentication Dial in User Service) and TACACS (Terminal Access Controller Access-Control System) that were, and continue to be, widely deployed. RADIUS has enjoyed significant deployment in most dial-up and initial broadband internet service provid ...
... access-control protocols including RADIUS (Remote Authentication Dial in User Service) and TACACS (Terminal Access Controller Access-Control System) that were, and continue to be, widely deployed. RADIUS has enjoyed significant deployment in most dial-up and initial broadband internet service provid ...
Routing & Addressing
... – a modem connection – a console terminal – a network TFTP server • which allows you to maintain and store configuration information at a central site ...
... – a modem connection – a console terminal – a network TFTP server • which allows you to maintain and store configuration information at a central site ...
PowerPoint slides
... If wireless link remains unavailable for extended duration, a window worth of data may be lost driving through a tunnel passing a truck Timeout results in slow start Slow start reduces congestion window to 1 MSS, ...
... If wireless link remains unavailable for extended duration, a window worth of data may be lost driving through a tunnel passing a truck Timeout results in slow start Slow start reduces congestion window to 1 MSS, ...
(IP) routers
... • IP state migration is achieved by control packet sniffing of OSPF using traffic duplication function of transport layer, and BGP peer masquerade using the external SDN controller • For future work, therefore, we will apply our method to an unpredictable failure restoration scenario in which faster ...
... • IP state migration is achieved by control packet sniffing of OSPF using traffic duplication function of transport layer, and BGP peer masquerade using the external SDN controller • For future work, therefore, we will apply our method to an unpredictable failure restoration scenario in which faster ...
The Spread Wide Area Group Communication System
... The cost of using a two level daemon-client model is that interference between different client applications using the same daemon configuration is possible, as discussed in [RG98]. This is minimized by the ability to run multiple daemon configurations each serving separate applications, and by our ...
... The cost of using a two level daemon-client model is that interference between different client applications using the same daemon configuration is possible, as discussed in [RG98]. This is minimized by the ability to run multiple daemon configurations each serving separate applications, and by our ...
Balancing Systematic and Flexible Exploration of Social Networks
... based on its value. This helps illustrate each node’s position among all ranked entities. The network visualization also paints each node with this color. Figure 1 illustrates SocialAction’s technique on a subgraph from the global terrorism network. This network is two-mode, which mean it has two di ...
... based on its value. This helps illustrate each node’s position among all ranked entities. The network visualization also paints each node with this color. Figure 1 illustrates SocialAction’s technique on a subgraph from the global terrorism network. This network is two-mode, which mean it has two di ...
OpenFlow Switching: Data Plane Performance
... We present the main results of the experiments run in our lab to compare the performance of OpenFlow to the ones achievable by standard L-2 and L-3 forwarding. We mainly focus on achieved throughput as the main comparison metric, although we discuss packet latency in some scenarios. A. Single-flow P ...
... We present the main results of the experiments run in our lab to compare the performance of OpenFlow to the ones achievable by standard L-2 and L-3 forwarding. We mainly focus on achieved throughput as the main comparison metric, although we discuss packet latency in some scenarios. A. Single-flow P ...