CS 291 Special Topics on Network Security
... Architecture (Layer); Algorithm; Protocol Why it is built this way? Is it good/the best to build it this way? What if I build it? Network Usage, Management, Analysis How to use the networking service? Application Development Existing Network Applications/Tools ...
... Architecture (Layer); Algorithm; Protocol Why it is built this way? Is it good/the best to build it this way? What if I build it? Network Usage, Management, Analysis How to use the networking service? Application Development Existing Network Applications/Tools ...
Broadband Infrastructure in the ASEAN ‐ 9 Region
... •A tender is issued to select one or more network operators responsible for the construction, operation, maintenance, and commercialization of the pan‐Asian terrestrial fiber optic network. •The contract recipient is paid to manage the cable and assume these responsibilities, including the sales of ...
... •A tender is issued to select one or more network operators responsible for the construction, operation, maintenance, and commercialization of the pan‐Asian terrestrial fiber optic network. •The contract recipient is paid to manage the cable and assume these responsibilities, including the sales of ...
Network Security Platform 8.2.7.71-8.2.3.84 Manager-Mxx30
... 1062428 An Ignore Rule created in the Threat Analyzer using an IPv4 address, creates a rule for an IPv6 endpoint, with an IPv4 address. 1062423 The Automatically Generated Rreports is displayed in improper format. 1062364 In the Threat Explorer page, McAfee ePO tagging success message for default ta ...
... 1062428 An Ignore Rule created in the Threat Analyzer using an IPv4 address, creates a rule for an IPv6 endpoint, with an IPv4 address. 1062423 The Automatically Generated Rreports is displayed in improper format. 1062364 In the Threat Explorer page, McAfee ePO tagging success message for default ta ...
Remote Access—Attack Vectors
... longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be sufficient to breach a system. Organizations with internal networks that store highly sensitive data increase their risk of exposure when they use VPNs to communicate. Hackers are drawn to the vuln ...
... longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be sufficient to breach a system. Organizations with internal networks that store highly sensitive data increase their risk of exposure when they use VPNs to communicate. Hackers are drawn to the vuln ...
Virtual Services Platform 4000 Series
... can be avoided, and time-to-service is vastly enhanced. The beauty of the underlying technology is that it masks devices, links, and protocols and delivers what is logically an extended Ethernet LAN that provides connectivity for multiple end-points. That’s the simple concept, and it is achieved in ...
... can be avoided, and time-to-service is vastly enhanced. The beauty of the underlying technology is that it masks devices, links, and protocols and delivers what is logically an extended Ethernet LAN that provides connectivity for multiple end-points. That’s the simple concept, and it is achieved in ...
MA-100 Media Adaptor
... This EMS SFP provides the management interface back to the NetComplete EMS. Since the management interface both reads and writes information to it, the EMS SFP must always be a JMEP. Typically, the JMEP EMS SFP is installed in the default network port, and this network port is designated as the EMS ...
... This EMS SFP provides the management interface back to the NetComplete EMS. Since the management interface both reads and writes information to it, the EMS SFP must always be a JMEP. Typically, the JMEP EMS SFP is installed in the default network port, and this network port is designated as the EMS ...
No Slide Title
... Standardisation activities for open service access Parlay. Parlay is an object-oriented API, developed by the homonymous industry forum, that provides independent software developers access to a selected range of network capabilities, abstracted by the socalled Service Capability Features (SCFs). ...
... Standardisation activities for open service access Parlay. Parlay is an object-oriented API, developed by the homonymous industry forum, that provides independent software developers access to a selected range of network capabilities, abstracted by the socalled Service Capability Features (SCFs). ...
Smart Gird Energy Training Coalition
... - Limited bandwidth: thus suboptimal with orthogonal (over time or freq.) information and energy transmissions in general - Co-channel interference present due to wireless broadcast nature ...
... - Limited bandwidth: thus suboptimal with orthogonal (over time or freq.) information and energy transmissions in general - Co-channel interference present due to wireless broadcast nature ...
Mobile Networks - ISSA-Sacramento
... receiver in the network (at a known position) also receives these signals. • The mobile device location is calculated by comparing the time differences of arrival of the signals from the base stations at both the mobile device and the special receiver. • This technology is deployed at cell sites and ...
... receiver in the network (at a known position) also receives these signals. • The mobile device location is calculated by comparing the time differences of arrival of the signals from the base stations at both the mobile device and the special receiver. • This technology is deployed at cell sites and ...
ACKs
... when packet dropped, any “upstream transmission capacity used for that packet was wasted! 3: Transport Layer 3b-22 ...
... when packet dropped, any “upstream transmission capacity used for that packet was wasted! 3: Transport Layer 3b-22 ...
NFV PM thought experiments
... But when the flow consists of information that has been previously cached then packets with non-zero information are output although no packets were input At a flow level this seems to show information creation by the server in paradoxical contradiction to principles of information theory So, even m ...
... But when the flow consists of information that has been previously cached then packets with non-zero information are output although no packets were input At a flow level this seems to show information creation by the server in paradoxical contradiction to principles of information theory So, even m ...
Performance Analysis of RIP, EIGRP, and OSPF using
... 2.1 Routing Information Protocol (RIP) RIP is a distance vector dynamic routing protocol that employs the hop count as a routing metric. RIP is implemented on top of the User Datagram Protocol (UDP) as its transport protocol. It is assigned the reserved port number 520. RIP prevents routing loops by ...
... 2.1 Routing Information Protocol (RIP) RIP is a distance vector dynamic routing protocol that employs the hop count as a routing metric. RIP is implemented on top of the User Datagram Protocol (UDP) as its transport protocol. It is assigned the reserved port number 520. RIP prevents routing loops by ...
Denial of Service Attacks in Cognitive Radio Networks and Counter
... communities is max at partition size of 256 ...
... communities is max at partition size of 256 ...
Internet Technology and Security
... IP Does Not: Guarantee delivery - if things go bad - the data can vanish Best effort to keep track of the good and bad paths for traffic - tries to pick better paths when ...
... IP Does Not: Guarantee delivery - if things go bad - the data can vanish Best effort to keep track of the good and bad paths for traffic - tries to pick better paths when ...
The Network Layer
... b) It will take considerable amount of time before every system in the Internet can move from IPv4 to IPv6 c) The transition should be a smooth process to prevent any problems due to their differences. d) 3 transition strategies: • Dual stack • Tunnelling • Header translation ...
... b) It will take considerable amount of time before every system in the Internet can move from IPv4 to IPv6 c) The transition should be a smooth process to prevent any problems due to their differences. d) 3 transition strategies: • Dual stack • Tunnelling • Header translation ...
Challenges in Mining Social Network Data
... Node 32 can find himself: only node of degree 6 connected to both leaders. Node 4 can find herself: only node of degree 5 connected to defecting leader but not original leader. Jon Kleinberg ...
... Node 32 can find himself: only node of degree 6 connected to both leaders. Node 4 can find herself: only node of degree 5 connected to defecting leader but not original leader. Jon Kleinberg ...
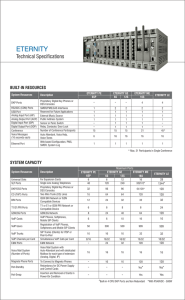
Product Datasheet
... TCP/IP on Ethernet connectivity for connection to local and remote management stations (MM8000 or MK8000). Transport protocol CMSDL/IP or CEI 79-5 featuring 64bit encryption (FEAL algorithm) for high security banking applications; Harmonisation from native protocols (CS11 AlgoRex, CS6 MP3, SI410 ...
... TCP/IP on Ethernet connectivity for connection to local and remote management stations (MM8000 or MK8000). Transport protocol CMSDL/IP or CEI 79-5 featuring 64bit encryption (FEAL algorithm) for high security banking applications; Harmonisation from native protocols (CS11 AlgoRex, CS6 MP3, SI410 ...
Week 7
... HiperLAN/2 (European standard, 54 Mbps in 5 GHz band) To provide security, most systems use either Wired Equivalent Privacy (WEP), which provides either 40- or 128bit key protection, or a more advanced standard such as WPA (more on security in Chapter Thirteen). Wireless LANs may also be configured ...
... HiperLAN/2 (European standard, 54 Mbps in 5 GHz band) To provide security, most systems use either Wired Equivalent Privacy (WEP), which provides either 40- or 128bit key protection, or a more advanced standard such as WPA (more on security in Chapter Thirteen). Wireless LANs may also be configured ...