Illustrative Examples Threat Mitigation
... A threat is characterized as any circumstance or event with the potential to have an adverse impact on an information system through unauthorized access, destruction, disclosure, modification of data, and/or denial of service (DoS). Threats continue to evolve in sophistication, moving from exploitat ...
... A threat is characterized as any circumstance or event with the potential to have an adverse impact on an information system through unauthorized access, destruction, disclosure, modification of data, and/or denial of service (DoS). Threats continue to evolve in sophistication, moving from exploitat ...
Burst-Polling Based Dynamic Bandwidth Allocation using Adaptive
... Ethernet Passive Optical Networks (EPONs) can be considered one of the best candidates for nextgeneration access networks because of low cost Ethernet equipment, fiber infrastructure, and efficient broadband capabilities [1]. As defined in the IEEE 802.3 standard [2], an EPON uses a multi-point cont ...
... Ethernet Passive Optical Networks (EPONs) can be considered one of the best candidates for nextgeneration access networks because of low cost Ethernet equipment, fiber infrastructure, and efficient broadband capabilities [1]. As defined in the IEEE 802.3 standard [2], an EPON uses a multi-point cont ...
SOCC 2011
... Table 1, the servers can autonomously determine their geographical identities with minimal human intervention. The network administrator needs to only define the geographical identity of a single landmark server. The rest of the servers can determine their geographical identities through the regular ...
... Table 1, the servers can autonomously determine their geographical identities with minimal human intervention. The network administrator needs to only define the geographical identity of a single landmark server. The rest of the servers can determine their geographical identities through the regular ...
Melange: Creating a Functional Internet
... to calculate the length of the options variable-length buffer during packet parsing, and is automatically calculated when generating IPv4 packets using the MPL interfaces. We have also created MPL specifications for a number of additional protocols, including BGP, DNS, SSH, and DHCP (available on-li ...
... to calculate the length of the options variable-length buffer during packet parsing, and is automatically calculated when generating IPv4 packets using the MPL interfaces. We have also created MPL specifications for a number of additional protocols, including BGP, DNS, SSH, and DHCP (available on-li ...
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242
... Figure 2: Classification of Routing Protocols 1.1.1 Table-Driven (Proactive) Routing Protocols These types of protocols are called table driven protocols in which fresh lists of destinations and their routes are maintained by periodic distribution of routing tables throughout the network and this ca ...
... Figure 2: Classification of Routing Protocols 1.1.1 Table-Driven (Proactive) Routing Protocols These types of protocols are called table driven protocols in which fresh lists of destinations and their routes are maintained by periodic distribution of routing tables throughout the network and this ca ...
cissp笔记
... Criteria...........http://doc.xuehai.net/bff69c6183e6980b054e00dcd.html......... ............................7 A Comparison of the Orange Book, ITSEC and Common ...
... Criteria...........http://doc.xuehai.net/bff69c6183e6980b054e00dcd.html......... ............................7 A Comparison of the Orange Book, ITSEC and Common ...
Designing of a semi-automation tool for wireless LAN interoperability testing Jukka Issakainen
... Wireless Local Area Network Access Point (AP) is a device connecting wireless client devices to existing wired network. There are many different brands and models available and their availability varies also geographically. Local laws and regulations have an effect on the product availability not to ...
... Wireless Local Area Network Access Point (AP) is a device connecting wireless client devices to existing wired network. There are many different brands and models available and their availability varies also geographically. Local laws and regulations have an effect on the product availability not to ...
The Pulse Protocol - Department of Computer Science
... On-Demand routes may only work for a short period of time Link State Protocols need to flood every time a link changes These simulations only consider changes from connected not connected (in free space) What about changes in link speed? Reliability? Hard transitions in a real environment? Fast-fa ...
... On-Demand routes may only work for a short period of time Link State Protocols need to flood every time a link changes These simulations only consider changes from connected not connected (in free space) What about changes in link speed? Reliability? Hard transitions in a real environment? Fast-fa ...
Copyright-Compliant Music Sharing in P2P Systems T. Kalker, DHJ
... Small scale trading (e.g. email) cannot be prevented Large-scale illegal trading on other type of network (KaZaa, Gnutella) cannot be prevented unless by legal action ...
... Small scale trading (e.g. email) cannot be prevented Large-scale illegal trading on other type of network (KaZaa, Gnutella) cannot be prevented unless by legal action ...
Distance vector routing updates
... updated due to slow convergence in a changing network. Assume for the remainder of this example that Router C's preferred path to Network 1 is by way of Router B, and the distance from Router C to Network 1 is 3. When Network 1 fails, Router E sends an update to Router A. When Router A sends out ...
... updated due to slow convergence in a changing network. Assume for the remainder of this example that Router C's preferred path to Network 1 is by way of Router B, and the distance from Router C to Network 1 is 3. When Network 1 fails, Router E sends an update to Router A. When Router A sends out ...
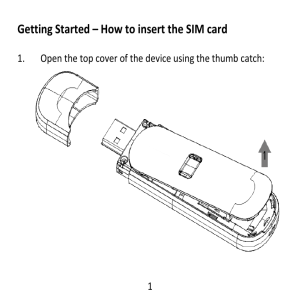
User Guide
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... consume communication resources including bandwidth and power, so that it can be costly. With less frequent information exchanges, these costs decrese but there is more uncertainty about the location of host. Scalable design which works for large size networks requires both routing protocols and res ...
... consume communication resources including bandwidth and power, so that it can be costly. With less frequent information exchanges, these costs decrese but there is more uncertainty about the location of host. Scalable design which works for large size networks requires both routing protocols and res ...
2 Need for coexistence - IEEE 802 LAN/MAN Standards Committee
... In the home use case all device types are expected to use an Internet connection provided by fixed device service from a WSSP. As in the other cases, the backhaul can be provided by any wired or wireless means. The use of sensing-only devices is also likely. TVWS spectrum may also be used by non-IEE ...
... In the home use case all device types are expected to use an Internet connection provided by fixed device service from a WSSP. As in the other cases, the backhaul can be provided by any wired or wireless means. The use of sensing-only devices is also likely. TVWS spectrum may also be used by non-IEE ...
Instruction Manual - Product Resources
... product must not be disposed of with your other household waste. Instead, it is your responsibility to dispose of your waste equipment by handing it over to a designated collection point for the recycling of waste electrical and electronic equipment. The separate collection and recycling of your was ...
... product must not be disposed of with your other household waste. Instead, it is your responsibility to dispose of your waste equipment by handing it over to a designated collection point for the recycling of waste electrical and electronic equipment. The separate collection and recycling of your was ...
Diapositiva 1
... • Permit 802.1q VLAN, jumbo and baby giant frames, VLAN stacking • Have filtering mechanisms like access-lists ...
... • Permit 802.1q VLAN, jumbo and baby giant frames, VLAN stacking • Have filtering mechanisms like access-lists ...
Atom and Molecules
... • There are others like Fahad,who have dubbed MLM schemes as unethical, and guilty of ‘instrumentalising’ relations rooted in love and affection and as such is socially and psychologically unacceptable to most people in our society. • The researchers in this study propose to explore whether such a p ...
... • There are others like Fahad,who have dubbed MLM schemes as unethical, and guilty of ‘instrumentalising’ relations rooted in love and affection and as such is socially and psychologically unacceptable to most people in our society. • The researchers in this study propose to explore whether such a p ...
downloading
... - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
... - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
Update a postal address for your broadband bill
... To connect to Mobile Broadband, make sure your Broadband Complete is plugged in and turned on and then put the Vodem stick into the slot on your Vodafone Broadband Complete. When the device is detected by the device you will see this screen below and the indicator on the front of the device will lig ...
... To connect to Mobile Broadband, make sure your Broadband Complete is plugged in and turned on and then put the Vodem stick into the slot on your Vodafone Broadband Complete. When the device is detected by the device you will see this screen below and the indicator on the front of the device will lig ...
An Efficient Feature Reduction Comparison of Machine Learning
... available data set is KDD data set for the purpose of experiment for intrusion detection.KDD data set [5] contain 42 attributes. The classes in KDD99 [6] dataset can be categorized into five main classes such as one normal class and four main intrusion classes. Data mining is a collection of techniq ...
... available data set is KDD data set for the purpose of experiment for intrusion detection.KDD data set [5] contain 42 attributes. The classes in KDD99 [6] dataset can be categorized into five main classes such as one normal class and four main intrusion classes. Data mining is a collection of techniq ...
Chakchai-Exploration_Routing_Chapter_5
... LAN links -Public IP addresses are used on WAN links -Loopback interfaces : LoX (These are virtual interfaces that can be pinged and added to routing table.) ...
... LAN links -Public IP addresses are used on WAN links -Loopback interfaces : LoX (These are virtual interfaces that can be pinged and added to routing table.) ...