PowerPoint Title
... coverage over some relatively large contiguous geographic serving area. vertically-integrated, top-down, service-provider approach to delivering wireless Internet access ...
... coverage over some relatively large contiguous geographic serving area. vertically-integrated, top-down, service-provider approach to delivering wireless Internet access ...
Chapter 12 Summary: The Internet and How It Works
... The Internet began as a research network funded by the U.S. Defense Department in 1969. ...
... The Internet began as a research network funded by the U.S. Defense Department in 1969. ...
technological change towards digital libraries
... • Libraries have become heavily involved in – building web site – buying access to toll-gated web sites – building resources that are indirectly available on the Web • Web OPACs ...
... • Libraries have become heavily involved in – building web site – buying access to toll-gated web sites – building resources that are indirectly available on the Web • Web OPACs ...
Lecture 29 - Electrical and Computer Engineering
... • 1990 1 millionth host attached to “the Internet” • 1995 NSFnet is decommissioned, and replaced by the “Network Access Point” (NAP) architecture • 1995+ Rapid growth of Internet usage by businesses, organizations, government and individuals (E-mail, WWW, E-commerce) Copyright 1999, S.D. Personick. ...
... • 1990 1 millionth host attached to “the Internet” • 1995 NSFnet is decommissioned, and replaced by the “Network Access Point” (NAP) architecture • 1995+ Rapid growth of Internet usage by businesses, organizations, government and individuals (E-mail, WWW, E-commerce) Copyright 1999, S.D. Personick. ...
$doc.title
... – Can use both collisions to construct original packets – Reduce effecVve error rate significantly ...
... – Can use both collisions to construct original packets – Reduce effecVve error rate significantly ...
Basic Operations of the SIP-Based Mobile Network
... • A SIP-based mobile network architecture to support networking services on the roads – Multiple wireless interfaces – Dynamic bandwidth to internal users – By interpreting SIP signaling, the RM and CAC mechanisms inside the SIP-MNG can guarantee QoS for users – a push mechanism to allow the SIP-MNG ...
... • A SIP-based mobile network architecture to support networking services on the roads – Multiple wireless interfaces – Dynamic bandwidth to internal users – By interpreting SIP signaling, the RM and CAC mechanisms inside the SIP-MNG can guarantee QoS for users – a push mechanism to allow the SIP-MNG ...
Slide 1
... that have a fast connection to the Internet via cable, satellite or DSL, the router can function as a hardware firewall. ...
... that have a fast connection to the Internet via cable, satellite or DSL, the router can function as a hardware firewall. ...
physcial_sci_networks_part2
... – Every host on the bus could see and capture every transmission made • Trivial to recover passwords, web pages you viewed ...
... – Every host on the bus could see and capture every transmission made • Trivial to recover passwords, web pages you viewed ...
Document
... Figure 15.2 A small example of the physical structure that remains hidden inside the Internet. Each computer attaches to a single network; routers interconnect the networks. ...
... Figure 15.2 A small example of the physical structure that remains hidden inside the Internet. Each computer attaches to a single network; routers interconnect the networks. ...
Chapter 7
... telephone, video, and data communication within a single network, offering convenience and flexibility not possible with separate infrastructures ...
... telephone, video, and data communication within a single network, offering convenience and flexibility not possible with separate infrastructures ...
lect2_3
... Lecture 2 CSIT435 Chapter 1 goal: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
... Lecture 2 CSIT435 Chapter 1 goal: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
View File - University of Engineering and Technology, Taxila
... Data is bursty, whereas voice is continuous ...
... Data is bursty, whereas voice is continuous ...
CS 4251: Computer Networking II
... • How to write programs that allow hosts to communicate with one another? • How do hosts “bootstrap” when they get onto the network? • What’s a “router”? What’s inside of it, how does it work, how does it know where to send your traffic? ...
... • How to write programs that allow hosts to communicate with one another? • How do hosts “bootstrap” when they get onto the network? • What’s a “router”? What’s inside of it, how does it work, how does it know where to send your traffic? ...
What is the Internet?
... A Web page is specially coded document that can contain text, graphics, videos, and sounds A Web site consists of one or more Web pages located on a Web server ...
... A Web page is specially coded document that can contain text, graphics, videos, and sounds A Web site consists of one or more Web pages located on a Web server ...
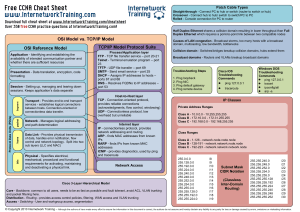
CCNA cheat sheet - Internetwork Training
... overhead but unreliable Internet layer IP - connectionless protocol, provides network addressing and routing ARP - finds MAC addresses from known IPs RARP - finds IPs from known MAC addresses ICMP - provides diagnostics, used by ping and traceroute ...
... overhead but unreliable Internet layer IP - connectionless protocol, provides network addressing and routing ARP - finds MAC addresses from known IPs RARP - finds IPs from known MAC addresses ICMP - provides diagnostics, used by ping and traceroute ...
Chapter 5
... • Protocol: a standard means for coordinating an activity between two or more entities • Communications protocol: a means for coordinating activity between two or more communicating computers – The communication protocol is broken into levels of layers – Two machines must agree upon and follow the p ...
... • Protocol: a standard means for coordinating an activity between two or more entities • Communications protocol: a means for coordinating activity between two or more communicating computers – The communication protocol is broken into levels of layers – Two machines must agree upon and follow the p ...
Chapter6
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” cell towers 802.11 access points ...
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” cell towers 802.11 access points ...
ACCESS NETWORKING - CERN Computing Seminars
... for point to point (or multi-point) developed (modulation, line, source and channel coding) • First stage of switching technology (FDMA, TDMA, Time and space switch) • Second stage of switching technology (packet switching, Network management, optical fibers multiple services (Multi-media - voice, d ...
... for point to point (or multi-point) developed (modulation, line, source and channel coding) • First stage of switching technology (FDMA, TDMA, Time and space switch) • Second stage of switching technology (packet switching, Network management, optical fibers multiple services (Multi-media - voice, d ...
Ch 5 Network Communication
... and virtual libraries. (http://www.Internet2.edu) Next Generation Internet (NGI) Government sponsored initiative aimed at creating an Internet that is fast, always on, everywhere, natural, intelligent, easy and trusted. ...
... and virtual libraries. (http://www.Internet2.edu) Next Generation Internet (NGI) Government sponsored initiative aimed at creating an Internet that is fast, always on, everywhere, natural, intelligent, easy and trusted. ...