... Wi-Fi is the commercial name for the technologies built on the standard of communication 802.11, utilized for local wireless networks with similar speeds to those of Ethernet. Wi-Fi support and compatibility are provided at this moment by many, if not all, new hardware mobile devices, routers and op ...
firstclass
... Packets Way information moves across the wire Packets can carry data or protocol/control information only Difference between “packet” and “cell” ...
... Packets Way information moves across the wire Packets can carry data or protocol/control information only Difference between “packet” and “cell” ...
Chapter 1-3
... Programmer does not need to understand network technologies Network facilities are accessed through an Application Program Interface ...
... Programmer does not need to understand network technologies Network facilities are accessed through an Application Program Interface ...
Document
... modem is a type of modem that provides access to a data signal sent over the cable television infrastructure. Cable modems are primarily used to deliver broadband Internet access, taking advantage of unused bandwidth on a cable television network ADSL modem or DSL modem is a device used to connect ...
... modem is a type of modem that provides access to a data signal sent over the cable television infrastructure. Cable modems are primarily used to deliver broadband Internet access, taking advantage of unused bandwidth on a cable television network ADSL modem or DSL modem is a device used to connect ...
Connected Devices Interfacing (CDI)
... services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of the physical network resources, as well as the capability to control them (up to certain limitations given by the physical resour ...
... services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of the physical network resources, as well as the capability to control them (up to certain limitations given by the physical resour ...
The Next Generation Wireless
... Airwave Management Platform Allows to monitor, configure and manage access points Has rogue detection capabilities Collects statistics Supports multiple vendors/platforms ...
... Airwave Management Platform Allows to monitor, configure and manage access points Has rogue detection capabilities Collects statistics Supports multiple vendors/platforms ...
Assignment 3 - Network Components
... What is a Network Gateway? A network gateway is an internetworking system capable of joining together two networks that use different base protocols. A network gateway can be implemented completely in software, completely in hardware, or as a combination of both. Depending on the types of protocols ...
... What is a Network Gateway? A network gateway is an internetworking system capable of joining together two networks that use different base protocols. A network gateway can be implemented completely in software, completely in hardware, or as a combination of both. Depending on the types of protocols ...
Wireless Networks
... time). WEP does not provide key management. • Cryptographic keys are short. • No user authentication occurs – only devices are authenticated. A stolen device can access the ...
... time). WEP does not provide key management. • Cryptographic keys are short. • No user authentication occurs – only devices are authenticated. A stolen device can access the ...
PPT
... • what’s the Internet • what’s a protocol? • network edge today • network core • access net, physical media • performance: loss, delay • protocol layers, service models • backbones, NAPs, ISPs • history • ATM network ...
... • what’s the Internet • what’s a protocol? • network edge today • network core • access net, physical media • performance: loss, delay • protocol layers, service models • backbones, NAPs, ISPs • history • ATM network ...
Network Traversal
... • “Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data. Spear phishing attempts are not typically initiated by "random hackers" but are more likely to be conducted by perpetrators out for financial gain, trade secr ...
... • “Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data. Spear phishing attempts are not typically initiated by "random hackers" but are more likely to be conducted by perpetrators out for financial gain, trade secr ...
Backbone: the main connecting cable that runs from one end of the
... and the client. IP provides the service of communicable unique global addressing amongst computers. UDP does not establish a connection to send a message. It merely sends the message to the address it was given and forgets about it. UDP does not offer such retransmission services. A transport layer ...
... and the client. IP provides the service of communicable unique global addressing amongst computers. UDP does not establish a connection to send a message. It merely sends the message to the address it was given and forgets about it. UDP does not offer such retransmission services. A transport layer ...
A Configuration Protocol for Embedded Networked Devices on Secure Wireless Networks
... implement additional user interfaces, such as a USB connection or wired Ethernet, to facilitate initial network configuration – which adds cost and complexity to the embedded devices. In this paper, we present a new protocol that allows a wireless embedded networked device to be easily configured fo ...
... implement additional user interfaces, such as a USB connection or wired Ethernet, to facilitate initial network configuration – which adds cost and complexity to the embedded devices. In this paper, we present a new protocol that allows a wireless embedded networked device to be easily configured fo ...
Internetworking - University of Maine System
... Universal Service is the concept that any device on any network can communicate with any arbitrary device on another network. The Internet is a heterogeneous environment, with multiple, independent network topologies. In LANs, we have seen that heterogeneous technologies cannot interconnect without ...
... Universal Service is the concept that any device on any network can communicate with any arbitrary device on another network. The Internet is a heterogeneous environment, with multiple, independent network topologies. In LANs, we have seen that heterogeneous technologies cannot interconnect without ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... Computers can still broadcast messages to all other computers on the network ...
... Computers can still broadcast messages to all other computers on the network ...
weather parameters_IoT
... The Internet of Things (IoT) is a recent communication, in which a network connects all things to the internet for communicating through the sensing devices with suitable protocols, and exchange data with each other by using wireless sensor networks. Embedded systems play a vital role in IoT; these ...
... The Internet of Things (IoT) is a recent communication, in which a network connects all things to the internet for communicating through the sensing devices with suitable protocols, and exchange data with each other by using wireless sensor networks. Embedded systems play a vital role in IoT; these ...
13707579013302_CIS 202 TC,NW & WT-1
... radio signals to link two or more computers within a geographically limited area, generally one building or a group of buildings. A networked office building, school, or home usually contains a single LAN. The linked computers are called workstations. • Wide area network (WAN) A computer network tha ...
... radio signals to link two or more computers within a geographically limited area, generally one building or a group of buildings. A networked office building, school, or home usually contains a single LAN. The linked computers are called workstations. • Wide area network (WAN) A computer network tha ...
QoS Guarantee in Wirless Network
... – The data is collected by portable devices, and may stay (and be searched) on the devices: • Urban sensing (vehicle, people) – Multiple hops - to other mobiles of to the Access Point – This creates new challenges • Distributed index (ie, publish/subscribe) to find the data • Data sharing among mobi ...
... – The data is collected by portable devices, and may stay (and be searched) on the devices: • Urban sensing (vehicle, people) – Multiple hops - to other mobiles of to the Access Point – This creates new challenges • Distributed index (ie, publish/subscribe) to find the data • Data sharing among mobi ...
Business to Business Wireless E
... meters automatically. Thus generating substantial cost savings by eliminating the need to send someone to every house to do the job. B2B Wireless E-Commerce also encompasses the wireless point of sales (POS). This will provide an industry-specific example of how new value can be created by improving ...
... meters automatically. Thus generating substantial cost savings by eliminating the need to send someone to every house to do the job. B2B Wireless E-Commerce also encompasses the wireless point of sales (POS). This will provide an industry-specific example of how new value can be created by improving ...
network protocols
... that determines the next network point to which a packet should be forwarded toward its destination. • The router is connected to at least two networks and decides which way to send each information packet based on its current understanding of the state of the networks it is connected to. • May crea ...
... that determines the next network point to which a packet should be forwarded toward its destination. • The router is connected to at least two networks and decides which way to send each information packet based on its current understanding of the state of the networks it is connected to. • May crea ...
No Slide Title
... governs Internet traffic is increasingly overloaded. In this example, A must take a complex route to site B, contending with cross traffic all along the way. ...
... governs Internet traffic is increasingly overloaded. In this example, A must take a complex route to site B, contending with cross traffic all along the way. ...
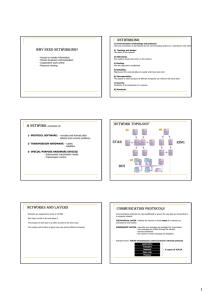
WHY NEED NETWORKING? NETWORKING NETWORK
... single VLAN, they can share resources and bandwidth as if they were connected to the same segment. ...
... single VLAN, they can share resources and bandwidth as if they were connected to the same segment. ...
Enabling Simultaneous Connections to Multiple Wireless Networks
... Intermediate layer between IP and MAC: • Maintains a virtual instance of the wireless card per network • Multiplexes across networks, activates one virtual instance at a time. • Buffers packets for inactive networks ...
... Intermediate layer between IP and MAC: • Maintains a virtual instance of the wireless card per network • Multiplexes across networks, activates one virtual instance at a time. • Buffers packets for inactive networks ...
Large-scale Wireless Networks: Stochastic Geometry and Ordering
... limited cases, it is of interest to compare network interference using stochastic orders, for two different point processes with different fading or path-loss scenarios between the interferers and the receiver. In this dissertation, conditions on the fading distribution and path-loss model are given ...
... limited cases, it is of interest to compare network interference using stochastic orders, for two different point processes with different fading or path-loss scenarios between the interferers and the receiver. In this dissertation, conditions on the fading distribution and path-loss model are given ...
Data Transmission Review
... 3. CSMA/CD is known as a _____________________ access method because computers on the network compete for an opportunity to send data. 4. With more traffic on a CSMA/CD network, _______________ tend to increase, slowing the network down. 5. With the token-passing access method, only one computer at ...
... 3. CSMA/CD is known as a _____________________ access method because computers on the network compete for an opportunity to send data. 4. With more traffic on a CSMA/CD network, _______________ tend to increase, slowing the network down. 5. With the token-passing access method, only one computer at ...
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE)
... design tradeoffs require further study. This includes coherent vs. non-coherent techniques, complex field vs. finite field coding, pilot aided vs. (semi)blind algorithms, and diversity vs. achievable rate. There is a potential to improve network performance if multiuser diversity can be ploited. Mul ...
... design tradeoffs require further study. This includes coherent vs. non-coherent techniques, complex field vs. finite field coding, pilot aided vs. (semi)blind algorithms, and diversity vs. achievable rate. There is a potential to improve network performance if multiuser diversity can be ploited. Mul ...